Inhaltsverzeichnis
squid CentOS 7
 Squid ist ein „caching proxy“ welcher z.B. die Protokolle HTTP, HTTPS, FTP, uvm. unterstützt. Durch den Einsatz eines Proxy-Servers kann eine Reduzierung des Bandbreitenverbrauchs und der Ladezeiten von Internetseiten erreicht werden. Ein weiterer sehr wichtiger Punkt ist die Möglichkeit der Zugriffsbeschränkung und der Authentifizierung beim Zugriff auf das Internet aus dem lokalen Netzwerk.
Squid ist ein „caching proxy“ welcher z.B. die Protokolle HTTP, HTTPS, FTP, uvm. unterstützt. Durch den Einsatz eines Proxy-Servers kann eine Reduzierung des Bandbreitenverbrauchs und der Ladezeiten von Internetseiten erreicht werden. Ein weiterer sehr wichtiger Punkt ist die Möglichkeit der Zugriffsbeschränkung und der Authentifizierung beim Zugriff auf das Internet aus dem lokalen Netzwerk.

| Beschreibung | Externer Link |
|---|---|
| Homepage | http://www.squid-cache.org/ |
| Konfiguration | http://www.squid-cache.org/Doc/config/ http://wiki.squid-cache.org/ConfigExamples |
| Wiki | http://wiki.squid-cache.org/ |
| FAQ | http://wiki.squid-cache.org/SquidFaq |
| Besonderheiten Version 3.3.8 | Externer Link |
|---|---|
| Caching Dynamic Content | http://wiki.squid-cache.org/ConfigExamples/DynamicContent |
Ab hier werden zur Ausführung nachfolgender Befehle root-Rechte benötigt. Um der Benutzer root zu werden, melden Sie sich bitte als root-Benutzer am System an, oder wechseln mit nachfolgendem Befehl zum Benutzer root:
$ su - Password:
Überblick
Im nachfolgenden soll die Konfiguration von Squid als Proxy-Server für ein privates Netzwerk durchgeführt werden. Nachfolgende Netze spielen dabei eine Rolle:
- IDMZ - Domain: idmz.tachtler.net - IP-Adressbereich: 192.168.0.0/24
- EDMZ - Domain: edmz.tachtler.net - IP-Adressbereich: 192.168.1.0/24
- Intranet - Domain: intra.tachtler.net - IP-Adressbereich: 192.168.2.0/24

Neben den vielen eindeutigen Vorteilen eines Cache-Proxy, gibt es jedoch auch gute Gründe, die gegen einen Cache-Proxy sprechen. In einigen Fällen kann es durchaus sinnvoll sein, auf eine Cache-Funktionalität zu verzichten.
Vorteile eines Cache-Proxy's:
- Beschleunigung - Da die Antwortzeiten des Proxys aus dem eigenen Cache meist deutlich kürzer sind - abgesehen von Webservern im lokalen Netz, kann je nach Entfernung und Anbindung zum Webserver die Antwortzeit aus dem Cache um den Faktor 2 bis 100 schneller sein, als direkte Zugriffe.
- Bandbreite - Durch die Datenhaltung im Cache werden viele Anfragen an den Zielserver überflüssig. Der Proxy liefert die Antwort aus dem Cache, anstatt sie über eine (externe) Verbindung zu holen.
- Verfügbarkeit - Bei unsicheren Verbindungen oder schlechter Verfügbarkeit externer Webserver kann ein Proxyserver u.U. auch zu einer Erhöhung der Verfügbarkeit dieser Inhalte führen. Wurde ein Objekt einmal im Cache abgelegt, kann es bei Ausfall der Verbindung noch aus dem Cache geliefert werden.
Nachteile eines Cache-Proxy's:
- Kosten eines Cache - Ein Cache braucht eine entsprechende Speicherkapazität, sowohl auf der Festplatte sowie auch im Hauptspeicher.
- Verzögerungen durch einen Cache - Ein Cache spart Ladezeit. Nutzen Sie den Proxy nur für Webserver in einem lokalen Netz mit guter Bandbreite, kann dieser Effekt unter sehr ungünstigen Umständen sogar zu geringfügig längeren Antwortzeiten führen als bei einem direkten Zugriff.
- Aktualität - Die Aktualität, kann ein starkes Argument gegen einen Cache sein. Teilweise kann es zur Auslieferung veralteter Objekte kommen. Ist eine laufende Aktualität aller Informationen ein zwingendes Argument, ist evtl. von einem Cache abzuraten.
- Rechtliche Probleme - Je nach aktueller Rechtslage können Probleme in Bereichen wie Urheberrecht auftreten.


Voraussetzungen
Als Voraussetzung für die Installation von Squid sind folgende Komponenten erforderlich:
- Lauffähiger Web-Server z.B. Apache HTTP Server
- Siehe auch den internen Link: Apache HTTP Server CentOS 7
Nachfolgende rpm-Pakete sind als Abhängigkeit erforderlich und werden ebenfalls benötigt:
Installation
Zur Installation eines Squid als Proxy-Server wird nachfolgendes Paket benötigt:
installiert werden.
Mit nachfolgendem Befehl, wird das Pakete squid installiert:
# yum install squid Loaded plugins: changelog, priorities base | 3.6 kB 00:00 epel | 4.4 kB 00:00 extras | 3.4 kB 00:00 updates | 3.4 kB 00:00 40 packages excluded due to repository priority protections Resolving Dependencies --> Running transaction check ---> Package squid.x86_64 7:3.3.8-12.el7_0 will be installed --> Processing Dependency: perl(Digest::MD5) for package: 7:squid-3.3.8-12.el7_0.x86_64 --> Processing Dependency: perl(Data::Dumper) for package: 7:squid-3.3.8-12.el7_0.x86_64 --> Processing Dependency: perl(DBI) for package: 7:squid-3.3.8-12.el7_0.x86_64 --> Processing Dependency: libltdl.so.7()(64bit) for package: 7:squid-3.3.8-12.el7_0.x86_64 --> Processing Dependency: libecap.so.2()(64bit) for package: 7:squid-3.3.8-12.el7_0.x86_64 --> Running transaction check ---> Package libecap.x86_64 0:0.2.0-8.el7 will be installed ---> Package libtool-ltdl.x86_64 0:2.4.2-20.el7 will be installed ---> Package perl-DBI.x86_64 0:1.627-4.el7 will be installed --> Processing Dependency: perl(RPC::PlServer) >= 0.2001 for package: perl-DBI-1.627-4.el7.x86_64 --> Processing Dependency: perl(RPC::PlClient) >= 0.2000 for package: perl-DBI-1.627-4.el7.x86_64 ---> Package perl-Data-Dumper.x86_64 0:2.145-3.el7 will be installed ---> Package perl-Digest-MD5.x86_64 0:2.52-3.el7 will be installed --> Processing Dependency: perl(Digest::base) >= 1.00 for package: perl-Digest-MD5-2.52-3.el7.x86_64 --> Running transaction check ---> Package perl-Digest.noarch 0:1.17-245.el7 will be installed ---> Package perl-PlRPC.noarch 0:0.2020-14.el7 will be installed --> Processing Dependency: perl(Net::Daemon) >= 0.13 for package: perl-PlRPC-0.2020-14.el7.noarch --> Processing Dependency: perl(Net::Daemon::Test) for package: perl-PlRPC-0.2020-14.el7.noarch --> Processing Dependency: perl(Net::Daemon::Log) for package: perl-PlRPC-0.2020-14.el7.noarch --> Processing Dependency: perl(Compress::Zlib) for package: perl-PlRPC-0.2020-14.el7.noarch --> Running transaction check ---> Package perl-IO-Compress.noarch 0:2.061-2.el7 will be installed --> Processing Dependency: perl(Compress::Raw::Zlib) >= 2.061 for package: perl-IO-Compress-2.061-2.el7.noarch --> Processing Dependency: perl(Compress::Raw::Bzip2) >= 2.061 for package: perl-IO-Compress-2.061-2.el7.noarch ---> Package perl-Net-Daemon.noarch 0:0.48-5.el7 will be installed --> Running transaction check ---> Package perl-Compress-Raw-Bzip2.x86_64 0:2.061-3.el7 will be installed ---> Package perl-Compress-Raw-Zlib.x86_64 1:2.061-4.el7 will be installed --> Finished Dependency Resolution Changes in packages about to be updated: Dependencies Resolved ================================================================================ Package Arch Version Repository Size ================================================================================ Installing: squid x86_64 7:3.3.8-12.el7_0 updates 2.6 M Installing for dependencies: libecap x86_64 0.2.0-8.el7 base 20 k libtool-ltdl x86_64 2.4.2-20.el7 base 49 k perl-Compress-Raw-Bzip2 x86_64 2.061-3.el7 base 32 k perl-Compress-Raw-Zlib x86_64 1:2.061-4.el7 base 57 k perl-DBI x86_64 1.627-4.el7 base 802 k perl-Data-Dumper x86_64 2.145-3.el7 base 47 k perl-Digest noarch 1.17-245.el7 base 23 k perl-Digest-MD5 x86_64 2.52-3.el7 base 30 k perl-IO-Compress noarch 2.061-2.el7 base 260 k perl-Net-Daemon noarch 0.48-5.el7 base 51 k perl-PlRPC noarch 0.2020-14.el7 base 36 k Transaction Summary ================================================================================ Install 1 Package (+11 Dependent packages) Total download size: 3.9 M Installed size: 12 M Is this ok [y/d/N]: y Downloading packages: (1/12): libtool-ltdl-2.4.2-20.el7.x86_64.rpm | 49 kB 00:00 (2/12): libecap-0.2.0-8.el7.x86_64.rpm | 20 kB 00:00 (3/12): perl-Compress-Raw-Bzip2-2.061-3.el7.x86_64.rpm | 32 kB 00:00 (4/12): perl-Compress-Raw-Zlib-2.061-4.el7.x86_64.rpm | 57 kB 00:00 (5/12): perl-DBI-1.627-4.el7.x86_64.rpm | 802 kB 00:00 (6/12): perl-Data-Dumper-2.145-3.el7.x86_64.rpm | 47 kB 00:00 (7/12): perl-Digest-MD5-2.52-3.el7.x86_64.rpm | 30 kB 00:00 (8/12): perl-Digest-1.17-245.el7.noarch.rpm | 23 kB 00:00 (9/12): perl-IO-Compress-2.061-2.el7.noarch.rpm | 260 kB 00:00 (10/12): perl-Net-Daemon-0.48-5.el7.noarch.rpm | 51 kB 00:00 (11/12): perl-PlRPC-0.2020-14.el7.noarch.rpm | 36 kB 00:00 (12/12): squid-3.3.8-12.el7_0.x86_64.rpm | 2.6 MB 00:00 -------------------------------------------------------------------------------- Total 4.6 MB/s | 3.9 MB 00:00 Running transaction check Running transaction test Transaction test succeeded Running transaction Installing : perl-Data-Dumper-2.145-3.el7.x86_64 1/12 Installing : perl-Net-Daemon-0.48-5.el7.noarch 2/12 Installing : perl-Digest-1.17-245.el7.noarch 3/12 Installing : perl-Digest-MD5-2.52-3.el7.x86_64 4/12 Installing : 1:perl-Compress-Raw-Zlib-2.061-4.el7.x86_64 5/12 Installing : libtool-ltdl-2.4.2-20.el7.x86_64 6/12 Installing : libecap-0.2.0-8.el7.x86_64 7/12 Installing : perl-Compress-Raw-Bzip2-2.061-3.el7.x86_64 8/12 Installing : perl-IO-Compress-2.061-2.el7.noarch 9/12 Installing : perl-PlRPC-0.2020-14.el7.noarch 10/12 Installing : perl-DBI-1.627-4.el7.x86_64 11/12 Installing : 7:squid-3.3.8-12.el7_0.x86_64 12/12 Verifying : perl-Compress-Raw-Bzip2-2.061-3.el7.x86_64 1/12 Verifying : 7:squid-3.3.8-12.el7_0.x86_64 2/12 Verifying : libecap-0.2.0-8.el7.x86_64 3/12 Verifying : perl-Data-Dumper-2.145-3.el7.x86_64 4/12 Verifying : perl-Digest-MD5-2.52-3.el7.x86_64 5/12 Verifying : perl-IO-Compress-2.061-2.el7.noarch 6/12 Verifying : libtool-ltdl-2.4.2-20.el7.x86_64 7/12 Verifying : 1:perl-Compress-Raw-Zlib-2.061-4.el7.x86_64 8/12 Verifying : perl-Digest-1.17-245.el7.noarch 9/12 Verifying : perl-DBI-1.627-4.el7.x86_64 10/12 Verifying : perl-Net-Daemon-0.48-5.el7.noarch 11/12 Verifying : perl-PlRPC-0.2020-14.el7.noarch 12/12 Installed: squid.x86_64 7:3.3.8-12.el7_0 Dependency Installed: libecap.x86_64 0:0.2.0-8.el7 libtool-ltdl.x86_64 0:2.4.2-20.el7 perl-Compress-Raw-Bzip2.x86_64 0:2.061-3.el7 perl-Compress-Raw-Zlib.x86_64 1:2.061-4.el7 perl-DBI.x86_64 0:1.627-4.el7 perl-Data-Dumper.x86_64 0:2.145-3.el7 perl-Digest.noarch 0:1.17-245.el7 perl-Digest-MD5.x86_64 0:2.52-3.el7 perl-IO-Compress.noarch 0:2.061-2.el7 perl-Net-Daemon.noarch 0:0.48-5.el7 perl-PlRPC.noarch 0:0.2020-14.el7 Complete!
Mit nachfolgendem Befehl kann überprüft werden, welche Inhalte mit den Paket squid installiert wurden.
# rpm -qil squid Name : squid Epoch : 7 Version : 3.3.8 Release : 12.el7_0 Architecture: x86_64 Install Date: Wed 04 Feb 2015 03:32:13 PM CET Group : System Environment/Daemons Size : 8958283 License : GPLv2+ and (LGPLv2+ and MIT and BSD and Public Domain) Signature : RSA/SHA256, Thu 04 Sep 2014 12:39:20 AM CEST, Key ID 24c6a8a7f4a80eb5 Source RPM : squid-3.3.8-12.el7_0.src.rpm Build Date : Wed 03 Sep 2014 09:40:33 PM CEST Build Host : worker1.bsys.centos.org Relocations : (not relocatable) Packager : CentOS BuildSystem <http://bugs.centos.org> Vendor : CentOS URL : http://www.squid-cache.org Summary : The Squid proxy caching server Description : Squid is a high-performance proxy caching server for Web clients, supporting FTP, gopher, and HTTP data objects. Unlike traditional caching software, Squid handles all requests in a single, non-blocking, I/O-driven process. Squid keeps meta data and especially hot objects cached in RAM, caches DNS lookups, supports non-blocking DNS lookups, and implements negative caching of failed requests. Squid consists of a main server program squid, a Domain Name System lookup program (dnsserver), a program for retrieving FTP data (ftpget), and some management and client tools. /etc/NetworkManager/dispatcher.d/20-squid /etc/httpd/conf.d/squid.conf /etc/logrotate.d/squid /etc/pam.d/squid /etc/squid /etc/squid/cachemgr.conf /etc/squid/cachemgr.conf.default /etc/squid/errorpage.css /etc/squid/errorpage.css.default /etc/squid/mime.conf /etc/squid/mime.conf.default /etc/squid/msntauth.conf /etc/squid/msntauth.conf.default /etc/squid/squid.conf /etc/squid/squid.conf.default /etc/sysconfig/squid /usr/bin/purge /usr/bin/squidclient /usr/lib/systemd/system/squid.service /usr/lib64/squid /usr/lib64/squid/basic_db_auth /usr/lib64/squid/basic_getpwnam_auth /usr/lib64/squid/basic_ldap_auth /usr/lib64/squid/basic_msnt_auth /usr/lib64/squid/basic_msnt_multi_domain_auth /usr/lib64/squid/basic_ncsa_auth /usr/lib64/squid/basic_nis_auth /usr/lib64/squid/basic_pam_auth /usr/lib64/squid/basic_pop3_auth /usr/lib64/squid/basic_radius_auth /usr/lib64/squid/basic_sasl_auth /usr/lib64/squid/basic_smb_auth /usr/lib64/squid/basic_smb_auth.sh /usr/lib64/squid/cachemgr.cgi /usr/lib64/squid/digest_edirectory_auth /usr/lib64/squid/digest_file_auth /usr/lib64/squid/digest_ldap_auth /usr/lib64/squid/diskd /usr/lib64/squid/ext_file_userip_acl /usr/lib64/squid/ext_ldap_group_acl /usr/lib64/squid/ext_session_acl /usr/lib64/squid/ext_time_quota_acl /usr/lib64/squid/ext_unix_group_acl /usr/lib64/squid/ext_wbinfo_group_acl /usr/lib64/squid/helper-mux.pl /usr/lib64/squid/log_db_daemon /usr/lib64/squid/log_file_daemon /usr/lib64/squid/negotiate_kerberos_auth /usr/lib64/squid/negotiate_kerberos_auth_test /usr/lib64/squid/ntlm_fake_auth /usr/lib64/squid/ntlm_smb_lm_auth /usr/lib64/squid/ssl_crtd /usr/lib64/squid/unlinkd /usr/lib64/squid/url_fake_rewrite /usr/lib64/squid/url_fake_rewrite.sh /usr/libexec/squid /usr/libexec/squid/cache_swap.sh /usr/sbin/squid /usr/share/doc/squid-3.3.8 /usr/share/doc/squid-3.3.8/COPYING /usr/share/doc/squid-3.3.8/COPYRIGHT /usr/share/doc/squid-3.3.8/ChangeLog /usr/share/doc/squid-3.3.8/QUICKSTART /usr/share/doc/squid-3.3.8/README /usr/share/doc/squid-3.3.8/rredir.c /usr/share/doc/squid-3.3.8/rredir.pl /usr/share/doc/squid-3.3.8/squid.conf.documented /usr/share/doc/squid-3.3.8/url-normalizer.pl /usr/share/doc/squid-3.3.8/user-agents.pl /usr/share/man/man1/squidclient.1.gz /usr/share/man/man8/basic_db_auth.8.gz /usr/share/man/man8/basic_getpwnam_auth.8.gz /usr/share/man/man8/basic_ldap_auth.8.gz /usr/share/man/man8/basic_ncsa_auth.8.gz /usr/share/man/man8/basic_pam_auth.8.gz /usr/share/man/man8/basic_radius_auth.8.gz /usr/share/man/man8/basic_sasl_auth.8.gz /usr/share/man/man8/cachemgr.cgi.8.gz /usr/share/man/man8/digest_file_auth.8.gz /usr/share/man/man8/ext_file_userip_acl.8.gz /usr/share/man/man8/ext_ldap_group_acl.8.gz /usr/share/man/man8/ext_session_acl.8.gz /usr/share/man/man8/ext_time_quota_acl.8.gz /usr/share/man/man8/ext_unix_group_acl.8.gz /usr/share/man/man8/ext_wbinfo_group_acl.8.gz /usr/share/man/man8/log_db_daemon.8.gz /usr/share/man/man8/negotiate_kerberos_auth.8.gz /usr/share/man/man8/squid.8.gz /usr/share/snmp/mibs/SQUID-MIB.txt /usr/share/squid /usr/share/squid/errors /usr/share/squid/errors/COPYRIGHT /usr/share/squid/errors/TRANSLATORS /usr/share/squid/errors/af /usr/share/squid/errors/af/ERR_ACCESS_DENIED /usr/share/squid/errors/af/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/af/ERR_AGENT_CONFIGURE /usr/share/squid/errors/af/ERR_AGENT_WPAD /usr/share/squid/errors/af/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/af/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/af/ERR_CANNOT_FORWARD /usr/share/squid/errors/af/ERR_CONFLICT_HOST /usr/share/squid/errors/af/ERR_CONNECT_FAIL /usr/share/squid/errors/af/ERR_DIR_LISTING /usr/share/squid/errors/af/ERR_DNS_FAIL /usr/share/squid/errors/af/ERR_ESI /usr/share/squid/errors/af/ERR_FORWARDING_DENIED /usr/share/squid/errors/af/ERR_FTP_DISABLED /usr/share/squid/errors/af/ERR_FTP_FAILURE /usr/share/squid/errors/af/ERR_FTP_FORBIDDEN /usr/share/squid/errors/af/ERR_FTP_NOT_FOUND /usr/share/squid/errors/af/ERR_FTP_PUT_CREATED /usr/share/squid/errors/af/ERR_FTP_PUT_ERROR /usr/share/squid/errors/af/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/af/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/af/ERR_GATEWAY_FAILURE /usr/share/squid/errors/af/ERR_ICAP_FAILURE /usr/share/squid/errors/af/ERR_INVALID_REQ /usr/share/squid/errors/af/ERR_INVALID_RESP /usr/share/squid/errors/af/ERR_INVALID_URL /usr/share/squid/errors/af/ERR_LIFETIME_EXP /usr/share/squid/errors/af/ERR_NO_RELAY /usr/share/squid/errors/af/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/af/ERR_PRECONDITION_FAILED /usr/share/squid/errors/af/ERR_READ_ERROR /usr/share/squid/errors/af/ERR_READ_TIMEOUT /usr/share/squid/errors/af/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/af/ERR_SHUTTING_DOWN /usr/share/squid/errors/af/ERR_SOCKET_FAILURE /usr/share/squid/errors/af/ERR_TOO_BIG /usr/share/squid/errors/af/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/af/ERR_UNSUP_REQ /usr/share/squid/errors/af/ERR_URN_RESOLVE /usr/share/squid/errors/af/ERR_WRITE_ERROR /usr/share/squid/errors/af/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/af/error-details.txt /usr/share/squid/errors/ar /usr/share/squid/errors/ar-ae /usr/share/squid/errors/ar-bh /usr/share/squid/errors/ar-dz /usr/share/squid/errors/ar-eg /usr/share/squid/errors/ar-iq /usr/share/squid/errors/ar-jo /usr/share/squid/errors/ar-kw /usr/share/squid/errors/ar-lb /usr/share/squid/errors/ar-ly /usr/share/squid/errors/ar-ma /usr/share/squid/errors/ar-om /usr/share/squid/errors/ar-qa /usr/share/squid/errors/ar-sa /usr/share/squid/errors/ar-sy /usr/share/squid/errors/ar-tn /usr/share/squid/errors/ar-ye /usr/share/squid/errors/ar/ERR_ACCESS_DENIED /usr/share/squid/errors/ar/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/ar/ERR_AGENT_CONFIGURE /usr/share/squid/errors/ar/ERR_AGENT_WPAD /usr/share/squid/errors/ar/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/ar/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/ar/ERR_CANNOT_FORWARD /usr/share/squid/errors/ar/ERR_CONFLICT_HOST /usr/share/squid/errors/ar/ERR_CONNECT_FAIL /usr/share/squid/errors/ar/ERR_DIR_LISTING /usr/share/squid/errors/ar/ERR_DNS_FAIL /usr/share/squid/errors/ar/ERR_ESI /usr/share/squid/errors/ar/ERR_FORWARDING_DENIED /usr/share/squid/errors/ar/ERR_FTP_DISABLED /usr/share/squid/errors/ar/ERR_FTP_FAILURE /usr/share/squid/errors/ar/ERR_FTP_FORBIDDEN /usr/share/squid/errors/ar/ERR_FTP_NOT_FOUND /usr/share/squid/errors/ar/ERR_FTP_PUT_CREATED /usr/share/squid/errors/ar/ERR_FTP_PUT_ERROR /usr/share/squid/errors/ar/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/ar/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/ar/ERR_GATEWAY_FAILURE /usr/share/squid/errors/ar/ERR_ICAP_FAILURE /usr/share/squid/errors/ar/ERR_INVALID_REQ /usr/share/squid/errors/ar/ERR_INVALID_RESP /usr/share/squid/errors/ar/ERR_INVALID_URL /usr/share/squid/errors/ar/ERR_LIFETIME_EXP /usr/share/squid/errors/ar/ERR_NO_RELAY /usr/share/squid/errors/ar/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/ar/ERR_PRECONDITION_FAILED /usr/share/squid/errors/ar/ERR_READ_ERROR /usr/share/squid/errors/ar/ERR_READ_TIMEOUT /usr/share/squid/errors/ar/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/ar/ERR_SHUTTING_DOWN /usr/share/squid/errors/ar/ERR_SOCKET_FAILURE /usr/share/squid/errors/ar/ERR_TOO_BIG /usr/share/squid/errors/ar/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/ar/ERR_UNSUP_REQ /usr/share/squid/errors/ar/ERR_URN_RESOLVE /usr/share/squid/errors/ar/ERR_WRITE_ERROR /usr/share/squid/errors/ar/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/ar/error-details.txt /usr/share/squid/errors/az /usr/share/squid/errors/az-az /usr/share/squid/errors/az/ERR_ACCESS_DENIED /usr/share/squid/errors/az/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/az/ERR_AGENT_CONFIGURE /usr/share/squid/errors/az/ERR_AGENT_WPAD /usr/share/squid/errors/az/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/az/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/az/ERR_CANNOT_FORWARD /usr/share/squid/errors/az/ERR_CONFLICT_HOST /usr/share/squid/errors/az/ERR_CONNECT_FAIL /usr/share/squid/errors/az/ERR_DIR_LISTING /usr/share/squid/errors/az/ERR_DNS_FAIL /usr/share/squid/errors/az/ERR_ESI /usr/share/squid/errors/az/ERR_FORWARDING_DENIED /usr/share/squid/errors/az/ERR_FTP_DISABLED /usr/share/squid/errors/az/ERR_FTP_FAILURE /usr/share/squid/errors/az/ERR_FTP_FORBIDDEN /usr/share/squid/errors/az/ERR_FTP_NOT_FOUND /usr/share/squid/errors/az/ERR_FTP_PUT_CREATED /usr/share/squid/errors/az/ERR_FTP_PUT_ERROR /usr/share/squid/errors/az/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/az/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/az/ERR_GATEWAY_FAILURE /usr/share/squid/errors/az/ERR_ICAP_FAILURE /usr/share/squid/errors/az/ERR_INVALID_REQ /usr/share/squid/errors/az/ERR_INVALID_RESP /usr/share/squid/errors/az/ERR_INVALID_URL /usr/share/squid/errors/az/ERR_LIFETIME_EXP /usr/share/squid/errors/az/ERR_NO_RELAY /usr/share/squid/errors/az/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/az/ERR_PRECONDITION_FAILED /usr/share/squid/errors/az/ERR_READ_ERROR /usr/share/squid/errors/az/ERR_READ_TIMEOUT /usr/share/squid/errors/az/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/az/ERR_SHUTTING_DOWN /usr/share/squid/errors/az/ERR_SOCKET_FAILURE /usr/share/squid/errors/az/ERR_TOO_BIG /usr/share/squid/errors/az/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/az/ERR_UNSUP_REQ /usr/share/squid/errors/az/ERR_URN_RESOLVE /usr/share/squid/errors/az/ERR_WRITE_ERROR /usr/share/squid/errors/az/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/az/error-details.txt /usr/share/squid/errors/bg /usr/share/squid/errors/bg-bg /usr/share/squid/errors/bg/ERR_ACCESS_DENIED /usr/share/squid/errors/bg/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/bg/ERR_AGENT_CONFIGURE /usr/share/squid/errors/bg/ERR_AGENT_WPAD /usr/share/squid/errors/bg/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/bg/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/bg/ERR_CANNOT_FORWARD /usr/share/squid/errors/bg/ERR_CONFLICT_HOST /usr/share/squid/errors/bg/ERR_CONNECT_FAIL /usr/share/squid/errors/bg/ERR_DIR_LISTING /usr/share/squid/errors/bg/ERR_DNS_FAIL /usr/share/squid/errors/bg/ERR_ESI /usr/share/squid/errors/bg/ERR_FORWARDING_DENIED /usr/share/squid/errors/bg/ERR_FTP_DISABLED /usr/share/squid/errors/bg/ERR_FTP_FAILURE /usr/share/squid/errors/bg/ERR_FTP_FORBIDDEN /usr/share/squid/errors/bg/ERR_FTP_NOT_FOUND /usr/share/squid/errors/bg/ERR_FTP_PUT_CREATED /usr/share/squid/errors/bg/ERR_FTP_PUT_ERROR /usr/share/squid/errors/bg/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/bg/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/bg/ERR_GATEWAY_FAILURE /usr/share/squid/errors/bg/ERR_ICAP_FAILURE /usr/share/squid/errors/bg/ERR_INVALID_REQ /usr/share/squid/errors/bg/ERR_INVALID_RESP /usr/share/squid/errors/bg/ERR_INVALID_URL /usr/share/squid/errors/bg/ERR_LIFETIME_EXP /usr/share/squid/errors/bg/ERR_NO_RELAY /usr/share/squid/errors/bg/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/bg/ERR_PRECONDITION_FAILED /usr/share/squid/errors/bg/ERR_READ_ERROR /usr/share/squid/errors/bg/ERR_READ_TIMEOUT /usr/share/squid/errors/bg/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/bg/ERR_SHUTTING_DOWN /usr/share/squid/errors/bg/ERR_SOCKET_FAILURE /usr/share/squid/errors/bg/ERR_TOO_BIG /usr/share/squid/errors/bg/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/bg/ERR_UNSUP_REQ /usr/share/squid/errors/bg/ERR_URN_RESOLVE /usr/share/squid/errors/bg/ERR_WRITE_ERROR /usr/share/squid/errors/bg/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/bg/error-details.txt /usr/share/squid/errors/ca /usr/share/squid/errors/ca/ERR_ACCESS_DENIED /usr/share/squid/errors/ca/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/ca/ERR_AGENT_CONFIGURE /usr/share/squid/errors/ca/ERR_AGENT_WPAD /usr/share/squid/errors/ca/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/ca/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/ca/ERR_CANNOT_FORWARD /usr/share/squid/errors/ca/ERR_CONFLICT_HOST /usr/share/squid/errors/ca/ERR_CONNECT_FAIL /usr/share/squid/errors/ca/ERR_DIR_LISTING /usr/share/squid/errors/ca/ERR_DNS_FAIL /usr/share/squid/errors/ca/ERR_ESI /usr/share/squid/errors/ca/ERR_FORWARDING_DENIED /usr/share/squid/errors/ca/ERR_FTP_DISABLED /usr/share/squid/errors/ca/ERR_FTP_FAILURE /usr/share/squid/errors/ca/ERR_FTP_FORBIDDEN /usr/share/squid/errors/ca/ERR_FTP_NOT_FOUND /usr/share/squid/errors/ca/ERR_FTP_PUT_CREATED /usr/share/squid/errors/ca/ERR_FTP_PUT_ERROR /usr/share/squid/errors/ca/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/ca/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/ca/ERR_GATEWAY_FAILURE /usr/share/squid/errors/ca/ERR_ICAP_FAILURE /usr/share/squid/errors/ca/ERR_INVALID_REQ /usr/share/squid/errors/ca/ERR_INVALID_RESP /usr/share/squid/errors/ca/ERR_INVALID_URL /usr/share/squid/errors/ca/ERR_LIFETIME_EXP /usr/share/squid/errors/ca/ERR_NO_RELAY /usr/share/squid/errors/ca/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/ca/ERR_PRECONDITION_FAILED /usr/share/squid/errors/ca/ERR_READ_ERROR /usr/share/squid/errors/ca/ERR_READ_TIMEOUT /usr/share/squid/errors/ca/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/ca/ERR_SHUTTING_DOWN /usr/share/squid/errors/ca/ERR_SOCKET_FAILURE /usr/share/squid/errors/ca/ERR_TOO_BIG /usr/share/squid/errors/ca/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/ca/ERR_UNSUP_REQ /usr/share/squid/errors/ca/ERR_URN_RESOLVE /usr/share/squid/errors/ca/ERR_WRITE_ERROR /usr/share/squid/errors/ca/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/ca/error-details.txt /usr/share/squid/errors/cs /usr/share/squid/errors/cs-cz /usr/share/squid/errors/cs/ERR_ACCESS_DENIED /usr/share/squid/errors/cs/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/cs/ERR_AGENT_CONFIGURE /usr/share/squid/errors/cs/ERR_AGENT_WPAD /usr/share/squid/errors/cs/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/cs/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/cs/ERR_CANNOT_FORWARD /usr/share/squid/errors/cs/ERR_CONFLICT_HOST /usr/share/squid/errors/cs/ERR_CONNECT_FAIL /usr/share/squid/errors/cs/ERR_DIR_LISTING /usr/share/squid/errors/cs/ERR_DNS_FAIL /usr/share/squid/errors/cs/ERR_ESI /usr/share/squid/errors/cs/ERR_FORWARDING_DENIED /usr/share/squid/errors/cs/ERR_FTP_DISABLED /usr/share/squid/errors/cs/ERR_FTP_FAILURE /usr/share/squid/errors/cs/ERR_FTP_FORBIDDEN /usr/share/squid/errors/cs/ERR_FTP_NOT_FOUND /usr/share/squid/errors/cs/ERR_FTP_PUT_CREATED /usr/share/squid/errors/cs/ERR_FTP_PUT_ERROR /usr/share/squid/errors/cs/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/cs/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/cs/ERR_GATEWAY_FAILURE /usr/share/squid/errors/cs/ERR_ICAP_FAILURE /usr/share/squid/errors/cs/ERR_INVALID_REQ /usr/share/squid/errors/cs/ERR_INVALID_RESP /usr/share/squid/errors/cs/ERR_INVALID_URL /usr/share/squid/errors/cs/ERR_LIFETIME_EXP /usr/share/squid/errors/cs/ERR_NO_RELAY /usr/share/squid/errors/cs/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/cs/ERR_PRECONDITION_FAILED /usr/share/squid/errors/cs/ERR_READ_ERROR /usr/share/squid/errors/cs/ERR_READ_TIMEOUT /usr/share/squid/errors/cs/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/cs/ERR_SHUTTING_DOWN /usr/share/squid/errors/cs/ERR_SOCKET_FAILURE /usr/share/squid/errors/cs/ERR_TOO_BIG /usr/share/squid/errors/cs/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/cs/ERR_UNSUP_REQ /usr/share/squid/errors/cs/ERR_URN_RESOLVE /usr/share/squid/errors/cs/ERR_WRITE_ERROR /usr/share/squid/errors/cs/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/cs/error-details.txt /usr/share/squid/errors/da /usr/share/squid/errors/da-dk /usr/share/squid/errors/da/ERR_ACCESS_DENIED /usr/share/squid/errors/da/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/da/ERR_AGENT_CONFIGURE /usr/share/squid/errors/da/ERR_AGENT_WPAD /usr/share/squid/errors/da/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/da/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/da/ERR_CANNOT_FORWARD /usr/share/squid/errors/da/ERR_CONFLICT_HOST /usr/share/squid/errors/da/ERR_CONNECT_FAIL /usr/share/squid/errors/da/ERR_DIR_LISTING /usr/share/squid/errors/da/ERR_DNS_FAIL /usr/share/squid/errors/da/ERR_ESI /usr/share/squid/errors/da/ERR_FORWARDING_DENIED /usr/share/squid/errors/da/ERR_FTP_DISABLED /usr/share/squid/errors/da/ERR_FTP_FAILURE /usr/share/squid/errors/da/ERR_FTP_FORBIDDEN /usr/share/squid/errors/da/ERR_FTP_NOT_FOUND /usr/share/squid/errors/da/ERR_FTP_PUT_CREATED /usr/share/squid/errors/da/ERR_FTP_PUT_ERROR /usr/share/squid/errors/da/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/da/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/da/ERR_GATEWAY_FAILURE /usr/share/squid/errors/da/ERR_ICAP_FAILURE /usr/share/squid/errors/da/ERR_INVALID_REQ /usr/share/squid/errors/da/ERR_INVALID_RESP /usr/share/squid/errors/da/ERR_INVALID_URL /usr/share/squid/errors/da/ERR_LIFETIME_EXP /usr/share/squid/errors/da/ERR_NO_RELAY /usr/share/squid/errors/da/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/da/ERR_PRECONDITION_FAILED /usr/share/squid/errors/da/ERR_READ_ERROR /usr/share/squid/errors/da/ERR_READ_TIMEOUT /usr/share/squid/errors/da/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/da/ERR_SHUTTING_DOWN /usr/share/squid/errors/da/ERR_SOCKET_FAILURE /usr/share/squid/errors/da/ERR_TOO_BIG /usr/share/squid/errors/da/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/da/ERR_UNSUP_REQ /usr/share/squid/errors/da/ERR_URN_RESOLVE /usr/share/squid/errors/da/ERR_WRITE_ERROR /usr/share/squid/errors/da/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/da/error-details.txt /usr/share/squid/errors/de /usr/share/squid/errors/de-at /usr/share/squid/errors/de-ch /usr/share/squid/errors/de-de /usr/share/squid/errors/de-li /usr/share/squid/errors/de-lu /usr/share/squid/errors/de/ERR_ACCESS_DENIED /usr/share/squid/errors/de/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/de/ERR_AGENT_CONFIGURE /usr/share/squid/errors/de/ERR_AGENT_WPAD /usr/share/squid/errors/de/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/de/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/de/ERR_CANNOT_FORWARD /usr/share/squid/errors/de/ERR_CONFLICT_HOST /usr/share/squid/errors/de/ERR_CONNECT_FAIL /usr/share/squid/errors/de/ERR_DIR_LISTING /usr/share/squid/errors/de/ERR_DNS_FAIL /usr/share/squid/errors/de/ERR_ESI /usr/share/squid/errors/de/ERR_FORWARDING_DENIED /usr/share/squid/errors/de/ERR_FTP_DISABLED /usr/share/squid/errors/de/ERR_FTP_FAILURE /usr/share/squid/errors/de/ERR_FTP_FORBIDDEN /usr/share/squid/errors/de/ERR_FTP_NOT_FOUND /usr/share/squid/errors/de/ERR_FTP_PUT_CREATED /usr/share/squid/errors/de/ERR_FTP_PUT_ERROR /usr/share/squid/errors/de/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/de/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/de/ERR_GATEWAY_FAILURE /usr/share/squid/errors/de/ERR_ICAP_FAILURE /usr/share/squid/errors/de/ERR_INVALID_REQ /usr/share/squid/errors/de/ERR_INVALID_RESP /usr/share/squid/errors/de/ERR_INVALID_URL /usr/share/squid/errors/de/ERR_LIFETIME_EXP /usr/share/squid/errors/de/ERR_NO_RELAY /usr/share/squid/errors/de/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/de/ERR_PRECONDITION_FAILED /usr/share/squid/errors/de/ERR_READ_ERROR /usr/share/squid/errors/de/ERR_READ_TIMEOUT /usr/share/squid/errors/de/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/de/ERR_SHUTTING_DOWN /usr/share/squid/errors/de/ERR_SOCKET_FAILURE /usr/share/squid/errors/de/ERR_TOO_BIG /usr/share/squid/errors/de/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/de/ERR_UNSUP_REQ /usr/share/squid/errors/de/ERR_URN_RESOLVE /usr/share/squid/errors/de/ERR_WRITE_ERROR /usr/share/squid/errors/de/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/de/error-details.txt /usr/share/squid/errors/el /usr/share/squid/errors/el-gr /usr/share/squid/errors/el/ERR_ACCESS_DENIED /usr/share/squid/errors/el/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/el/ERR_AGENT_CONFIGURE /usr/share/squid/errors/el/ERR_AGENT_WPAD /usr/share/squid/errors/el/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/el/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/el/ERR_CANNOT_FORWARD /usr/share/squid/errors/el/ERR_CONFLICT_HOST /usr/share/squid/errors/el/ERR_CONNECT_FAIL /usr/share/squid/errors/el/ERR_DIR_LISTING /usr/share/squid/errors/el/ERR_DNS_FAIL /usr/share/squid/errors/el/ERR_ESI /usr/share/squid/errors/el/ERR_FORWARDING_DENIED /usr/share/squid/errors/el/ERR_FTP_DISABLED /usr/share/squid/errors/el/ERR_FTP_FAILURE /usr/share/squid/errors/el/ERR_FTP_FORBIDDEN /usr/share/squid/errors/el/ERR_FTP_NOT_FOUND /usr/share/squid/errors/el/ERR_FTP_PUT_CREATED /usr/share/squid/errors/el/ERR_FTP_PUT_ERROR /usr/share/squid/errors/el/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/el/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/el/ERR_GATEWAY_FAILURE /usr/share/squid/errors/el/ERR_ICAP_FAILURE /usr/share/squid/errors/el/ERR_INVALID_REQ /usr/share/squid/errors/el/ERR_INVALID_RESP /usr/share/squid/errors/el/ERR_INVALID_URL /usr/share/squid/errors/el/ERR_LIFETIME_EXP /usr/share/squid/errors/el/ERR_NO_RELAY /usr/share/squid/errors/el/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/el/ERR_PRECONDITION_FAILED /usr/share/squid/errors/el/ERR_READ_ERROR /usr/share/squid/errors/el/ERR_READ_TIMEOUT /usr/share/squid/errors/el/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/el/ERR_SHUTTING_DOWN /usr/share/squid/errors/el/ERR_SOCKET_FAILURE /usr/share/squid/errors/el/ERR_TOO_BIG /usr/share/squid/errors/el/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/el/ERR_UNSUP_REQ /usr/share/squid/errors/el/ERR_URN_RESOLVE /usr/share/squid/errors/el/ERR_WRITE_ERROR /usr/share/squid/errors/el/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/el/error-details.txt /usr/share/squid/errors/en /usr/share/squid/errors/en-au /usr/share/squid/errors/en-bz /usr/share/squid/errors/en-ca /usr/share/squid/errors/en-gb /usr/share/squid/errors/en-ie /usr/share/squid/errors/en-in /usr/share/squid/errors/en-jm /usr/share/squid/errors/en-nz /usr/share/squid/errors/en-ph /usr/share/squid/errors/en-sg /usr/share/squid/errors/en-tt /usr/share/squid/errors/en-uk /usr/share/squid/errors/en-us /usr/share/squid/errors/en-za /usr/share/squid/errors/en-zw /usr/share/squid/errors/en/ERR_ACCESS_DENIED /usr/share/squid/errors/en/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/en/ERR_AGENT_CONFIGURE /usr/share/squid/errors/en/ERR_AGENT_WPAD /usr/share/squid/errors/en/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/en/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/en/ERR_CANNOT_FORWARD /usr/share/squid/errors/en/ERR_CONFLICT_HOST /usr/share/squid/errors/en/ERR_CONNECT_FAIL /usr/share/squid/errors/en/ERR_DIR_LISTING /usr/share/squid/errors/en/ERR_DNS_FAIL /usr/share/squid/errors/en/ERR_ESI /usr/share/squid/errors/en/ERR_FORWARDING_DENIED /usr/share/squid/errors/en/ERR_FTP_DISABLED /usr/share/squid/errors/en/ERR_FTP_FAILURE /usr/share/squid/errors/en/ERR_FTP_FORBIDDEN /usr/share/squid/errors/en/ERR_FTP_NOT_FOUND /usr/share/squid/errors/en/ERR_FTP_PUT_CREATED /usr/share/squid/errors/en/ERR_FTP_PUT_ERROR /usr/share/squid/errors/en/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/en/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/en/ERR_GATEWAY_FAILURE /usr/share/squid/errors/en/ERR_ICAP_FAILURE /usr/share/squid/errors/en/ERR_INVALID_REQ /usr/share/squid/errors/en/ERR_INVALID_RESP /usr/share/squid/errors/en/ERR_INVALID_URL /usr/share/squid/errors/en/ERR_LIFETIME_EXP /usr/share/squid/errors/en/ERR_NO_RELAY /usr/share/squid/errors/en/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/en/ERR_PRECONDITION_FAILED /usr/share/squid/errors/en/ERR_READ_ERROR /usr/share/squid/errors/en/ERR_READ_TIMEOUT /usr/share/squid/errors/en/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/en/ERR_SHUTTING_DOWN /usr/share/squid/errors/en/ERR_SOCKET_FAILURE /usr/share/squid/errors/en/ERR_TOO_BIG /usr/share/squid/errors/en/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/en/ERR_UNSUP_REQ /usr/share/squid/errors/en/ERR_URN_RESOLVE /usr/share/squid/errors/en/ERR_WRITE_ERROR /usr/share/squid/errors/en/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/en/error-details.txt /usr/share/squid/errors/es /usr/share/squid/errors/es-ar /usr/share/squid/errors/es-bo /usr/share/squid/errors/es-cl /usr/share/squid/errors/es-co /usr/share/squid/errors/es-cr /usr/share/squid/errors/es-do /usr/share/squid/errors/es-ec /usr/share/squid/errors/es-es /usr/share/squid/errors/es-gt /usr/share/squid/errors/es-hn /usr/share/squid/errors/es-mx /usr/share/squid/errors/es-ni /usr/share/squid/errors/es-pa /usr/share/squid/errors/es-pe /usr/share/squid/errors/es-pr /usr/share/squid/errors/es-py /usr/share/squid/errors/es-sv /usr/share/squid/errors/es-uy /usr/share/squid/errors/es-ve /usr/share/squid/errors/es/ERR_ACCESS_DENIED /usr/share/squid/errors/es/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/es/ERR_AGENT_CONFIGURE /usr/share/squid/errors/es/ERR_AGENT_WPAD /usr/share/squid/errors/es/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/es/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/es/ERR_CANNOT_FORWARD /usr/share/squid/errors/es/ERR_CONFLICT_HOST /usr/share/squid/errors/es/ERR_CONNECT_FAIL /usr/share/squid/errors/es/ERR_DIR_LISTING /usr/share/squid/errors/es/ERR_DNS_FAIL /usr/share/squid/errors/es/ERR_ESI /usr/share/squid/errors/es/ERR_FORWARDING_DENIED /usr/share/squid/errors/es/ERR_FTP_DISABLED /usr/share/squid/errors/es/ERR_FTP_FAILURE /usr/share/squid/errors/es/ERR_FTP_FORBIDDEN /usr/share/squid/errors/es/ERR_FTP_NOT_FOUND /usr/share/squid/errors/es/ERR_FTP_PUT_CREATED /usr/share/squid/errors/es/ERR_FTP_PUT_ERROR /usr/share/squid/errors/es/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/es/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/es/ERR_GATEWAY_FAILURE /usr/share/squid/errors/es/ERR_ICAP_FAILURE /usr/share/squid/errors/es/ERR_INVALID_REQ /usr/share/squid/errors/es/ERR_INVALID_RESP /usr/share/squid/errors/es/ERR_INVALID_URL /usr/share/squid/errors/es/ERR_LIFETIME_EXP /usr/share/squid/errors/es/ERR_NO_RELAY /usr/share/squid/errors/es/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/es/ERR_PRECONDITION_FAILED /usr/share/squid/errors/es/ERR_READ_ERROR /usr/share/squid/errors/es/ERR_READ_TIMEOUT /usr/share/squid/errors/es/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/es/ERR_SHUTTING_DOWN /usr/share/squid/errors/es/ERR_SOCKET_FAILURE /usr/share/squid/errors/es/ERR_TOO_BIG /usr/share/squid/errors/es/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/es/ERR_UNSUP_REQ /usr/share/squid/errors/es/ERR_URN_RESOLVE /usr/share/squid/errors/es/ERR_WRITE_ERROR /usr/share/squid/errors/es/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/es/error-details.txt /usr/share/squid/errors/et /usr/share/squid/errors/et-ee /usr/share/squid/errors/et/ERR_ACCESS_DENIED /usr/share/squid/errors/et/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/et/ERR_AGENT_CONFIGURE /usr/share/squid/errors/et/ERR_AGENT_WPAD /usr/share/squid/errors/et/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/et/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/et/ERR_CANNOT_FORWARD /usr/share/squid/errors/et/ERR_CONFLICT_HOST /usr/share/squid/errors/et/ERR_CONNECT_FAIL /usr/share/squid/errors/et/ERR_DIR_LISTING /usr/share/squid/errors/et/ERR_DNS_FAIL /usr/share/squid/errors/et/ERR_ESI /usr/share/squid/errors/et/ERR_FORWARDING_DENIED /usr/share/squid/errors/et/ERR_FTP_DISABLED /usr/share/squid/errors/et/ERR_FTP_FAILURE /usr/share/squid/errors/et/ERR_FTP_FORBIDDEN /usr/share/squid/errors/et/ERR_FTP_NOT_FOUND /usr/share/squid/errors/et/ERR_FTP_PUT_CREATED /usr/share/squid/errors/et/ERR_FTP_PUT_ERROR /usr/share/squid/errors/et/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/et/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/et/ERR_GATEWAY_FAILURE /usr/share/squid/errors/et/ERR_ICAP_FAILURE /usr/share/squid/errors/et/ERR_INVALID_REQ /usr/share/squid/errors/et/ERR_INVALID_RESP /usr/share/squid/errors/et/ERR_INVALID_URL /usr/share/squid/errors/et/ERR_LIFETIME_EXP /usr/share/squid/errors/et/ERR_NO_RELAY /usr/share/squid/errors/et/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/et/ERR_PRECONDITION_FAILED /usr/share/squid/errors/et/ERR_READ_ERROR /usr/share/squid/errors/et/ERR_READ_TIMEOUT /usr/share/squid/errors/et/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/et/ERR_SHUTTING_DOWN /usr/share/squid/errors/et/ERR_SOCKET_FAILURE /usr/share/squid/errors/et/ERR_TOO_BIG /usr/share/squid/errors/et/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/et/ERR_UNSUP_REQ /usr/share/squid/errors/et/ERR_URN_RESOLVE /usr/share/squid/errors/et/ERR_WRITE_ERROR /usr/share/squid/errors/et/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/et/error-details.txt /usr/share/squid/errors/fa /usr/share/squid/errors/fa-fa /usr/share/squid/errors/fa-ir /usr/share/squid/errors/fa/ERR_ACCESS_DENIED /usr/share/squid/errors/fa/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/fa/ERR_AGENT_CONFIGURE /usr/share/squid/errors/fa/ERR_AGENT_WPAD /usr/share/squid/errors/fa/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/fa/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/fa/ERR_CANNOT_FORWARD /usr/share/squid/errors/fa/ERR_CONFLICT_HOST /usr/share/squid/errors/fa/ERR_CONNECT_FAIL /usr/share/squid/errors/fa/ERR_DIR_LISTING /usr/share/squid/errors/fa/ERR_DNS_FAIL /usr/share/squid/errors/fa/ERR_ESI /usr/share/squid/errors/fa/ERR_FORWARDING_DENIED /usr/share/squid/errors/fa/ERR_FTP_DISABLED /usr/share/squid/errors/fa/ERR_FTP_FAILURE /usr/share/squid/errors/fa/ERR_FTP_FORBIDDEN /usr/share/squid/errors/fa/ERR_FTP_NOT_FOUND /usr/share/squid/errors/fa/ERR_FTP_PUT_CREATED /usr/share/squid/errors/fa/ERR_FTP_PUT_ERROR /usr/share/squid/errors/fa/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/fa/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/fa/ERR_GATEWAY_FAILURE /usr/share/squid/errors/fa/ERR_ICAP_FAILURE /usr/share/squid/errors/fa/ERR_INVALID_REQ /usr/share/squid/errors/fa/ERR_INVALID_RESP /usr/share/squid/errors/fa/ERR_INVALID_URL /usr/share/squid/errors/fa/ERR_LIFETIME_EXP /usr/share/squid/errors/fa/ERR_NO_RELAY /usr/share/squid/errors/fa/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/fa/ERR_PRECONDITION_FAILED /usr/share/squid/errors/fa/ERR_READ_ERROR /usr/share/squid/errors/fa/ERR_READ_TIMEOUT /usr/share/squid/errors/fa/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/fa/ERR_SHUTTING_DOWN /usr/share/squid/errors/fa/ERR_SOCKET_FAILURE /usr/share/squid/errors/fa/ERR_TOO_BIG /usr/share/squid/errors/fa/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/fa/ERR_UNSUP_REQ /usr/share/squid/errors/fa/ERR_URN_RESOLVE /usr/share/squid/errors/fa/ERR_WRITE_ERROR /usr/share/squid/errors/fa/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/fa/error-details.txt /usr/share/squid/errors/fi /usr/share/squid/errors/fi-fi /usr/share/squid/errors/fi/ERR_ACCESS_DENIED /usr/share/squid/errors/fi/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/fi/ERR_AGENT_CONFIGURE /usr/share/squid/errors/fi/ERR_AGENT_WPAD /usr/share/squid/errors/fi/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/fi/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/fi/ERR_CANNOT_FORWARD /usr/share/squid/errors/fi/ERR_CONFLICT_HOST /usr/share/squid/errors/fi/ERR_CONNECT_FAIL /usr/share/squid/errors/fi/ERR_DIR_LISTING /usr/share/squid/errors/fi/ERR_DNS_FAIL /usr/share/squid/errors/fi/ERR_ESI /usr/share/squid/errors/fi/ERR_FORWARDING_DENIED /usr/share/squid/errors/fi/ERR_FTP_DISABLED /usr/share/squid/errors/fi/ERR_FTP_FAILURE /usr/share/squid/errors/fi/ERR_FTP_FORBIDDEN /usr/share/squid/errors/fi/ERR_FTP_NOT_FOUND /usr/share/squid/errors/fi/ERR_FTP_PUT_CREATED /usr/share/squid/errors/fi/ERR_FTP_PUT_ERROR /usr/share/squid/errors/fi/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/fi/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/fi/ERR_GATEWAY_FAILURE /usr/share/squid/errors/fi/ERR_ICAP_FAILURE /usr/share/squid/errors/fi/ERR_INVALID_REQ /usr/share/squid/errors/fi/ERR_INVALID_RESP /usr/share/squid/errors/fi/ERR_INVALID_URL /usr/share/squid/errors/fi/ERR_LIFETIME_EXP /usr/share/squid/errors/fi/ERR_NO_RELAY /usr/share/squid/errors/fi/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/fi/ERR_PRECONDITION_FAILED /usr/share/squid/errors/fi/ERR_READ_ERROR /usr/share/squid/errors/fi/ERR_READ_TIMEOUT /usr/share/squid/errors/fi/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/fi/ERR_SHUTTING_DOWN /usr/share/squid/errors/fi/ERR_SOCKET_FAILURE /usr/share/squid/errors/fi/ERR_TOO_BIG /usr/share/squid/errors/fi/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/fi/ERR_UNSUP_REQ /usr/share/squid/errors/fi/ERR_URN_RESOLVE /usr/share/squid/errors/fi/ERR_WRITE_ERROR /usr/share/squid/errors/fi/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/fi/error-details.txt /usr/share/squid/errors/fr /usr/share/squid/errors/fr-be /usr/share/squid/errors/fr-ca /usr/share/squid/errors/fr-ch /usr/share/squid/errors/fr-fr /usr/share/squid/errors/fr-lu /usr/share/squid/errors/fr-mc /usr/share/squid/errors/fr/ERR_ACCESS_DENIED /usr/share/squid/errors/fr/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/fr/ERR_AGENT_CONFIGURE /usr/share/squid/errors/fr/ERR_AGENT_WPAD /usr/share/squid/errors/fr/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/fr/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/fr/ERR_CANNOT_FORWARD /usr/share/squid/errors/fr/ERR_CONFLICT_HOST /usr/share/squid/errors/fr/ERR_CONNECT_FAIL /usr/share/squid/errors/fr/ERR_DIR_LISTING /usr/share/squid/errors/fr/ERR_DNS_FAIL /usr/share/squid/errors/fr/ERR_ESI /usr/share/squid/errors/fr/ERR_FORWARDING_DENIED /usr/share/squid/errors/fr/ERR_FTP_DISABLED /usr/share/squid/errors/fr/ERR_FTP_FAILURE /usr/share/squid/errors/fr/ERR_FTP_FORBIDDEN /usr/share/squid/errors/fr/ERR_FTP_NOT_FOUND /usr/share/squid/errors/fr/ERR_FTP_PUT_CREATED /usr/share/squid/errors/fr/ERR_FTP_PUT_ERROR /usr/share/squid/errors/fr/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/fr/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/fr/ERR_GATEWAY_FAILURE /usr/share/squid/errors/fr/ERR_ICAP_FAILURE /usr/share/squid/errors/fr/ERR_INVALID_REQ /usr/share/squid/errors/fr/ERR_INVALID_RESP /usr/share/squid/errors/fr/ERR_INVALID_URL /usr/share/squid/errors/fr/ERR_LIFETIME_EXP /usr/share/squid/errors/fr/ERR_NO_RELAY /usr/share/squid/errors/fr/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/fr/ERR_PRECONDITION_FAILED /usr/share/squid/errors/fr/ERR_READ_ERROR /usr/share/squid/errors/fr/ERR_READ_TIMEOUT /usr/share/squid/errors/fr/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/fr/ERR_SHUTTING_DOWN /usr/share/squid/errors/fr/ERR_SOCKET_FAILURE /usr/share/squid/errors/fr/ERR_TOO_BIG /usr/share/squid/errors/fr/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/fr/ERR_UNSUP_REQ /usr/share/squid/errors/fr/ERR_URN_RESOLVE /usr/share/squid/errors/fr/ERR_WRITE_ERROR /usr/share/squid/errors/fr/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/fr/error-details.txt /usr/share/squid/errors/he /usr/share/squid/errors/he-il /usr/share/squid/errors/he/ERR_ACCESS_DENIED /usr/share/squid/errors/he/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/he/ERR_AGENT_CONFIGURE /usr/share/squid/errors/he/ERR_AGENT_WPAD /usr/share/squid/errors/he/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/he/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/he/ERR_CANNOT_FORWARD /usr/share/squid/errors/he/ERR_CONFLICT_HOST /usr/share/squid/errors/he/ERR_CONNECT_FAIL /usr/share/squid/errors/he/ERR_DIR_LISTING /usr/share/squid/errors/he/ERR_DNS_FAIL /usr/share/squid/errors/he/ERR_ESI /usr/share/squid/errors/he/ERR_FORWARDING_DENIED /usr/share/squid/errors/he/ERR_FTP_DISABLED /usr/share/squid/errors/he/ERR_FTP_FAILURE /usr/share/squid/errors/he/ERR_FTP_FORBIDDEN /usr/share/squid/errors/he/ERR_FTP_NOT_FOUND /usr/share/squid/errors/he/ERR_FTP_PUT_CREATED /usr/share/squid/errors/he/ERR_FTP_PUT_ERROR /usr/share/squid/errors/he/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/he/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/he/ERR_GATEWAY_FAILURE /usr/share/squid/errors/he/ERR_ICAP_FAILURE /usr/share/squid/errors/he/ERR_INVALID_REQ /usr/share/squid/errors/he/ERR_INVALID_RESP /usr/share/squid/errors/he/ERR_INVALID_URL /usr/share/squid/errors/he/ERR_LIFETIME_EXP /usr/share/squid/errors/he/ERR_NO_RELAY /usr/share/squid/errors/he/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/he/ERR_PRECONDITION_FAILED /usr/share/squid/errors/he/ERR_READ_ERROR /usr/share/squid/errors/he/ERR_READ_TIMEOUT /usr/share/squid/errors/he/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/he/ERR_SHUTTING_DOWN /usr/share/squid/errors/he/ERR_SOCKET_FAILURE /usr/share/squid/errors/he/ERR_TOO_BIG /usr/share/squid/errors/he/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/he/ERR_UNSUP_REQ /usr/share/squid/errors/he/ERR_URN_RESOLVE /usr/share/squid/errors/he/ERR_WRITE_ERROR /usr/share/squid/errors/he/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/he/error-details.txt /usr/share/squid/errors/hu /usr/share/squid/errors/hu-hu /usr/share/squid/errors/hu/ERR_ACCESS_DENIED /usr/share/squid/errors/hu/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/hu/ERR_AGENT_CONFIGURE /usr/share/squid/errors/hu/ERR_AGENT_WPAD /usr/share/squid/errors/hu/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/hu/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/hu/ERR_CANNOT_FORWARD /usr/share/squid/errors/hu/ERR_CONFLICT_HOST /usr/share/squid/errors/hu/ERR_CONNECT_FAIL /usr/share/squid/errors/hu/ERR_DIR_LISTING /usr/share/squid/errors/hu/ERR_DNS_FAIL /usr/share/squid/errors/hu/ERR_ESI /usr/share/squid/errors/hu/ERR_FORWARDING_DENIED /usr/share/squid/errors/hu/ERR_FTP_DISABLED /usr/share/squid/errors/hu/ERR_FTP_FAILURE /usr/share/squid/errors/hu/ERR_FTP_FORBIDDEN /usr/share/squid/errors/hu/ERR_FTP_NOT_FOUND /usr/share/squid/errors/hu/ERR_FTP_PUT_CREATED /usr/share/squid/errors/hu/ERR_FTP_PUT_ERROR /usr/share/squid/errors/hu/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/hu/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/hu/ERR_GATEWAY_FAILURE /usr/share/squid/errors/hu/ERR_ICAP_FAILURE /usr/share/squid/errors/hu/ERR_INVALID_REQ /usr/share/squid/errors/hu/ERR_INVALID_RESP /usr/share/squid/errors/hu/ERR_INVALID_URL /usr/share/squid/errors/hu/ERR_LIFETIME_EXP /usr/share/squid/errors/hu/ERR_NO_RELAY /usr/share/squid/errors/hu/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/hu/ERR_PRECONDITION_FAILED /usr/share/squid/errors/hu/ERR_READ_ERROR /usr/share/squid/errors/hu/ERR_READ_TIMEOUT /usr/share/squid/errors/hu/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/hu/ERR_SHUTTING_DOWN /usr/share/squid/errors/hu/ERR_SOCKET_FAILURE /usr/share/squid/errors/hu/ERR_TOO_BIG /usr/share/squid/errors/hu/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/hu/ERR_UNSUP_REQ /usr/share/squid/errors/hu/ERR_URN_RESOLVE /usr/share/squid/errors/hu/ERR_WRITE_ERROR /usr/share/squid/errors/hu/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/hu/error-details.txt /usr/share/squid/errors/hy /usr/share/squid/errors/hy-am /usr/share/squid/errors/hy-armn /usr/share/squid/errors/hy/ERR_ACCESS_DENIED /usr/share/squid/errors/hy/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/hy/ERR_AGENT_CONFIGURE /usr/share/squid/errors/hy/ERR_AGENT_WPAD /usr/share/squid/errors/hy/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/hy/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/hy/ERR_CANNOT_FORWARD /usr/share/squid/errors/hy/ERR_CONFLICT_HOST /usr/share/squid/errors/hy/ERR_CONNECT_FAIL /usr/share/squid/errors/hy/ERR_DIR_LISTING /usr/share/squid/errors/hy/ERR_DNS_FAIL /usr/share/squid/errors/hy/ERR_ESI /usr/share/squid/errors/hy/ERR_FORWARDING_DENIED /usr/share/squid/errors/hy/ERR_FTP_DISABLED /usr/share/squid/errors/hy/ERR_FTP_FAILURE /usr/share/squid/errors/hy/ERR_FTP_FORBIDDEN /usr/share/squid/errors/hy/ERR_FTP_NOT_FOUND /usr/share/squid/errors/hy/ERR_FTP_PUT_CREATED /usr/share/squid/errors/hy/ERR_FTP_PUT_ERROR /usr/share/squid/errors/hy/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/hy/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/hy/ERR_GATEWAY_FAILURE /usr/share/squid/errors/hy/ERR_ICAP_FAILURE /usr/share/squid/errors/hy/ERR_INVALID_REQ /usr/share/squid/errors/hy/ERR_INVALID_RESP /usr/share/squid/errors/hy/ERR_INVALID_URL /usr/share/squid/errors/hy/ERR_LIFETIME_EXP /usr/share/squid/errors/hy/ERR_NO_RELAY /usr/share/squid/errors/hy/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/hy/ERR_PRECONDITION_FAILED /usr/share/squid/errors/hy/ERR_READ_ERROR /usr/share/squid/errors/hy/ERR_READ_TIMEOUT /usr/share/squid/errors/hy/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/hy/ERR_SHUTTING_DOWN /usr/share/squid/errors/hy/ERR_SOCKET_FAILURE /usr/share/squid/errors/hy/ERR_TOO_BIG /usr/share/squid/errors/hy/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/hy/ERR_UNSUP_REQ /usr/share/squid/errors/hy/ERR_URN_RESOLVE /usr/share/squid/errors/hy/ERR_WRITE_ERROR /usr/share/squid/errors/hy/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/hy/error-details.txt /usr/share/squid/errors/id /usr/share/squid/errors/id-id /usr/share/squid/errors/id/ERR_ACCESS_DENIED /usr/share/squid/errors/id/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/id/ERR_AGENT_CONFIGURE /usr/share/squid/errors/id/ERR_AGENT_WPAD /usr/share/squid/errors/id/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/id/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/id/ERR_CANNOT_FORWARD /usr/share/squid/errors/id/ERR_CONFLICT_HOST /usr/share/squid/errors/id/ERR_CONNECT_FAIL /usr/share/squid/errors/id/ERR_DIR_LISTING /usr/share/squid/errors/id/ERR_DNS_FAIL /usr/share/squid/errors/id/ERR_ESI /usr/share/squid/errors/id/ERR_FORWARDING_DENIED /usr/share/squid/errors/id/ERR_FTP_DISABLED /usr/share/squid/errors/id/ERR_FTP_FAILURE /usr/share/squid/errors/id/ERR_FTP_FORBIDDEN /usr/share/squid/errors/id/ERR_FTP_NOT_FOUND /usr/share/squid/errors/id/ERR_FTP_PUT_CREATED /usr/share/squid/errors/id/ERR_FTP_PUT_ERROR /usr/share/squid/errors/id/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/id/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/id/ERR_GATEWAY_FAILURE /usr/share/squid/errors/id/ERR_ICAP_FAILURE /usr/share/squid/errors/id/ERR_INVALID_REQ /usr/share/squid/errors/id/ERR_INVALID_RESP /usr/share/squid/errors/id/ERR_INVALID_URL /usr/share/squid/errors/id/ERR_LIFETIME_EXP /usr/share/squid/errors/id/ERR_NO_RELAY /usr/share/squid/errors/id/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/id/ERR_PRECONDITION_FAILED /usr/share/squid/errors/id/ERR_READ_ERROR /usr/share/squid/errors/id/ERR_READ_TIMEOUT /usr/share/squid/errors/id/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/id/ERR_SHUTTING_DOWN /usr/share/squid/errors/id/ERR_SOCKET_FAILURE /usr/share/squid/errors/id/ERR_TOO_BIG /usr/share/squid/errors/id/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/id/ERR_UNSUP_REQ /usr/share/squid/errors/id/ERR_URN_RESOLVE /usr/share/squid/errors/id/ERR_WRITE_ERROR /usr/share/squid/errors/id/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/id/error-details.txt /usr/share/squid/errors/it /usr/share/squid/errors/it-ch /usr/share/squid/errors/it-it /usr/share/squid/errors/it/ERR_ACCESS_DENIED /usr/share/squid/errors/it/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/it/ERR_AGENT_CONFIGURE /usr/share/squid/errors/it/ERR_AGENT_WPAD /usr/share/squid/errors/it/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/it/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/it/ERR_CANNOT_FORWARD /usr/share/squid/errors/it/ERR_CONFLICT_HOST /usr/share/squid/errors/it/ERR_CONNECT_FAIL /usr/share/squid/errors/it/ERR_DIR_LISTING /usr/share/squid/errors/it/ERR_DNS_FAIL /usr/share/squid/errors/it/ERR_ESI /usr/share/squid/errors/it/ERR_FORWARDING_DENIED /usr/share/squid/errors/it/ERR_FTP_DISABLED /usr/share/squid/errors/it/ERR_FTP_FAILURE /usr/share/squid/errors/it/ERR_FTP_FORBIDDEN /usr/share/squid/errors/it/ERR_FTP_NOT_FOUND /usr/share/squid/errors/it/ERR_FTP_PUT_CREATED /usr/share/squid/errors/it/ERR_FTP_PUT_ERROR /usr/share/squid/errors/it/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/it/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/it/ERR_GATEWAY_FAILURE /usr/share/squid/errors/it/ERR_ICAP_FAILURE /usr/share/squid/errors/it/ERR_INVALID_REQ /usr/share/squid/errors/it/ERR_INVALID_RESP /usr/share/squid/errors/it/ERR_INVALID_URL /usr/share/squid/errors/it/ERR_LIFETIME_EXP /usr/share/squid/errors/it/ERR_NO_RELAY /usr/share/squid/errors/it/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/it/ERR_PRECONDITION_FAILED /usr/share/squid/errors/it/ERR_READ_ERROR /usr/share/squid/errors/it/ERR_READ_TIMEOUT /usr/share/squid/errors/it/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/it/ERR_SHUTTING_DOWN /usr/share/squid/errors/it/ERR_SOCKET_FAILURE /usr/share/squid/errors/it/ERR_TOO_BIG /usr/share/squid/errors/it/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/it/ERR_UNSUP_REQ /usr/share/squid/errors/it/ERR_URN_RESOLVE /usr/share/squid/errors/it/ERR_WRITE_ERROR /usr/share/squid/errors/it/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/it/error-details.txt /usr/share/squid/errors/ja /usr/share/squid/errors/ja-jp /usr/share/squid/errors/ja/ERR_ACCESS_DENIED /usr/share/squid/errors/ja/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/ja/ERR_AGENT_CONFIGURE /usr/share/squid/errors/ja/ERR_AGENT_WPAD /usr/share/squid/errors/ja/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/ja/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/ja/ERR_CANNOT_FORWARD /usr/share/squid/errors/ja/ERR_CONFLICT_HOST /usr/share/squid/errors/ja/ERR_CONNECT_FAIL /usr/share/squid/errors/ja/ERR_DIR_LISTING /usr/share/squid/errors/ja/ERR_DNS_FAIL /usr/share/squid/errors/ja/ERR_ESI /usr/share/squid/errors/ja/ERR_FORWARDING_DENIED /usr/share/squid/errors/ja/ERR_FTP_DISABLED /usr/share/squid/errors/ja/ERR_FTP_FAILURE /usr/share/squid/errors/ja/ERR_FTP_FORBIDDEN /usr/share/squid/errors/ja/ERR_FTP_NOT_FOUND /usr/share/squid/errors/ja/ERR_FTP_PUT_CREATED /usr/share/squid/errors/ja/ERR_FTP_PUT_ERROR /usr/share/squid/errors/ja/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/ja/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/ja/ERR_GATEWAY_FAILURE /usr/share/squid/errors/ja/ERR_ICAP_FAILURE /usr/share/squid/errors/ja/ERR_INVALID_REQ /usr/share/squid/errors/ja/ERR_INVALID_RESP /usr/share/squid/errors/ja/ERR_INVALID_URL /usr/share/squid/errors/ja/ERR_LIFETIME_EXP /usr/share/squid/errors/ja/ERR_NO_RELAY /usr/share/squid/errors/ja/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/ja/ERR_PRECONDITION_FAILED /usr/share/squid/errors/ja/ERR_READ_ERROR /usr/share/squid/errors/ja/ERR_READ_TIMEOUT /usr/share/squid/errors/ja/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/ja/ERR_SHUTTING_DOWN /usr/share/squid/errors/ja/ERR_SOCKET_FAILURE /usr/share/squid/errors/ja/ERR_TOO_BIG /usr/share/squid/errors/ja/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/ja/ERR_UNSUP_REQ /usr/share/squid/errors/ja/ERR_URN_RESOLVE /usr/share/squid/errors/ja/ERR_WRITE_ERROR /usr/share/squid/errors/ja/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/ja/error-details.txt /usr/share/squid/errors/ko /usr/share/squid/errors/ko-kp /usr/share/squid/errors/ko-kr /usr/share/squid/errors/ko/ERR_ACCESS_DENIED /usr/share/squid/errors/ko/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/ko/ERR_AGENT_CONFIGURE /usr/share/squid/errors/ko/ERR_AGENT_WPAD /usr/share/squid/errors/ko/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/ko/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/ko/ERR_CANNOT_FORWARD /usr/share/squid/errors/ko/ERR_CONFLICT_HOST /usr/share/squid/errors/ko/ERR_CONNECT_FAIL /usr/share/squid/errors/ko/ERR_DIR_LISTING /usr/share/squid/errors/ko/ERR_DNS_FAIL /usr/share/squid/errors/ko/ERR_ESI /usr/share/squid/errors/ko/ERR_FORWARDING_DENIED /usr/share/squid/errors/ko/ERR_FTP_DISABLED /usr/share/squid/errors/ko/ERR_FTP_FAILURE /usr/share/squid/errors/ko/ERR_FTP_FORBIDDEN /usr/share/squid/errors/ko/ERR_FTP_NOT_FOUND /usr/share/squid/errors/ko/ERR_FTP_PUT_CREATED /usr/share/squid/errors/ko/ERR_FTP_PUT_ERROR /usr/share/squid/errors/ko/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/ko/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/ko/ERR_GATEWAY_FAILURE /usr/share/squid/errors/ko/ERR_ICAP_FAILURE /usr/share/squid/errors/ko/ERR_INVALID_REQ /usr/share/squid/errors/ko/ERR_INVALID_RESP /usr/share/squid/errors/ko/ERR_INVALID_URL /usr/share/squid/errors/ko/ERR_LIFETIME_EXP /usr/share/squid/errors/ko/ERR_NO_RELAY /usr/share/squid/errors/ko/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/ko/ERR_PRECONDITION_FAILED /usr/share/squid/errors/ko/ERR_READ_ERROR /usr/share/squid/errors/ko/ERR_READ_TIMEOUT /usr/share/squid/errors/ko/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/ko/ERR_SHUTTING_DOWN /usr/share/squid/errors/ko/ERR_SOCKET_FAILURE /usr/share/squid/errors/ko/ERR_TOO_BIG /usr/share/squid/errors/ko/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/ko/ERR_UNSUP_REQ /usr/share/squid/errors/ko/ERR_URN_RESOLVE /usr/share/squid/errors/ko/ERR_WRITE_ERROR /usr/share/squid/errors/ko/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/ko/error-details.txt /usr/share/squid/errors/lt /usr/share/squid/errors/lt-lt /usr/share/squid/errors/lt/ERR_ACCESS_DENIED /usr/share/squid/errors/lt/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/lt/ERR_AGENT_CONFIGURE /usr/share/squid/errors/lt/ERR_AGENT_WPAD /usr/share/squid/errors/lt/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/lt/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/lt/ERR_CANNOT_FORWARD /usr/share/squid/errors/lt/ERR_CONFLICT_HOST /usr/share/squid/errors/lt/ERR_CONNECT_FAIL /usr/share/squid/errors/lt/ERR_DIR_LISTING /usr/share/squid/errors/lt/ERR_DNS_FAIL /usr/share/squid/errors/lt/ERR_ESI /usr/share/squid/errors/lt/ERR_FORWARDING_DENIED /usr/share/squid/errors/lt/ERR_FTP_DISABLED /usr/share/squid/errors/lt/ERR_FTP_FAILURE /usr/share/squid/errors/lt/ERR_FTP_FORBIDDEN /usr/share/squid/errors/lt/ERR_FTP_NOT_FOUND /usr/share/squid/errors/lt/ERR_FTP_PUT_CREATED /usr/share/squid/errors/lt/ERR_FTP_PUT_ERROR /usr/share/squid/errors/lt/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/lt/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/lt/ERR_GATEWAY_FAILURE /usr/share/squid/errors/lt/ERR_ICAP_FAILURE /usr/share/squid/errors/lt/ERR_INVALID_REQ /usr/share/squid/errors/lt/ERR_INVALID_RESP /usr/share/squid/errors/lt/ERR_INVALID_URL /usr/share/squid/errors/lt/ERR_LIFETIME_EXP /usr/share/squid/errors/lt/ERR_NO_RELAY /usr/share/squid/errors/lt/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/lt/ERR_PRECONDITION_FAILED /usr/share/squid/errors/lt/ERR_READ_ERROR /usr/share/squid/errors/lt/ERR_READ_TIMEOUT /usr/share/squid/errors/lt/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/lt/ERR_SHUTTING_DOWN /usr/share/squid/errors/lt/ERR_SOCKET_FAILURE /usr/share/squid/errors/lt/ERR_TOO_BIG /usr/share/squid/errors/lt/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/lt/ERR_UNSUP_REQ /usr/share/squid/errors/lt/ERR_URN_RESOLVE /usr/share/squid/errors/lt/ERR_WRITE_ERROR /usr/share/squid/errors/lt/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/lt/error-details.txt /usr/share/squid/errors/lv /usr/share/squid/errors/lv-lv /usr/share/squid/errors/lv/ERR_ACCESS_DENIED /usr/share/squid/errors/lv/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/lv/ERR_AGENT_CONFIGURE /usr/share/squid/errors/lv/ERR_AGENT_WPAD /usr/share/squid/errors/lv/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/lv/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/lv/ERR_CANNOT_FORWARD /usr/share/squid/errors/lv/ERR_CONFLICT_HOST /usr/share/squid/errors/lv/ERR_CONNECT_FAIL /usr/share/squid/errors/lv/ERR_DIR_LISTING /usr/share/squid/errors/lv/ERR_DNS_FAIL /usr/share/squid/errors/lv/ERR_ESI /usr/share/squid/errors/lv/ERR_FORWARDING_DENIED /usr/share/squid/errors/lv/ERR_FTP_DISABLED /usr/share/squid/errors/lv/ERR_FTP_FAILURE /usr/share/squid/errors/lv/ERR_FTP_FORBIDDEN /usr/share/squid/errors/lv/ERR_FTP_NOT_FOUND /usr/share/squid/errors/lv/ERR_FTP_PUT_CREATED /usr/share/squid/errors/lv/ERR_FTP_PUT_ERROR /usr/share/squid/errors/lv/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/lv/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/lv/ERR_GATEWAY_FAILURE /usr/share/squid/errors/lv/ERR_ICAP_FAILURE /usr/share/squid/errors/lv/ERR_INVALID_REQ /usr/share/squid/errors/lv/ERR_INVALID_RESP /usr/share/squid/errors/lv/ERR_INVALID_URL /usr/share/squid/errors/lv/ERR_LIFETIME_EXP /usr/share/squid/errors/lv/ERR_NO_RELAY /usr/share/squid/errors/lv/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/lv/ERR_PRECONDITION_FAILED /usr/share/squid/errors/lv/ERR_READ_ERROR /usr/share/squid/errors/lv/ERR_READ_TIMEOUT /usr/share/squid/errors/lv/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/lv/ERR_SHUTTING_DOWN /usr/share/squid/errors/lv/ERR_SOCKET_FAILURE /usr/share/squid/errors/lv/ERR_TOO_BIG /usr/share/squid/errors/lv/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/lv/ERR_UNSUP_REQ /usr/share/squid/errors/lv/ERR_URN_RESOLVE /usr/share/squid/errors/lv/ERR_WRITE_ERROR /usr/share/squid/errors/lv/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/lv/error-details.txt /usr/share/squid/errors/ms /usr/share/squid/errors/ms-my /usr/share/squid/errors/ms/ERR_ACCESS_DENIED /usr/share/squid/errors/ms/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/ms/ERR_AGENT_CONFIGURE /usr/share/squid/errors/ms/ERR_AGENT_WPAD /usr/share/squid/errors/ms/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/ms/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/ms/ERR_CANNOT_FORWARD /usr/share/squid/errors/ms/ERR_CONFLICT_HOST /usr/share/squid/errors/ms/ERR_CONNECT_FAIL /usr/share/squid/errors/ms/ERR_DIR_LISTING /usr/share/squid/errors/ms/ERR_DNS_FAIL /usr/share/squid/errors/ms/ERR_ESI /usr/share/squid/errors/ms/ERR_FORWARDING_DENIED /usr/share/squid/errors/ms/ERR_FTP_DISABLED /usr/share/squid/errors/ms/ERR_FTP_FAILURE /usr/share/squid/errors/ms/ERR_FTP_FORBIDDEN /usr/share/squid/errors/ms/ERR_FTP_NOT_FOUND /usr/share/squid/errors/ms/ERR_FTP_PUT_CREATED /usr/share/squid/errors/ms/ERR_FTP_PUT_ERROR /usr/share/squid/errors/ms/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/ms/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/ms/ERR_GATEWAY_FAILURE /usr/share/squid/errors/ms/ERR_ICAP_FAILURE /usr/share/squid/errors/ms/ERR_INVALID_REQ /usr/share/squid/errors/ms/ERR_INVALID_RESP /usr/share/squid/errors/ms/ERR_INVALID_URL /usr/share/squid/errors/ms/ERR_LIFETIME_EXP /usr/share/squid/errors/ms/ERR_NO_RELAY /usr/share/squid/errors/ms/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/ms/ERR_PRECONDITION_FAILED /usr/share/squid/errors/ms/ERR_READ_ERROR /usr/share/squid/errors/ms/ERR_READ_TIMEOUT /usr/share/squid/errors/ms/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/ms/ERR_SHUTTING_DOWN /usr/share/squid/errors/ms/ERR_SOCKET_FAILURE /usr/share/squid/errors/ms/ERR_TOO_BIG /usr/share/squid/errors/ms/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/ms/ERR_UNSUP_REQ /usr/share/squid/errors/ms/ERR_URN_RESOLVE /usr/share/squid/errors/ms/ERR_WRITE_ERROR /usr/share/squid/errors/ms/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/ms/error-details.txt /usr/share/squid/errors/nl /usr/share/squid/errors/nl-nl /usr/share/squid/errors/nl/ERR_ACCESS_DENIED /usr/share/squid/errors/nl/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/nl/ERR_AGENT_CONFIGURE /usr/share/squid/errors/nl/ERR_AGENT_WPAD /usr/share/squid/errors/nl/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/nl/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/nl/ERR_CANNOT_FORWARD /usr/share/squid/errors/nl/ERR_CONFLICT_HOST /usr/share/squid/errors/nl/ERR_CONNECT_FAIL /usr/share/squid/errors/nl/ERR_DIR_LISTING /usr/share/squid/errors/nl/ERR_DNS_FAIL /usr/share/squid/errors/nl/ERR_ESI /usr/share/squid/errors/nl/ERR_FORWARDING_DENIED /usr/share/squid/errors/nl/ERR_FTP_DISABLED /usr/share/squid/errors/nl/ERR_FTP_FAILURE /usr/share/squid/errors/nl/ERR_FTP_FORBIDDEN /usr/share/squid/errors/nl/ERR_FTP_NOT_FOUND /usr/share/squid/errors/nl/ERR_FTP_PUT_CREATED /usr/share/squid/errors/nl/ERR_FTP_PUT_ERROR /usr/share/squid/errors/nl/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/nl/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/nl/ERR_GATEWAY_FAILURE /usr/share/squid/errors/nl/ERR_ICAP_FAILURE /usr/share/squid/errors/nl/ERR_INVALID_REQ /usr/share/squid/errors/nl/ERR_INVALID_RESP /usr/share/squid/errors/nl/ERR_INVALID_URL /usr/share/squid/errors/nl/ERR_LIFETIME_EXP /usr/share/squid/errors/nl/ERR_NO_RELAY /usr/share/squid/errors/nl/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/nl/ERR_PRECONDITION_FAILED /usr/share/squid/errors/nl/ERR_READ_ERROR /usr/share/squid/errors/nl/ERR_READ_TIMEOUT /usr/share/squid/errors/nl/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/nl/ERR_SHUTTING_DOWN /usr/share/squid/errors/nl/ERR_SOCKET_FAILURE /usr/share/squid/errors/nl/ERR_TOO_BIG /usr/share/squid/errors/nl/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/nl/ERR_UNSUP_REQ /usr/share/squid/errors/nl/ERR_URN_RESOLVE /usr/share/squid/errors/nl/ERR_WRITE_ERROR /usr/share/squid/errors/nl/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/nl/error-details.txt /usr/share/squid/errors/oc /usr/share/squid/errors/oc/ERR_ACCESS_DENIED /usr/share/squid/errors/oc/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/oc/ERR_AGENT_CONFIGURE /usr/share/squid/errors/oc/ERR_AGENT_WPAD /usr/share/squid/errors/oc/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/oc/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/oc/ERR_CANNOT_FORWARD /usr/share/squid/errors/oc/ERR_CONFLICT_HOST /usr/share/squid/errors/oc/ERR_CONNECT_FAIL /usr/share/squid/errors/oc/ERR_DIR_LISTING /usr/share/squid/errors/oc/ERR_DNS_FAIL /usr/share/squid/errors/oc/ERR_ESI /usr/share/squid/errors/oc/ERR_FORWARDING_DENIED /usr/share/squid/errors/oc/ERR_FTP_DISABLED /usr/share/squid/errors/oc/ERR_FTP_FAILURE /usr/share/squid/errors/oc/ERR_FTP_FORBIDDEN /usr/share/squid/errors/oc/ERR_FTP_NOT_FOUND /usr/share/squid/errors/oc/ERR_FTP_PUT_CREATED /usr/share/squid/errors/oc/ERR_FTP_PUT_ERROR /usr/share/squid/errors/oc/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/oc/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/oc/ERR_GATEWAY_FAILURE /usr/share/squid/errors/oc/ERR_ICAP_FAILURE /usr/share/squid/errors/oc/ERR_INVALID_REQ /usr/share/squid/errors/oc/ERR_INVALID_RESP /usr/share/squid/errors/oc/ERR_INVALID_URL /usr/share/squid/errors/oc/ERR_LIFETIME_EXP /usr/share/squid/errors/oc/ERR_NO_RELAY /usr/share/squid/errors/oc/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/oc/ERR_PRECONDITION_FAILED /usr/share/squid/errors/oc/ERR_READ_ERROR /usr/share/squid/errors/oc/ERR_READ_TIMEOUT /usr/share/squid/errors/oc/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/oc/ERR_SHUTTING_DOWN /usr/share/squid/errors/oc/ERR_SOCKET_FAILURE /usr/share/squid/errors/oc/ERR_TOO_BIG /usr/share/squid/errors/oc/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/oc/ERR_UNSUP_REQ /usr/share/squid/errors/oc/ERR_URN_RESOLVE /usr/share/squid/errors/oc/ERR_WRITE_ERROR /usr/share/squid/errors/oc/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/oc/error-details.txt /usr/share/squid/errors/pl /usr/share/squid/errors/pl-pl /usr/share/squid/errors/pl/ERR_ACCESS_DENIED /usr/share/squid/errors/pl/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/pl/ERR_AGENT_CONFIGURE /usr/share/squid/errors/pl/ERR_AGENT_WPAD /usr/share/squid/errors/pl/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/pl/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/pl/ERR_CANNOT_FORWARD /usr/share/squid/errors/pl/ERR_CONFLICT_HOST /usr/share/squid/errors/pl/ERR_CONNECT_FAIL /usr/share/squid/errors/pl/ERR_DIR_LISTING /usr/share/squid/errors/pl/ERR_DNS_FAIL /usr/share/squid/errors/pl/ERR_ESI /usr/share/squid/errors/pl/ERR_FORWARDING_DENIED /usr/share/squid/errors/pl/ERR_FTP_DISABLED /usr/share/squid/errors/pl/ERR_FTP_FAILURE /usr/share/squid/errors/pl/ERR_FTP_FORBIDDEN /usr/share/squid/errors/pl/ERR_FTP_NOT_FOUND /usr/share/squid/errors/pl/ERR_FTP_PUT_CREATED /usr/share/squid/errors/pl/ERR_FTP_PUT_ERROR /usr/share/squid/errors/pl/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/pl/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/pl/ERR_GATEWAY_FAILURE /usr/share/squid/errors/pl/ERR_ICAP_FAILURE /usr/share/squid/errors/pl/ERR_INVALID_REQ /usr/share/squid/errors/pl/ERR_INVALID_RESP /usr/share/squid/errors/pl/ERR_INVALID_URL /usr/share/squid/errors/pl/ERR_LIFETIME_EXP /usr/share/squid/errors/pl/ERR_NO_RELAY /usr/share/squid/errors/pl/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/pl/ERR_PRECONDITION_FAILED /usr/share/squid/errors/pl/ERR_READ_ERROR /usr/share/squid/errors/pl/ERR_READ_TIMEOUT /usr/share/squid/errors/pl/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/pl/ERR_SHUTTING_DOWN /usr/share/squid/errors/pl/ERR_SOCKET_FAILURE /usr/share/squid/errors/pl/ERR_TOO_BIG /usr/share/squid/errors/pl/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/pl/ERR_UNSUP_REQ /usr/share/squid/errors/pl/ERR_URN_RESOLVE /usr/share/squid/errors/pl/ERR_WRITE_ERROR /usr/share/squid/errors/pl/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/pl/error-details.txt /usr/share/squid/errors/pt /usr/share/squid/errors/pt-br /usr/share/squid/errors/pt-br/ERR_ACCESS_DENIED /usr/share/squid/errors/pt-br/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/pt-br/ERR_AGENT_CONFIGURE /usr/share/squid/errors/pt-br/ERR_AGENT_WPAD /usr/share/squid/errors/pt-br/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/pt-br/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/pt-br/ERR_CANNOT_FORWARD /usr/share/squid/errors/pt-br/ERR_CONFLICT_HOST /usr/share/squid/errors/pt-br/ERR_CONNECT_FAIL /usr/share/squid/errors/pt-br/ERR_DIR_LISTING /usr/share/squid/errors/pt-br/ERR_DNS_FAIL /usr/share/squid/errors/pt-br/ERR_ESI /usr/share/squid/errors/pt-br/ERR_FORWARDING_DENIED /usr/share/squid/errors/pt-br/ERR_FTP_DISABLED /usr/share/squid/errors/pt-br/ERR_FTP_FAILURE /usr/share/squid/errors/pt-br/ERR_FTP_FORBIDDEN /usr/share/squid/errors/pt-br/ERR_FTP_NOT_FOUND /usr/share/squid/errors/pt-br/ERR_FTP_PUT_CREATED /usr/share/squid/errors/pt-br/ERR_FTP_PUT_ERROR /usr/share/squid/errors/pt-br/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/pt-br/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/pt-br/ERR_GATEWAY_FAILURE /usr/share/squid/errors/pt-br/ERR_ICAP_FAILURE /usr/share/squid/errors/pt-br/ERR_INVALID_REQ /usr/share/squid/errors/pt-br/ERR_INVALID_RESP /usr/share/squid/errors/pt-br/ERR_INVALID_URL /usr/share/squid/errors/pt-br/ERR_LIFETIME_EXP /usr/share/squid/errors/pt-br/ERR_NO_RELAY /usr/share/squid/errors/pt-br/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/pt-br/ERR_PRECONDITION_FAILED /usr/share/squid/errors/pt-br/ERR_READ_ERROR /usr/share/squid/errors/pt-br/ERR_READ_TIMEOUT /usr/share/squid/errors/pt-br/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/pt-br/ERR_SHUTTING_DOWN /usr/share/squid/errors/pt-br/ERR_SOCKET_FAILURE /usr/share/squid/errors/pt-br/ERR_TOO_BIG /usr/share/squid/errors/pt-br/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/pt-br/ERR_UNSUP_REQ /usr/share/squid/errors/pt-br/ERR_URN_RESOLVE /usr/share/squid/errors/pt-br/ERR_WRITE_ERROR /usr/share/squid/errors/pt-br/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/pt-br/error-details.txt /usr/share/squid/errors/pt-pt /usr/share/squid/errors/pt/ERR_ACCESS_DENIED /usr/share/squid/errors/pt/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/pt/ERR_AGENT_CONFIGURE /usr/share/squid/errors/pt/ERR_AGENT_WPAD /usr/share/squid/errors/pt/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/pt/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/pt/ERR_CANNOT_FORWARD /usr/share/squid/errors/pt/ERR_CONFLICT_HOST /usr/share/squid/errors/pt/ERR_CONNECT_FAIL /usr/share/squid/errors/pt/ERR_DIR_LISTING /usr/share/squid/errors/pt/ERR_DNS_FAIL /usr/share/squid/errors/pt/ERR_ESI /usr/share/squid/errors/pt/ERR_FORWARDING_DENIED /usr/share/squid/errors/pt/ERR_FTP_DISABLED /usr/share/squid/errors/pt/ERR_FTP_FAILURE /usr/share/squid/errors/pt/ERR_FTP_FORBIDDEN /usr/share/squid/errors/pt/ERR_FTP_NOT_FOUND /usr/share/squid/errors/pt/ERR_FTP_PUT_CREATED /usr/share/squid/errors/pt/ERR_FTP_PUT_ERROR /usr/share/squid/errors/pt/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/pt/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/pt/ERR_GATEWAY_FAILURE /usr/share/squid/errors/pt/ERR_ICAP_FAILURE /usr/share/squid/errors/pt/ERR_INVALID_REQ /usr/share/squid/errors/pt/ERR_INVALID_RESP /usr/share/squid/errors/pt/ERR_INVALID_URL /usr/share/squid/errors/pt/ERR_LIFETIME_EXP /usr/share/squid/errors/pt/ERR_NO_RELAY /usr/share/squid/errors/pt/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/pt/ERR_PRECONDITION_FAILED /usr/share/squid/errors/pt/ERR_READ_ERROR /usr/share/squid/errors/pt/ERR_READ_TIMEOUT /usr/share/squid/errors/pt/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/pt/ERR_SHUTTING_DOWN /usr/share/squid/errors/pt/ERR_SOCKET_FAILURE /usr/share/squid/errors/pt/ERR_TOO_BIG /usr/share/squid/errors/pt/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/pt/ERR_UNSUP_REQ /usr/share/squid/errors/pt/ERR_URN_RESOLVE /usr/share/squid/errors/pt/ERR_WRITE_ERROR /usr/share/squid/errors/pt/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/pt/error-details.txt /usr/share/squid/errors/ro /usr/share/squid/errors/ro-md /usr/share/squid/errors/ro-ro /usr/share/squid/errors/ro/ERR_ACCESS_DENIED /usr/share/squid/errors/ro/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/ro/ERR_AGENT_CONFIGURE /usr/share/squid/errors/ro/ERR_AGENT_WPAD /usr/share/squid/errors/ro/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/ro/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/ro/ERR_CANNOT_FORWARD /usr/share/squid/errors/ro/ERR_CONFLICT_HOST /usr/share/squid/errors/ro/ERR_CONNECT_FAIL /usr/share/squid/errors/ro/ERR_DIR_LISTING /usr/share/squid/errors/ro/ERR_DNS_FAIL /usr/share/squid/errors/ro/ERR_ESI /usr/share/squid/errors/ro/ERR_FORWARDING_DENIED /usr/share/squid/errors/ro/ERR_FTP_DISABLED /usr/share/squid/errors/ro/ERR_FTP_FAILURE /usr/share/squid/errors/ro/ERR_FTP_FORBIDDEN /usr/share/squid/errors/ro/ERR_FTP_NOT_FOUND /usr/share/squid/errors/ro/ERR_FTP_PUT_CREATED /usr/share/squid/errors/ro/ERR_FTP_PUT_ERROR /usr/share/squid/errors/ro/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/ro/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/ro/ERR_GATEWAY_FAILURE /usr/share/squid/errors/ro/ERR_ICAP_FAILURE /usr/share/squid/errors/ro/ERR_INVALID_REQ /usr/share/squid/errors/ro/ERR_INVALID_RESP /usr/share/squid/errors/ro/ERR_INVALID_URL /usr/share/squid/errors/ro/ERR_LIFETIME_EXP /usr/share/squid/errors/ro/ERR_NO_RELAY /usr/share/squid/errors/ro/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/ro/ERR_PRECONDITION_FAILED /usr/share/squid/errors/ro/ERR_READ_ERROR /usr/share/squid/errors/ro/ERR_READ_TIMEOUT /usr/share/squid/errors/ro/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/ro/ERR_SHUTTING_DOWN /usr/share/squid/errors/ro/ERR_SOCKET_FAILURE /usr/share/squid/errors/ro/ERR_TOO_BIG /usr/share/squid/errors/ro/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/ro/ERR_UNSUP_REQ /usr/share/squid/errors/ro/ERR_URN_RESOLVE /usr/share/squid/errors/ro/ERR_WRITE_ERROR /usr/share/squid/errors/ro/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/ro/error-details.txt /usr/share/squid/errors/ru /usr/share/squid/errors/ru-ru /usr/share/squid/errors/ru/ERR_ACCESS_DENIED /usr/share/squid/errors/ru/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/ru/ERR_AGENT_CONFIGURE /usr/share/squid/errors/ru/ERR_AGENT_WPAD /usr/share/squid/errors/ru/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/ru/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/ru/ERR_CANNOT_FORWARD /usr/share/squid/errors/ru/ERR_CONFLICT_HOST /usr/share/squid/errors/ru/ERR_CONNECT_FAIL /usr/share/squid/errors/ru/ERR_DIR_LISTING /usr/share/squid/errors/ru/ERR_DNS_FAIL /usr/share/squid/errors/ru/ERR_ESI /usr/share/squid/errors/ru/ERR_FORWARDING_DENIED /usr/share/squid/errors/ru/ERR_FTP_DISABLED /usr/share/squid/errors/ru/ERR_FTP_FAILURE /usr/share/squid/errors/ru/ERR_FTP_FORBIDDEN /usr/share/squid/errors/ru/ERR_FTP_NOT_FOUND /usr/share/squid/errors/ru/ERR_FTP_PUT_CREATED /usr/share/squid/errors/ru/ERR_FTP_PUT_ERROR /usr/share/squid/errors/ru/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/ru/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/ru/ERR_GATEWAY_FAILURE /usr/share/squid/errors/ru/ERR_ICAP_FAILURE /usr/share/squid/errors/ru/ERR_INVALID_REQ /usr/share/squid/errors/ru/ERR_INVALID_RESP /usr/share/squid/errors/ru/ERR_INVALID_URL /usr/share/squid/errors/ru/ERR_LIFETIME_EXP /usr/share/squid/errors/ru/ERR_NO_RELAY /usr/share/squid/errors/ru/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/ru/ERR_PRECONDITION_FAILED /usr/share/squid/errors/ru/ERR_READ_ERROR /usr/share/squid/errors/ru/ERR_READ_TIMEOUT /usr/share/squid/errors/ru/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/ru/ERR_SHUTTING_DOWN /usr/share/squid/errors/ru/ERR_SOCKET_FAILURE /usr/share/squid/errors/ru/ERR_TOO_BIG /usr/share/squid/errors/ru/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/ru/ERR_UNSUP_REQ /usr/share/squid/errors/ru/ERR_URN_RESOLVE /usr/share/squid/errors/ru/ERR_WRITE_ERROR /usr/share/squid/errors/ru/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/ru/error-details.txt /usr/share/squid/errors/sk /usr/share/squid/errors/sk-sk /usr/share/squid/errors/sk/ERR_ACCESS_DENIED /usr/share/squid/errors/sk/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/sk/ERR_AGENT_CONFIGURE /usr/share/squid/errors/sk/ERR_AGENT_WPAD /usr/share/squid/errors/sk/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/sk/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/sk/ERR_CANNOT_FORWARD /usr/share/squid/errors/sk/ERR_CONFLICT_HOST /usr/share/squid/errors/sk/ERR_CONNECT_FAIL /usr/share/squid/errors/sk/ERR_DIR_LISTING /usr/share/squid/errors/sk/ERR_DNS_FAIL /usr/share/squid/errors/sk/ERR_ESI /usr/share/squid/errors/sk/ERR_FORWARDING_DENIED /usr/share/squid/errors/sk/ERR_FTP_DISABLED /usr/share/squid/errors/sk/ERR_FTP_FAILURE /usr/share/squid/errors/sk/ERR_FTP_FORBIDDEN /usr/share/squid/errors/sk/ERR_FTP_NOT_FOUND /usr/share/squid/errors/sk/ERR_FTP_PUT_CREATED /usr/share/squid/errors/sk/ERR_FTP_PUT_ERROR /usr/share/squid/errors/sk/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/sk/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/sk/ERR_GATEWAY_FAILURE /usr/share/squid/errors/sk/ERR_ICAP_FAILURE /usr/share/squid/errors/sk/ERR_INVALID_REQ /usr/share/squid/errors/sk/ERR_INVALID_RESP /usr/share/squid/errors/sk/ERR_INVALID_URL /usr/share/squid/errors/sk/ERR_LIFETIME_EXP /usr/share/squid/errors/sk/ERR_NO_RELAY /usr/share/squid/errors/sk/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/sk/ERR_PRECONDITION_FAILED /usr/share/squid/errors/sk/ERR_READ_ERROR /usr/share/squid/errors/sk/ERR_READ_TIMEOUT /usr/share/squid/errors/sk/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/sk/ERR_SHUTTING_DOWN /usr/share/squid/errors/sk/ERR_SOCKET_FAILURE /usr/share/squid/errors/sk/ERR_TOO_BIG /usr/share/squid/errors/sk/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/sk/ERR_UNSUP_REQ /usr/share/squid/errors/sk/ERR_URN_RESOLVE /usr/share/squid/errors/sk/ERR_WRITE_ERROR /usr/share/squid/errors/sk/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/sk/error-details.txt /usr/share/squid/errors/sl /usr/share/squid/errors/sl-si /usr/share/squid/errors/sl/ERR_ACCESS_DENIED /usr/share/squid/errors/sl/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/sl/ERR_AGENT_CONFIGURE /usr/share/squid/errors/sl/ERR_AGENT_WPAD /usr/share/squid/errors/sl/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/sl/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/sl/ERR_CANNOT_FORWARD /usr/share/squid/errors/sl/ERR_CONFLICT_HOST /usr/share/squid/errors/sl/ERR_CONNECT_FAIL /usr/share/squid/errors/sl/ERR_DIR_LISTING /usr/share/squid/errors/sl/ERR_DNS_FAIL /usr/share/squid/errors/sl/ERR_ESI /usr/share/squid/errors/sl/ERR_FORWARDING_DENIED /usr/share/squid/errors/sl/ERR_FTP_DISABLED /usr/share/squid/errors/sl/ERR_FTP_FAILURE /usr/share/squid/errors/sl/ERR_FTP_FORBIDDEN /usr/share/squid/errors/sl/ERR_FTP_NOT_FOUND /usr/share/squid/errors/sl/ERR_FTP_PUT_CREATED /usr/share/squid/errors/sl/ERR_FTP_PUT_ERROR /usr/share/squid/errors/sl/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/sl/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/sl/ERR_GATEWAY_FAILURE /usr/share/squid/errors/sl/ERR_ICAP_FAILURE /usr/share/squid/errors/sl/ERR_INVALID_REQ /usr/share/squid/errors/sl/ERR_INVALID_RESP /usr/share/squid/errors/sl/ERR_INVALID_URL /usr/share/squid/errors/sl/ERR_LIFETIME_EXP /usr/share/squid/errors/sl/ERR_NO_RELAY /usr/share/squid/errors/sl/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/sl/ERR_PRECONDITION_FAILED /usr/share/squid/errors/sl/ERR_READ_ERROR /usr/share/squid/errors/sl/ERR_READ_TIMEOUT /usr/share/squid/errors/sl/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/sl/ERR_SHUTTING_DOWN /usr/share/squid/errors/sl/ERR_SOCKET_FAILURE /usr/share/squid/errors/sl/ERR_TOO_BIG /usr/share/squid/errors/sl/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/sl/ERR_UNSUP_REQ /usr/share/squid/errors/sl/ERR_URN_RESOLVE /usr/share/squid/errors/sl/ERR_WRITE_ERROR /usr/share/squid/errors/sl/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/sl/error-details.txt /usr/share/squid/errors/sr /usr/share/squid/errors/sr-cyrl /usr/share/squid/errors/sr-cyrl/ERR_ACCESS_DENIED /usr/share/squid/errors/sr-cyrl/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/sr-cyrl/ERR_AGENT_CONFIGURE /usr/share/squid/errors/sr-cyrl/ERR_AGENT_WPAD /usr/share/squid/errors/sr-cyrl/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/sr-cyrl/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/sr-cyrl/ERR_CANNOT_FORWARD /usr/share/squid/errors/sr-cyrl/ERR_CONFLICT_HOST /usr/share/squid/errors/sr-cyrl/ERR_CONNECT_FAIL /usr/share/squid/errors/sr-cyrl/ERR_DIR_LISTING /usr/share/squid/errors/sr-cyrl/ERR_DNS_FAIL /usr/share/squid/errors/sr-cyrl/ERR_ESI /usr/share/squid/errors/sr-cyrl/ERR_FORWARDING_DENIED /usr/share/squid/errors/sr-cyrl/ERR_FTP_DISABLED /usr/share/squid/errors/sr-cyrl/ERR_FTP_FAILURE /usr/share/squid/errors/sr-cyrl/ERR_FTP_FORBIDDEN /usr/share/squid/errors/sr-cyrl/ERR_FTP_NOT_FOUND /usr/share/squid/errors/sr-cyrl/ERR_FTP_PUT_CREATED /usr/share/squid/errors/sr-cyrl/ERR_FTP_PUT_ERROR /usr/share/squid/errors/sr-cyrl/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/sr-cyrl/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/sr-cyrl/ERR_GATEWAY_FAILURE /usr/share/squid/errors/sr-cyrl/ERR_ICAP_FAILURE /usr/share/squid/errors/sr-cyrl/ERR_INVALID_REQ /usr/share/squid/errors/sr-cyrl/ERR_INVALID_RESP /usr/share/squid/errors/sr-cyrl/ERR_INVALID_URL /usr/share/squid/errors/sr-cyrl/ERR_LIFETIME_EXP /usr/share/squid/errors/sr-cyrl/ERR_NO_RELAY /usr/share/squid/errors/sr-cyrl/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/sr-cyrl/ERR_PRECONDITION_FAILED /usr/share/squid/errors/sr-cyrl/ERR_READ_ERROR /usr/share/squid/errors/sr-cyrl/ERR_READ_TIMEOUT /usr/share/squid/errors/sr-cyrl/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/sr-cyrl/ERR_SHUTTING_DOWN /usr/share/squid/errors/sr-cyrl/ERR_SOCKET_FAILURE /usr/share/squid/errors/sr-cyrl/ERR_TOO_BIG /usr/share/squid/errors/sr-cyrl/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/sr-cyrl/ERR_UNSUP_REQ /usr/share/squid/errors/sr-cyrl/ERR_URN_RESOLVE /usr/share/squid/errors/sr-cyrl/ERR_WRITE_ERROR /usr/share/squid/errors/sr-cyrl/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/sr-cyrl/error-details.txt /usr/share/squid/errors/sr-latn /usr/share/squid/errors/sr-latn-cs /usr/share/squid/errors/sr-latn/ERR_ACCESS_DENIED /usr/share/squid/errors/sr-latn/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/sr-latn/ERR_AGENT_CONFIGURE /usr/share/squid/errors/sr-latn/ERR_AGENT_WPAD /usr/share/squid/errors/sr-latn/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/sr-latn/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/sr-latn/ERR_CANNOT_FORWARD /usr/share/squid/errors/sr-latn/ERR_CONFLICT_HOST /usr/share/squid/errors/sr-latn/ERR_CONNECT_FAIL /usr/share/squid/errors/sr-latn/ERR_DIR_LISTING /usr/share/squid/errors/sr-latn/ERR_DNS_FAIL /usr/share/squid/errors/sr-latn/ERR_ESI /usr/share/squid/errors/sr-latn/ERR_FORWARDING_DENIED /usr/share/squid/errors/sr-latn/ERR_FTP_DISABLED /usr/share/squid/errors/sr-latn/ERR_FTP_FAILURE /usr/share/squid/errors/sr-latn/ERR_FTP_FORBIDDEN /usr/share/squid/errors/sr-latn/ERR_FTP_NOT_FOUND /usr/share/squid/errors/sr-latn/ERR_FTP_PUT_CREATED /usr/share/squid/errors/sr-latn/ERR_FTP_PUT_ERROR /usr/share/squid/errors/sr-latn/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/sr-latn/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/sr-latn/ERR_GATEWAY_FAILURE /usr/share/squid/errors/sr-latn/ERR_ICAP_FAILURE /usr/share/squid/errors/sr-latn/ERR_INVALID_REQ /usr/share/squid/errors/sr-latn/ERR_INVALID_RESP /usr/share/squid/errors/sr-latn/ERR_INVALID_URL /usr/share/squid/errors/sr-latn/ERR_LIFETIME_EXP /usr/share/squid/errors/sr-latn/ERR_NO_RELAY /usr/share/squid/errors/sr-latn/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/sr-latn/ERR_PRECONDITION_FAILED /usr/share/squid/errors/sr-latn/ERR_READ_ERROR /usr/share/squid/errors/sr-latn/ERR_READ_TIMEOUT /usr/share/squid/errors/sr-latn/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/sr-latn/ERR_SHUTTING_DOWN /usr/share/squid/errors/sr-latn/ERR_SOCKET_FAILURE /usr/share/squid/errors/sr-latn/ERR_TOO_BIG /usr/share/squid/errors/sr-latn/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/sr-latn/ERR_UNSUP_REQ /usr/share/squid/errors/sr-latn/ERR_URN_RESOLVE /usr/share/squid/errors/sr-latn/ERR_WRITE_ERROR /usr/share/squid/errors/sr-latn/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/sr-latn/error-details.txt /usr/share/squid/errors/sr-sp /usr/share/squid/errors/sv /usr/share/squid/errors/sv-fi /usr/share/squid/errors/sv-se /usr/share/squid/errors/sv/ERR_ACCESS_DENIED /usr/share/squid/errors/sv/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/sv/ERR_AGENT_CONFIGURE /usr/share/squid/errors/sv/ERR_AGENT_WPAD /usr/share/squid/errors/sv/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/sv/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/sv/ERR_CANNOT_FORWARD /usr/share/squid/errors/sv/ERR_CONFLICT_HOST /usr/share/squid/errors/sv/ERR_CONNECT_FAIL /usr/share/squid/errors/sv/ERR_DIR_LISTING /usr/share/squid/errors/sv/ERR_DNS_FAIL /usr/share/squid/errors/sv/ERR_ESI /usr/share/squid/errors/sv/ERR_FORWARDING_DENIED /usr/share/squid/errors/sv/ERR_FTP_DISABLED /usr/share/squid/errors/sv/ERR_FTP_FAILURE /usr/share/squid/errors/sv/ERR_FTP_FORBIDDEN /usr/share/squid/errors/sv/ERR_FTP_NOT_FOUND /usr/share/squid/errors/sv/ERR_FTP_PUT_CREATED /usr/share/squid/errors/sv/ERR_FTP_PUT_ERROR /usr/share/squid/errors/sv/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/sv/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/sv/ERR_GATEWAY_FAILURE /usr/share/squid/errors/sv/ERR_ICAP_FAILURE /usr/share/squid/errors/sv/ERR_INVALID_REQ /usr/share/squid/errors/sv/ERR_INVALID_RESP /usr/share/squid/errors/sv/ERR_INVALID_URL /usr/share/squid/errors/sv/ERR_LIFETIME_EXP /usr/share/squid/errors/sv/ERR_NO_RELAY /usr/share/squid/errors/sv/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/sv/ERR_PRECONDITION_FAILED /usr/share/squid/errors/sv/ERR_READ_ERROR /usr/share/squid/errors/sv/ERR_READ_TIMEOUT /usr/share/squid/errors/sv/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/sv/ERR_SHUTTING_DOWN /usr/share/squid/errors/sv/ERR_SOCKET_FAILURE /usr/share/squid/errors/sv/ERR_TOO_BIG /usr/share/squid/errors/sv/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/sv/ERR_UNSUP_REQ /usr/share/squid/errors/sv/ERR_URN_RESOLVE /usr/share/squid/errors/sv/ERR_WRITE_ERROR /usr/share/squid/errors/sv/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/sv/error-details.txt /usr/share/squid/errors/templates /usr/share/squid/errors/templates/ERR_ACCESS_DENIED /usr/share/squid/errors/templates/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/templates/ERR_AGENT_CONFIGURE /usr/share/squid/errors/templates/ERR_AGENT_WPAD /usr/share/squid/errors/templates/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/templates/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/templates/ERR_CANNOT_FORWARD /usr/share/squid/errors/templates/ERR_CONFLICT_HOST /usr/share/squid/errors/templates/ERR_CONNECT_FAIL /usr/share/squid/errors/templates/ERR_DIR_LISTING /usr/share/squid/errors/templates/ERR_DNS_FAIL /usr/share/squid/errors/templates/ERR_ESI /usr/share/squid/errors/templates/ERR_FORWARDING_DENIED /usr/share/squid/errors/templates/ERR_FTP_DISABLED /usr/share/squid/errors/templates/ERR_FTP_FAILURE /usr/share/squid/errors/templates/ERR_FTP_FORBIDDEN /usr/share/squid/errors/templates/ERR_FTP_NOT_FOUND /usr/share/squid/errors/templates/ERR_FTP_PUT_CREATED /usr/share/squid/errors/templates/ERR_FTP_PUT_ERROR /usr/share/squid/errors/templates/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/templates/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/templates/ERR_GATEWAY_FAILURE /usr/share/squid/errors/templates/ERR_ICAP_FAILURE /usr/share/squid/errors/templates/ERR_INVALID_REQ /usr/share/squid/errors/templates/ERR_INVALID_RESP /usr/share/squid/errors/templates/ERR_INVALID_URL /usr/share/squid/errors/templates/ERR_LIFETIME_EXP /usr/share/squid/errors/templates/ERR_NO_RELAY /usr/share/squid/errors/templates/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/templates/ERR_PRECONDITION_FAILED /usr/share/squid/errors/templates/ERR_READ_ERROR /usr/share/squid/errors/templates/ERR_READ_TIMEOUT /usr/share/squid/errors/templates/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/templates/ERR_SHUTTING_DOWN /usr/share/squid/errors/templates/ERR_SOCKET_FAILURE /usr/share/squid/errors/templates/ERR_TOO_BIG /usr/share/squid/errors/templates/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/templates/ERR_UNSUP_REQ /usr/share/squid/errors/templates/ERR_URN_RESOLVE /usr/share/squid/errors/templates/ERR_WRITE_ERROR /usr/share/squid/errors/templates/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/templates/error-details.txt /usr/share/squid/errors/th /usr/share/squid/errors/th-th /usr/share/squid/errors/th/ERR_ACCESS_DENIED /usr/share/squid/errors/th/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/th/ERR_AGENT_CONFIGURE /usr/share/squid/errors/th/ERR_AGENT_WPAD /usr/share/squid/errors/th/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/th/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/th/ERR_CANNOT_FORWARD /usr/share/squid/errors/th/ERR_CONFLICT_HOST /usr/share/squid/errors/th/ERR_CONNECT_FAIL /usr/share/squid/errors/th/ERR_DIR_LISTING /usr/share/squid/errors/th/ERR_DNS_FAIL /usr/share/squid/errors/th/ERR_ESI /usr/share/squid/errors/th/ERR_FORWARDING_DENIED /usr/share/squid/errors/th/ERR_FTP_DISABLED /usr/share/squid/errors/th/ERR_FTP_FAILURE /usr/share/squid/errors/th/ERR_FTP_FORBIDDEN /usr/share/squid/errors/th/ERR_FTP_NOT_FOUND /usr/share/squid/errors/th/ERR_FTP_PUT_CREATED /usr/share/squid/errors/th/ERR_FTP_PUT_ERROR /usr/share/squid/errors/th/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/th/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/th/ERR_GATEWAY_FAILURE /usr/share/squid/errors/th/ERR_ICAP_FAILURE /usr/share/squid/errors/th/ERR_INVALID_REQ /usr/share/squid/errors/th/ERR_INVALID_RESP /usr/share/squid/errors/th/ERR_INVALID_URL /usr/share/squid/errors/th/ERR_LIFETIME_EXP /usr/share/squid/errors/th/ERR_NO_RELAY /usr/share/squid/errors/th/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/th/ERR_PRECONDITION_FAILED /usr/share/squid/errors/th/ERR_READ_ERROR /usr/share/squid/errors/th/ERR_READ_TIMEOUT /usr/share/squid/errors/th/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/th/ERR_SHUTTING_DOWN /usr/share/squid/errors/th/ERR_SOCKET_FAILURE /usr/share/squid/errors/th/ERR_TOO_BIG /usr/share/squid/errors/th/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/th/ERR_UNSUP_REQ /usr/share/squid/errors/th/ERR_URN_RESOLVE /usr/share/squid/errors/th/ERR_WRITE_ERROR /usr/share/squid/errors/th/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/th/error-details.txt /usr/share/squid/errors/tr /usr/share/squid/errors/tr-tr /usr/share/squid/errors/tr/ERR_ACCESS_DENIED /usr/share/squid/errors/tr/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/tr/ERR_AGENT_CONFIGURE /usr/share/squid/errors/tr/ERR_AGENT_WPAD /usr/share/squid/errors/tr/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/tr/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/tr/ERR_CANNOT_FORWARD /usr/share/squid/errors/tr/ERR_CONFLICT_HOST /usr/share/squid/errors/tr/ERR_CONNECT_FAIL /usr/share/squid/errors/tr/ERR_DIR_LISTING /usr/share/squid/errors/tr/ERR_DNS_FAIL /usr/share/squid/errors/tr/ERR_ESI /usr/share/squid/errors/tr/ERR_FORWARDING_DENIED /usr/share/squid/errors/tr/ERR_FTP_DISABLED /usr/share/squid/errors/tr/ERR_FTP_FAILURE /usr/share/squid/errors/tr/ERR_FTP_FORBIDDEN /usr/share/squid/errors/tr/ERR_FTP_NOT_FOUND /usr/share/squid/errors/tr/ERR_FTP_PUT_CREATED /usr/share/squid/errors/tr/ERR_FTP_PUT_ERROR /usr/share/squid/errors/tr/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/tr/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/tr/ERR_GATEWAY_FAILURE /usr/share/squid/errors/tr/ERR_ICAP_FAILURE /usr/share/squid/errors/tr/ERR_INVALID_REQ /usr/share/squid/errors/tr/ERR_INVALID_RESP /usr/share/squid/errors/tr/ERR_INVALID_URL /usr/share/squid/errors/tr/ERR_LIFETIME_EXP /usr/share/squid/errors/tr/ERR_NO_RELAY /usr/share/squid/errors/tr/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/tr/ERR_PRECONDITION_FAILED /usr/share/squid/errors/tr/ERR_READ_ERROR /usr/share/squid/errors/tr/ERR_READ_TIMEOUT /usr/share/squid/errors/tr/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/tr/ERR_SHUTTING_DOWN /usr/share/squid/errors/tr/ERR_SOCKET_FAILURE /usr/share/squid/errors/tr/ERR_TOO_BIG /usr/share/squid/errors/tr/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/tr/ERR_UNSUP_REQ /usr/share/squid/errors/tr/ERR_URN_RESOLVE /usr/share/squid/errors/tr/ERR_WRITE_ERROR /usr/share/squid/errors/tr/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/tr/error-details.txt /usr/share/squid/errors/uk /usr/share/squid/errors/uk-ua /usr/share/squid/errors/uk/ERR_ACCESS_DENIED /usr/share/squid/errors/uk/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/uk/ERR_AGENT_CONFIGURE /usr/share/squid/errors/uk/ERR_AGENT_WPAD /usr/share/squid/errors/uk/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/uk/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/uk/ERR_CANNOT_FORWARD /usr/share/squid/errors/uk/ERR_CONFLICT_HOST /usr/share/squid/errors/uk/ERR_CONNECT_FAIL /usr/share/squid/errors/uk/ERR_DIR_LISTING /usr/share/squid/errors/uk/ERR_DNS_FAIL /usr/share/squid/errors/uk/ERR_ESI /usr/share/squid/errors/uk/ERR_FORWARDING_DENIED /usr/share/squid/errors/uk/ERR_FTP_DISABLED /usr/share/squid/errors/uk/ERR_FTP_FAILURE /usr/share/squid/errors/uk/ERR_FTP_FORBIDDEN /usr/share/squid/errors/uk/ERR_FTP_NOT_FOUND /usr/share/squid/errors/uk/ERR_FTP_PUT_CREATED /usr/share/squid/errors/uk/ERR_FTP_PUT_ERROR /usr/share/squid/errors/uk/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/uk/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/uk/ERR_GATEWAY_FAILURE /usr/share/squid/errors/uk/ERR_ICAP_FAILURE /usr/share/squid/errors/uk/ERR_INVALID_REQ /usr/share/squid/errors/uk/ERR_INVALID_RESP /usr/share/squid/errors/uk/ERR_INVALID_URL /usr/share/squid/errors/uk/ERR_LIFETIME_EXP /usr/share/squid/errors/uk/ERR_NO_RELAY /usr/share/squid/errors/uk/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/uk/ERR_PRECONDITION_FAILED /usr/share/squid/errors/uk/ERR_READ_ERROR /usr/share/squid/errors/uk/ERR_READ_TIMEOUT /usr/share/squid/errors/uk/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/uk/ERR_SHUTTING_DOWN /usr/share/squid/errors/uk/ERR_SOCKET_FAILURE /usr/share/squid/errors/uk/ERR_TOO_BIG /usr/share/squid/errors/uk/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/uk/ERR_UNSUP_REQ /usr/share/squid/errors/uk/ERR_URN_RESOLVE /usr/share/squid/errors/uk/ERR_WRITE_ERROR /usr/share/squid/errors/uk/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/uk/error-details.txt /usr/share/squid/errors/uz /usr/share/squid/errors/uz/ERR_ACCESS_DENIED /usr/share/squid/errors/uz/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/uz/ERR_AGENT_CONFIGURE /usr/share/squid/errors/uz/ERR_AGENT_WPAD /usr/share/squid/errors/uz/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/uz/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/uz/ERR_CANNOT_FORWARD /usr/share/squid/errors/uz/ERR_CONFLICT_HOST /usr/share/squid/errors/uz/ERR_CONNECT_FAIL /usr/share/squid/errors/uz/ERR_DIR_LISTING /usr/share/squid/errors/uz/ERR_DNS_FAIL /usr/share/squid/errors/uz/ERR_ESI /usr/share/squid/errors/uz/ERR_FORWARDING_DENIED /usr/share/squid/errors/uz/ERR_FTP_DISABLED /usr/share/squid/errors/uz/ERR_FTP_FAILURE /usr/share/squid/errors/uz/ERR_FTP_FORBIDDEN /usr/share/squid/errors/uz/ERR_FTP_NOT_FOUND /usr/share/squid/errors/uz/ERR_FTP_PUT_CREATED /usr/share/squid/errors/uz/ERR_FTP_PUT_ERROR /usr/share/squid/errors/uz/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/uz/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/uz/ERR_GATEWAY_FAILURE /usr/share/squid/errors/uz/ERR_ICAP_FAILURE /usr/share/squid/errors/uz/ERR_INVALID_REQ /usr/share/squid/errors/uz/ERR_INVALID_RESP /usr/share/squid/errors/uz/ERR_INVALID_URL /usr/share/squid/errors/uz/ERR_LIFETIME_EXP /usr/share/squid/errors/uz/ERR_NO_RELAY /usr/share/squid/errors/uz/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/uz/ERR_PRECONDITION_FAILED /usr/share/squid/errors/uz/ERR_READ_ERROR /usr/share/squid/errors/uz/ERR_READ_TIMEOUT /usr/share/squid/errors/uz/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/uz/ERR_SHUTTING_DOWN /usr/share/squid/errors/uz/ERR_SOCKET_FAILURE /usr/share/squid/errors/uz/ERR_TOO_BIG /usr/share/squid/errors/uz/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/uz/ERR_UNSUP_REQ /usr/share/squid/errors/uz/ERR_URN_RESOLVE /usr/share/squid/errors/uz/ERR_WRITE_ERROR /usr/share/squid/errors/uz/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/uz/error-details.txt /usr/share/squid/errors/vi /usr/share/squid/errors/vi-vn /usr/share/squid/errors/vi/ERR_ACCESS_DENIED /usr/share/squid/errors/vi/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/vi/ERR_AGENT_CONFIGURE /usr/share/squid/errors/vi/ERR_AGENT_WPAD /usr/share/squid/errors/vi/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/vi/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/vi/ERR_CANNOT_FORWARD /usr/share/squid/errors/vi/ERR_CONFLICT_HOST /usr/share/squid/errors/vi/ERR_CONNECT_FAIL /usr/share/squid/errors/vi/ERR_DIR_LISTING /usr/share/squid/errors/vi/ERR_DNS_FAIL /usr/share/squid/errors/vi/ERR_ESI /usr/share/squid/errors/vi/ERR_FORWARDING_DENIED /usr/share/squid/errors/vi/ERR_FTP_DISABLED /usr/share/squid/errors/vi/ERR_FTP_FAILURE /usr/share/squid/errors/vi/ERR_FTP_FORBIDDEN /usr/share/squid/errors/vi/ERR_FTP_NOT_FOUND /usr/share/squid/errors/vi/ERR_FTP_PUT_CREATED /usr/share/squid/errors/vi/ERR_FTP_PUT_ERROR /usr/share/squid/errors/vi/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/vi/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/vi/ERR_GATEWAY_FAILURE /usr/share/squid/errors/vi/ERR_ICAP_FAILURE /usr/share/squid/errors/vi/ERR_INVALID_REQ /usr/share/squid/errors/vi/ERR_INVALID_RESP /usr/share/squid/errors/vi/ERR_INVALID_URL /usr/share/squid/errors/vi/ERR_LIFETIME_EXP /usr/share/squid/errors/vi/ERR_NO_RELAY /usr/share/squid/errors/vi/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/vi/ERR_PRECONDITION_FAILED /usr/share/squid/errors/vi/ERR_READ_ERROR /usr/share/squid/errors/vi/ERR_READ_TIMEOUT /usr/share/squid/errors/vi/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/vi/ERR_SHUTTING_DOWN /usr/share/squid/errors/vi/ERR_SOCKET_FAILURE /usr/share/squid/errors/vi/ERR_TOO_BIG /usr/share/squid/errors/vi/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/vi/ERR_UNSUP_REQ /usr/share/squid/errors/vi/ERR_URN_RESOLVE /usr/share/squid/errors/vi/ERR_WRITE_ERROR /usr/share/squid/errors/vi/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/vi/error-details.txt /usr/share/squid/errors/zh-cn /usr/share/squid/errors/zh-cn/ERR_ACCESS_DENIED /usr/share/squid/errors/zh-cn/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/zh-cn/ERR_AGENT_CONFIGURE /usr/share/squid/errors/zh-cn/ERR_AGENT_WPAD /usr/share/squid/errors/zh-cn/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/zh-cn/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/zh-cn/ERR_CANNOT_FORWARD /usr/share/squid/errors/zh-cn/ERR_CONFLICT_HOST /usr/share/squid/errors/zh-cn/ERR_CONNECT_FAIL /usr/share/squid/errors/zh-cn/ERR_DIR_LISTING /usr/share/squid/errors/zh-cn/ERR_DNS_FAIL /usr/share/squid/errors/zh-cn/ERR_ESI /usr/share/squid/errors/zh-cn/ERR_FORWARDING_DENIED /usr/share/squid/errors/zh-cn/ERR_FTP_DISABLED /usr/share/squid/errors/zh-cn/ERR_FTP_FAILURE /usr/share/squid/errors/zh-cn/ERR_FTP_FORBIDDEN /usr/share/squid/errors/zh-cn/ERR_FTP_NOT_FOUND /usr/share/squid/errors/zh-cn/ERR_FTP_PUT_CREATED /usr/share/squid/errors/zh-cn/ERR_FTP_PUT_ERROR /usr/share/squid/errors/zh-cn/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/zh-cn/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/zh-cn/ERR_GATEWAY_FAILURE /usr/share/squid/errors/zh-cn/ERR_ICAP_FAILURE /usr/share/squid/errors/zh-cn/ERR_INVALID_REQ /usr/share/squid/errors/zh-cn/ERR_INVALID_RESP /usr/share/squid/errors/zh-cn/ERR_INVALID_URL /usr/share/squid/errors/zh-cn/ERR_LIFETIME_EXP /usr/share/squid/errors/zh-cn/ERR_NO_RELAY /usr/share/squid/errors/zh-cn/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/zh-cn/ERR_PRECONDITION_FAILED /usr/share/squid/errors/zh-cn/ERR_READ_ERROR /usr/share/squid/errors/zh-cn/ERR_READ_TIMEOUT /usr/share/squid/errors/zh-cn/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/zh-cn/ERR_SHUTTING_DOWN /usr/share/squid/errors/zh-cn/ERR_SOCKET_FAILURE /usr/share/squid/errors/zh-cn/ERR_TOO_BIG /usr/share/squid/errors/zh-cn/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/zh-cn/ERR_UNSUP_REQ /usr/share/squid/errors/zh-cn/ERR_URN_RESOLVE /usr/share/squid/errors/zh-cn/ERR_WRITE_ERROR /usr/share/squid/errors/zh-cn/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/zh-cn/error-details.txt /usr/share/squid/errors/zh-hk /usr/share/squid/errors/zh-mo /usr/share/squid/errors/zh-sg /usr/share/squid/errors/zh-tw /usr/share/squid/errors/zh-tw/ERR_ACCESS_DENIED /usr/share/squid/errors/zh-tw/ERR_ACL_TIME_QUOTA_EXCEEDED /usr/share/squid/errors/zh-tw/ERR_AGENT_CONFIGURE /usr/share/squid/errors/zh-tw/ERR_AGENT_WPAD /usr/share/squid/errors/zh-tw/ERR_CACHE_ACCESS_DENIED /usr/share/squid/errors/zh-tw/ERR_CACHE_MGR_ACCESS_DENIED /usr/share/squid/errors/zh-tw/ERR_CANNOT_FORWARD /usr/share/squid/errors/zh-tw/ERR_CONFLICT_HOST /usr/share/squid/errors/zh-tw/ERR_CONNECT_FAIL /usr/share/squid/errors/zh-tw/ERR_DIR_LISTING /usr/share/squid/errors/zh-tw/ERR_DNS_FAIL /usr/share/squid/errors/zh-tw/ERR_ESI /usr/share/squid/errors/zh-tw/ERR_FORWARDING_DENIED /usr/share/squid/errors/zh-tw/ERR_FTP_DISABLED /usr/share/squid/errors/zh-tw/ERR_FTP_FAILURE /usr/share/squid/errors/zh-tw/ERR_FTP_FORBIDDEN /usr/share/squid/errors/zh-tw/ERR_FTP_NOT_FOUND /usr/share/squid/errors/zh-tw/ERR_FTP_PUT_CREATED /usr/share/squid/errors/zh-tw/ERR_FTP_PUT_ERROR /usr/share/squid/errors/zh-tw/ERR_FTP_PUT_MODIFIED /usr/share/squid/errors/zh-tw/ERR_FTP_UNAVAILABLE /usr/share/squid/errors/zh-tw/ERR_GATEWAY_FAILURE /usr/share/squid/errors/zh-tw/ERR_ICAP_FAILURE /usr/share/squid/errors/zh-tw/ERR_INVALID_REQ /usr/share/squid/errors/zh-tw/ERR_INVALID_RESP /usr/share/squid/errors/zh-tw/ERR_INVALID_URL /usr/share/squid/errors/zh-tw/ERR_LIFETIME_EXP /usr/share/squid/errors/zh-tw/ERR_NO_RELAY /usr/share/squid/errors/zh-tw/ERR_ONLY_IF_CACHED_MISS /usr/share/squid/errors/zh-tw/ERR_PRECONDITION_FAILED /usr/share/squid/errors/zh-tw/ERR_READ_ERROR /usr/share/squid/errors/zh-tw/ERR_READ_TIMEOUT /usr/share/squid/errors/zh-tw/ERR_SECURE_CONNECT_FAIL /usr/share/squid/errors/zh-tw/ERR_SHUTTING_DOWN /usr/share/squid/errors/zh-tw/ERR_SOCKET_FAILURE /usr/share/squid/errors/zh-tw/ERR_TOO_BIG /usr/share/squid/errors/zh-tw/ERR_UNSUP_HTTPVERSION /usr/share/squid/errors/zh-tw/ERR_UNSUP_REQ /usr/share/squid/errors/zh-tw/ERR_URN_RESOLVE /usr/share/squid/errors/zh-tw/ERR_WRITE_ERROR /usr/share/squid/errors/zh-tw/ERR_ZERO_SIZE_OBJECT /usr/share/squid/errors/zh-tw/error-details.txt /usr/share/squid/icons /usr/share/squid/icons/SN.png /usr/share/squid/icons/silk /usr/share/squid/icons/silk/application.png /usr/share/squid/icons/silk/arrow_up.png /usr/share/squid/icons/silk/bomb.png /usr/share/squid/icons/silk/box.png /usr/share/squid/icons/silk/bricks.png /usr/share/squid/icons/silk/bullet_red.png /usr/share/squid/icons/silk/cd.png /usr/share/squid/icons/silk/chart_line.png /usr/share/squid/icons/silk/compress.png /usr/share/squid/icons/silk/computer_link.png /usr/share/squid/icons/silk/css.png /usr/share/squid/icons/silk/cup.png /usr/share/squid/icons/silk/database.png /usr/share/squid/icons/silk/database_table.png /usr/share/squid/icons/silk/drive_disk.png /usr/share/squid/icons/silk/film.png /usr/share/squid/icons/silk/film_key.png /usr/share/squid/icons/silk/folder.png /usr/share/squid/icons/silk/folder_table.png /usr/share/squid/icons/silk/image.png /usr/share/squid/icons/silk/information.png /usr/share/squid/icons/silk/layers.png /usr/share/squid/icons/silk/layout.png /usr/share/squid/icons/silk/link.png /usr/share/squid/icons/silk/music.png /usr/share/squid/icons/silk/package.png /usr/share/squid/icons/silk/package_go.png /usr/share/squid/icons/silk/page_code.png /usr/share/squid/icons/silk/page_excel.png /usr/share/squid/icons/silk/page_green.png /usr/share/squid/icons/silk/page_white.png /usr/share/squid/icons/silk/page_white_acrobat.png /usr/share/squid/icons/silk/page_white_c.png /usr/share/squid/icons/silk/page_white_cplusplus.png /usr/share/squid/icons/silk/page_white_flash.png /usr/share/squid/icons/silk/page_white_magnify.png /usr/share/squid/icons/silk/page_white_picture.png /usr/share/squid/icons/silk/page_white_powerpoint.png /usr/share/squid/icons/silk/page_white_stack.png /usr/share/squid/icons/silk/page_white_text.png /usr/share/squid/icons/silk/page_white_word.png /usr/share/squid/icons/silk/page_white_zip.png /usr/share/squid/icons/silk/page_world.png /usr/share/squid/icons/silk/photo.png /usr/share/squid/icons/silk/picture.png /usr/share/squid/icons/silk/plugin.png /usr/share/squid/icons/silk/plugin_add.png /usr/share/squid/icons/silk/script.png /usr/share/squid/icons/silk/script_gear.png /usr/share/squid/icons/silk/script_palette.png /var/log/squid /var/spool/squid
Dienst/Deamon-Start einrichten
Um einen Squid, welcher als Dienst/Deamon als Hintergrundprozess läuft, auch nach einem Neustart des Servers zur Verfügung zu haben, soll der Dienst/Daemon mit dem Server mit gestartet werden, was mit nachfolgendem Befehl realisiert werden kann:
# systemctl enable squid.service ln -s '/usr/lib/systemd/system/squid.service' '/etc/systemd/system/multi-user.target.wants/squid.service'
Eine Überprüfung, ob beim Neustart des Server der squid-Dienst/Deamon wirklich mit gestartet wird, kann mit nachfolgendem Befehl erfolgen und sollte eine Anzeige, wie ebenfalls nachfolgend dargestellt ausgeben:
# systemctl list-unit-files --type=service | grep -e squid.service squid.service enabled
bzw.
# systemctl is-enabled squid.service enabled
iptables Regel
Damit der Squid als Proxy-Server auch erreichbar ist und nicht die Weitergabe der IP-Paket vom Paketfilter iptables blockiert wird, muss nachfolgende Regel zum iptables-Regelwerk hinzugefügt werden.
Um die aktuellen iptables-Regeln erweitern zu können, sollten diese erst einmal aufgelistet werden, was mit nachfolgendem Befehl durchgeführt werden kann:
# iptables -L -nv --line-numbers Chain INPUT (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 3269 2693K ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 2 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 3 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 4 1 60 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 5 16 512 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 2563 packets, 1114K bytes) num pkts bytes target prot opt in out source destination
Nachfolgender Befehl, fügt folgende iptables-Regeln dem iptables-Regelwerk nach der Position 4 hinzu, ohne das der Paketfilter angehalten werden muss:
-A INPUT -p tcp --dport 3128 -j ACCEPT
-A INPUT -p tcp --dport 3129 -j ACCEPT
und hier der Befehl:
# iptables -I INPUT 5 -p tcp --dport 3128 -j ACCEPT # iptables -I INPUT 6 -p tcp --dport 3129 -j ACCEPT
Ein erneute Abfrage des iptables-Regelwerts, sollte dann nachfolgend dargestellte Ausgabe ergeben, was mit folgendem Befehl durchgeführt werden kann:
# iptables -L -nv --line-numbers Chain INPUT (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 2 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 3 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 4 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 5 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:3128 6 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:3129 7 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 4 packets, 624 bytes) num pkts bytes target prot opt in out source destination
Die neuen Zeilen sind an Position 5 (INPUT) und an Position 6 (INPUT) zu sehen, hier nachfolgend zur Verdeutlichung noch einmal dargestellt (nur relevanter Ausschnitt):
... 5 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:3128 6 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:3129 ...
Um diese iptables-Regel dauerhaft, auch nach einem Neustart des Server, weiterhin im iptables-Regelwerk zu speichern, muss nachfolgend dargestellter Befehl abschließend noch ausgeführt werden:
# /usr/sbin/iptables-save > /etc/sysconfig/iptables
Grund-Konfiguration
Nachfolgende Konfiguration stellt eine Basiskonfiguration dar, mit verschiedenen Ausprägung in Bezug auf die Authentifizierung.
Nach der Installation des Squid Proxy-Server sind folgende Konfigurationsdateien von Bedeutung:
/etc/NetworkManager/dispatcher.d/20-squid(NetworkManager Konfiguration)/etc/logrotate.d/squid(Anweisungen zum logrotate)/etc/pam.d/squid(PAM-Legitimationsanweisungen)
/etc/squid/cachemgr.conf(Cache-Manager Konfigurationen)/etc/squid/errorpage.css(CSS-Style der Fehlerseite)/etc/squid/mime.conf(Zusätzliche MIME-Konfigurationen)/etc/squid/msntauth.conf(Beispieldatei für eine MSNT Authentifizierung)/etc/squid/squid.conf(Hauptkonfigurationsdatei)
/etc/sysconfig/squid(Starteinstellungensquid-Dienst/Daemon)
/usr/share/squid/errors(Speicherort der Fehlerseite und der Templates)
und
/etc/httpd/conf.d/squid.conf(httpd-Daemon CGI-Konfigurationen für Apache Webserver)
/etc/squid/squid.conf
Da die Konfigurationsdatei /etc/squid/squid.conf aufgrund von Kommentar- und Leerzeichen sehr schnell an Übersichtlichkeit verliert, kann mit folgendem Befehl eine Ausgabe ohne Kommentar- und Leerzeilen erzeugt werden, welche dann nach der Grundinstallation von Squid wie folgt aussehen sollte:
# egrep -v '(^#|^$)' /etc/squid/squid.conf
Die Konfigurationsdatei /etc/squid/squid.conf ohne Kommentar- und Leerzeichen:
# egrep -v '(^#|^$)' /etc/squid/squid.conf acl localnet src 10.0.0.0/8 # RFC1918 possible internal network acl localnet src 172.16.0.0/12 # RFC1918 possible internal network acl localnet src 192.168.0.0/16 # RFC1918 possible internal network acl localnet src fc00::/7 # RFC 4193 local private network range acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines acl SSL_ports port 443 acl Safe_ports port 80 # http acl Safe_ports port 21 # ftp acl Safe_ports port 443 # https acl Safe_ports port 70 # gopher acl Safe_ports port 210 # wais acl Safe_ports port 1025-65535 # unregistered ports acl Safe_ports port 280 # http-mgmt acl Safe_ports port 488 # gss-http acl Safe_ports port 591 # filemaker acl Safe_ports port 777 # multiling http acl CONNECT method CONNECT http_access deny !Safe_ports http_access deny CONNECT !SSL_ports http_access allow localhost manager http_access deny manager http_access allow localnet http_access allow localhost http_access deny all http_port 3128 coredump_dir /var/spool/squid refresh_pattern ^ftp: 1440 20% 10080 refresh_pattern ^gopher: 1440 0% 1440 refresh_pattern -i (/cgi-bin/|\?) 0 0% 0 refresh_pattern . 0 20% 4320
Authentifizierung
Squid Proxy-Server kennt verschiedene Authentifizierungsmöglichkeiten. Nachfolgend eine Liste aller Möglichkeiten:
- DB: Uses a SQL database.
- getpwam: Uses the old-fashioned Unix password file.
- LDAP: Uses the Lightweight Directory Access Protocol.
- MSNT: Uses a Windows NT authentication domain.
- MSNT-multi-domain: Allows login to one of multiple Windows NT domains.
- NCSA: Uses an NCSA-style username and password file.
- NIS (or YP): Uses the NIS database
- PAM: Uses the Unix Pluggable Authentication Modules scheme.
- POP3: Uses an email server to validate credentials. Useful for single-signon to proxy and email.
- RADIUS: Uses a RADIUS server for login validation.
- SASL: Uses SASL libraries.
- SMB: Uses a SMB server like Windows NT or Samba.
- SSPI: Windows native authenticator
Nachfolgend sollen zwei der aus der Liste der oben genannten Möglichkeiten beschrieben:
- NCSA: Uses an NCSA-style username and password file. Siehe nachfolgenden internen Link
- LDAP: Uses the Lightweight Directory Access Protocol. Siehe nachfolgenden internen Link
- LDAP: Uses the Lightweight Directory Access Protocol without anonyouse bind. Siehe nachfolgenden internen Link
NCSA-Authentifizierung
Um die NCSA-Authentifizierung (NCSA-style Username und Passwort Authentifizierung) aktivieren zu können, ist es erforderlich eine Passwort-Datei in der Benutzernamen und Passwörter hinterlegt werden, zu erstellen, was mit nachfolgendem Befehl durchgeführt werden kann:
# /usr/bin/htpasswd -c -m /etc/squid/ncsa_passwd klaus New password: Re-type new password: Adding password for user klaus
Das Programm htpasswd generiert für den angegeben Benutzer einen Eintrag in der neu zu erstellenden Passwort-Datei
/etc/squid/ncsa_passwd
mit dem Benutzernamen klaus und einem verschlüsselten Passwort.
Nachfolgende Option kommen dabei zum Einsatz:
-cdient nur zur erstmaligen Erstellung der Passwort-Datei/etc/squid/ncsa_passwd-mverwendet den Standardverschlüsselungsalgorithmus MD5.

bcryt funktioniert aktuell NICHT !!!
Um weitere Benutzer zur Passwort-Datei
/etc/squid/ncsa_passwd
hinzuzufügen, wird eine Variante des oben beschriebenen Befehls, ohne die Option -c verwendet.
# /usr/bin/htpasswd -m /etc/squid/ncsa_passwd petra New password: Re-type new password: Adding password for user petra
Die Passwort-Datei
/etc/squid/ncsa_passwd
kann mit folgendem Befehl zur Anzeige gebracht werden und sollte wie folgt aussehen:
# cat /etc/squid/ncsa_passwd klaus:$apr1$...DerRestistgeheim petra:$apr1$...DerRestistgeheim
Nachfolgende Ergänzungen sind in der Konfigurationsdatei
/etc/squid/squid.conf
notwendig, um die NCSA-Authentifizierung im Squid Proxy-Server einsetzen zu:
(Komplette Konfigurationsdatei)
# # Recommended minimum configuration: # # Tachtler - NCSA authentication - auth_param basic program /usr/lib64/squid/basic_ncsa_auth /etc/squid/ncsa_passwd auth_param basic utf8 on auth_param basic children 5 startup=1 idle=1 concurrency=0 auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein! auth_param basic credentialsttl 60 minutes auth_param basic casesensitive off # Example rule allowing access from your local networks. # Adapt to list your (internal) IP networks from where browsing # should be allowed acl localnet src 10.0.0.0/8 # RFC1918 possible internal network acl localnet src 172.16.0.0/12 # RFC1918 possible internal network acl localnet src 192.168.0.0/16 # RFC1918 possible internal network # Tachtler - disabled IPv6 - # default: acl localnet src fc00::/7 # RFC 4193 local private network range # default: acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines acl SSL_ports port 443 acl Safe_ports port 80 # http acl Safe_ports port 21 # ftp acl Safe_ports port 443 # https acl Safe_ports port 70 # gopher acl Safe_ports port 210 # wais acl Safe_ports port 1025-65535 # unregistered ports acl Safe_ports port 280 # http-mgmt acl Safe_ports port 488 # gss-http acl Safe_ports port 591 # filemaker acl Safe_ports port 777 # multiling http # Tachtler - NCSA authentication - acl ncsa_users proxy_auth REQUIRED acl CONNECT method CONNECT # # Recommended minimum Access Permission configuration: # # Deny requests to certain unsafe ports http_access deny !Safe_ports # Deny CONNECT to other than secure SSL ports http_access deny CONNECT !SSL_ports # Only allow cachemgr access from localhost http_access allow localhost manager http_access deny manager # We strongly recommend the following be uncommented to protect innocent # web applications running on the proxy server who think the only # one who can access services on "localhost" is a local user # Tachtler - enabled, deny access to localhost via squid proxy - # default: #http_access deny to_localhost http_access deny to_localhost # # INSERT YOUR OWN RULE(S) HERE TO ALLOW ACCESS FROM YOUR CLIENTS # # Example rule allowing access from your local networks. # Adapt localnet in the ACL section to list your (internal) IP networks # from where browsing should be allowed # Tachtler - NCSA authentication - # default: http_access allow localnet # default: http_access allow localhost http_access allow localnet ncsa_users http_access allow localhost ncsa_users # And finally deny all other access to this proxy http_access deny all # Squid normally listens to port 3128 http_port 3128 # Uncomment and adjust the following to add a disk cache directory. #cache_dir ufs /var/spool/squid 100 16 256 # Leave coredumps in the first cache dir coredump_dir /var/spool/squid # # Add any of your own refresh_pattern entries above these. # refresh_pattern ^ftp: 1440 20% 10080 refresh_pattern ^gopher: 1440 0% 1440 refresh_pattern -i (/cgi-bin/|\?) 0 0% 0 refresh_pattern . 0 20% 4320
Erklärungen:
Nachfolgende Optionen werden zur Initialisierung der NCSA-Authentifizierung verwendet:
# Tachtler - NCSA authentication - auth_param basic program /usr/lib64/squid/basic_ncsa_auth /etc/squid/ncsa_passwd auth_param basic utf8 on auth_param basic children 5 startup=1 idle=1 concurrency=0 auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein! auth_param basic credentialsttl 60 minutes auth_param basic casesensitive off
auth_param basic program /usr/lib64/squid/basic_ncsa_auth /etc/squid/ncsa_passwd
Aufruf des Programms /usr/lib64/squid/basic_ncsa_auth mit der Passwortdatei /etc/squid/ncsa_passwd als Parameter.
auth_param basic utf8 on
Bei der Übertragung des Benutzernamens und des Passwortes soll UTF-8 als Zeichensatz verwendet werden.
auth_param basic children 5 startup=1 idle=1 concurrency=0
Beim Start der Authentifizierungsdienste/-Deamons sollen 5 Dienste/Deamons zum Einsatz kommen, wobei 1 beim Start von Squid gestartet werden sollen, jedoch nach erfolgreicher Erstnutzung 1 Dienst/Deamon zur Verfügung stehen soll.
auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein!
Angabe der Zeichenkette, welche durch z.B. dem Browser beim Authentifizierungs-Dialog präsentiert werden soll.
auth_param basic credentialsttl 60 minutes
Zeit der Zwischenspeicherung der Authentifizierungsdaten, bevor diese erneut angefragt werden.
auth_param basic casesensitive off
Deaktivierung der Groß- und Kleinschreibung bei der Abfrage des Benutzernamens.
# Tachtler - NCSA authentication -
acl ncsa_users proxy_auth REQUIRED
acl ncsa_users proxy_auth REQUIRED
Definition einer ACL mit den Namen: ncsa_users und der Bedingung proxy_auth REQUIRED, was bedeutet, das eine Proxy-Authentifizierung beim Einsatz/Definition zwingend erforderlich ist.
# Tachtler - NCSA authentication - # default: http_access allow localnet # default: http_access allow localhost http_access allow localnet ncsa_users http_access allow localhost ncsa_users
http_access allow localnet ncsa_users
Definition einer HTTP-Zugriffsregel, welche besagt, dass bei einem Client aus dem lokalen Netz, zusätzlich die ACL ncsa_users erfüllt sein muss.
http_access allow localhost ncsa_users
Definition einer HTTP-Zugriffsregel, welche besagt, dass bei einem Client aus dem lokalen Host, zusätzlich die ACL ncsa_users erfüllt sein muss.
LDAP-Authentifizierung
Für die Authentifizierung gegen einen LDAP-Server, hier OpenLDAP sind nachfolgende Voraussetzungen erforderlich, wie diese unter nachfolgendem internen Link beschrieben sind:
Nachfolgende Ergänzungen sind in der Konfigurationsdatei
/etc/squid/squid.conf
notwendig, um die LDAP-Authentifizierung im Squid Proxy-Server einsetzen zu:
(Komplette Konfigurationsdatei)
# # Recommended minimum configuration: # # Tachtler - LDAP authentication - auth_param basic program /usr/lib64/squid/basic_ldap_auth -b "ou=People,dc=tachtler,dc=net" -f "uid=%s" -h ldap.idmz.tachtler.net auth_param basic utf8 on auth_param basic children 5 startup=1 idle=1 concurrency=0 auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein! auth_param basic credentialsttl 60 minutes auth_param basic casesensitive off # Example rule allowing access from your local networks. # Adapt to list your (internal) IP networks from where browsing # should be allowed acl localnet src 10.0.0.0/8 # RFC1918 possible internal network acl localnet src 172.16.0.0/12 # RFC1918 possible internal network acl localnet src 192.168.0.0/16 # RFC1918 possible internal network # Tachtler - disabled IPv6 - # default: acl localnet src fc00::/7 # RFC 4193 local private network range # default: acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines acl SSL_ports port 443 acl Safe_ports port 80 # http acl Safe_ports port 21 # ftp acl Safe_ports port 443 # https acl Safe_ports port 70 # gopher acl Safe_ports port 210 # wais acl Safe_ports port 1025-65535 # unregistered ports acl Safe_ports port 280 # http-mgmt acl Safe_ports port 488 # gss-http acl Safe_ports port 591 # filemaker acl Safe_ports port 777 # multiling http # Tachtler - LDAP authentication - acl ldap_auth proxy_auth REQUIRED acl CONNECT method CONNECT # # Recommended minimum Access Permission configuration: # # Deny requests to certain unsafe ports http_access deny !Safe_ports # Deny CONNECT to other than secure SSL ports http_access deny CONNECT !SSL_ports # Only allow cachemgr access from localhost http_access allow localhost manager http_access deny manager # We strongly recommend the following be uncommented to protect innocent # web applications running on the proxy server who think the only # one who can access services on "localhost" is a local user # Tachtler - enabled, deny access to localhost via squid proxy - # default: #http_access deny to_localhost http_access deny to_localhost # # INSERT YOUR OWN RULE(S) HERE TO ALLOW ACCESS FROM YOUR CLIENTS # # Example rule allowing access from your local networks. # Adapt localnet in the ACL section to list your (internal) IP networks # from where browsing should be allowed # Tachtler - LDAP authentication - # default: http_access allow localnet # default: http_access allow localhost http_access allow localnet ldap_auth http_access allow localhost ldap_auth # And finally deny all other access to this proxy http_access deny all # Squid normally listens to port 3128 http_port 3128 # Uncomment and adjust the following to add a disk cache directory. #cache_dir ufs /var/spool/squid 100 16 256 # Leave coredumps in the first cache dir coredump_dir /var/spool/squid # # Add any of your own refresh_pattern entries above these. # refresh_pattern ^ftp: 1440 20% 10080 refresh_pattern ^gopher: 1440 0% 1440 refresh_pattern -i (/cgi-bin/|\?) 0 0% 0 refresh_pattern . 0 20% 4320
Erklärungen:
Nachfolgende Optionen werden zur Initialisierung der NCSA-Authentifizierung verwendet:
# Tachtler - LDAP authentication - auth_param basic program /usr/lib64/squid/basic_ldap_auth -b "ou=People,dc=tachtler,dc=net" -f "uid=%s" -h auth_param basic utf8 on auth_param basic children 5 startup=1 idle=1 concurrency=0 auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein! auth_param basic credentialsttl 60 minutes auth_param basic casesensitive off
auth_param basic program /usr/lib64/squid/basic_ldap_auth -b "ou=People,dc=tachtler,dc=net" -f "uid=%s" -h
Aufruf des Programms /usr/lib64/squid/basic_ldap_auth mit dem Pfad im LDAP-Verzeichnisbaum zu den Benutzern und mit welcher Ausprägung der Aufruf erfolgen soll z.B. (uid=%s).
auth_param basic utf8 on
Bei der Übertragung des Benutzernamens und des Passwortes soll UTF-8 als Zeichensatz verwendet werden.
auth_param basic children 5 startup=1 idle=1 concurrency=0
Beim Start der Authentifizierungsdienste/-Deamons sollen 5 Dienste/Deamons zum Einsatz kommen, wobei 1 beim Start von Squid gestartet werden sollen, jedoch nach erfolgreicher Erstnutzung 1 Dienst/Deamon zur Verfügung stehen soll.
auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein!
Angabe der Zeichenkette, welche durch z.B. dem Browser beim Authentifizierungs-Dialog präsentiert werden soll.
auth_param basic credentialsttl 60 minutes
Zeit der Zwischenspeicherung der Authentifizierungsdaten, bevor diese erneut angefragt werden.
auth_param basic casesensitive off
Deaktivierung der Groß- und Kleinschreibung bei der Abfrage des Benutzernamens.
# Tachtler - LDAP authentication -
acl ldap_auth proxy_auth REQUIRED
acl ldap_auth proxy_auth REQUIRED
Definition einer ACL mit den Namen: ldap_auth und der Bedingung proxy_auth REQUIRED, was bedeutet, das eine Proxy-Authentifizierung beim Einsatz/Definition zwingend erforderlich ist.
# Tachtler - LDAP authentication - # default: http_access allow localnet # default: http_access allow localhost http_access allow localnet ldap_auth http_access allow localhost ldap_auth
http_access allow localnet ldap_auth
Definition einer HTTP-Zugriffsregel, welche besagt, dass bei einem Client aus dem lokalen Netz, zusätzlich die ACL ldap_auth erfüllt sein muss.
http_access allow localhost ncsa_users
Definition einer HTTP-Zugriffsregel, welche besagt, dass bei einem Client aus dem lokalen Host, zusätzlich die ACL ldap_auth erfüllt sein muss.
LDAP-Authentifizierung ohne "anonymous bind"
Für die Authentifizierung gegen einen LDAP-Server, hier OpenLDAP sind nachfolgende Voraussetzungen erforderlich, wie diese unter nachfolgendem internen Link beschrieben sind:
Um die LDAP-Authentifizierung ohne „anonymous bind“ (LDAP: Authentifizierung gegen das Lightweight Directory Access Protocol.) aktivieren zu können, ist es erforderlich eine Passwort-Datei in der das Passwort für den „Ersatzbenutzer“ hinterlegt werden kann, zu erstellen.
Damit das Passwort für den „Ersatzbenutzer“ nicht in der Konfigurationsdatei des Squid Proxy-Servers erscheint, kann mit nachfolgendem Befehl eine Passwort-Datei erstellt werden:
# touch /etc/squid/ldap_passwd
Mit folgendem Befehlen sind die Dateirechte auf lesend und schreibend durch den Benutzer root und lesend durch den Benutzer squid und sonst keine Rechte für alle anderen Benutzer zu setzen:
# chown root.squid /etc/squid/ldap_passwd
# chmod 640 /etc/squid/ldap_passwd
Ein Beispiel für den Inhalt der Datei /etc/squid/ldap_passwd kann wie folgt aussehen:
geheim

geheim und kann ohne weitere Angaben so in die Datei /etc/squid/ldap_passwd geschrieben werden.
Nachfolgende Ergänzungen sind in der Konfigurationsdatei
/etc/squid/squid.conf
notwendig, um die LDAP-Authentifizierung im Squid Proxy-Server einsetzen zu:
(Komplette Konfigurationsdatei)
# # Recommended minimum configuration: # # Tachtler - LDAP authentication - auth_param basic program /usr/lib64/squid/basic_ldap_auth -b "ou=People,dc=tachtler,dc=net" -f "uid=%s" -h ldap.idmz.tachtler.net -D "cn=Ersatzbenutzer,dc=tachtler,dc=net" - W /etc/squid/ldap_passwd auth_param basic utf8 on auth_param basic children 5 startup=1 idle=1 concurrency=0 auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein! auth_param basic credentialsttl 60 minutes auth_param basic casesensitive off # Example rule allowing access from your local networks. # Adapt to list your (internal) IP networks from where browsing # should be allowed acl localnet src 10.0.0.0/8 # RFC1918 possible internal network acl localnet src 172.16.0.0/12 # RFC1918 possible internal network acl localnet src 192.168.0.0/16 # RFC1918 possible internal network # Tachtler - disabled IPv6 - # default: acl localnet src fc00::/7 # RFC 4193 local private network range # default: acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines acl SSL_ports port 443 acl Safe_ports port 80 # http acl Safe_ports port 21 # ftp acl Safe_ports port 443 # https acl Safe_ports port 70 # gopher acl Safe_ports port 210 # wais acl Safe_ports port 1025-65535 # unregistered ports acl Safe_ports port 280 # http-mgmt acl Safe_ports port 488 # gss-http acl Safe_ports port 591 # filemaker acl Safe_ports port 777 # multiling http # Tachtler - LDAP authentication - acl ldap_auth proxy_auth REQUIRED acl CONNECT method CONNECT # # Recommended minimum Access Permission configuration: # # Deny requests to certain unsafe ports http_access deny !Safe_ports # Deny CONNECT to other than secure SSL ports http_access deny CONNECT !SSL_ports # Only allow cachemgr access from localhost http_access allow localhost manager http_access deny manager # We strongly recommend the following be uncommented to protect innocent # web applications running on the proxy server who think the only # one who can access services on "localhost" is a local user # Tachtler - enabled, deny access to localhost via squid proxy - # default: #http_access deny to_localhost http_access deny to_localhost # # INSERT YOUR OWN RULE(S) HERE TO ALLOW ACCESS FROM YOUR CLIENTS # # Example rule allowing access from your local networks. # Adapt localnet in the ACL section to list your (internal) IP networks # from where browsing should be allowed # Tachtler - LDAP authentication - # default: http_access allow localnet # default: http_access allow localhost http_access allow localnet ldap_auth http_access allow localhost ldap_auth # And finally deny all other access to this proxy http_access deny all # Squid normally listens to port 3128 http_port 3128 # Uncomment and adjust the following to add a disk cache directory. #cache_dir ufs /var/spool/squid 100 16 256 # Leave coredumps in the first cache dir coredump_dir /var/spool/squid # # Add any of your own refresh_pattern entries above these. # refresh_pattern ^ftp: 1440 20% 10080 refresh_pattern ^gopher: 1440 0% 1440 refresh_pattern -i (/cgi-bin/|\?) 0 0% 0 refresh_pattern . 0 20% 4320
Erklärungen:
Nachfolgende Optionen werden zur Initialisierung der NCSA-Authentifizierung verwendet:
# Tachtler - LDAP authentication - auth_param basic program /usr/lib64/squid/basic_ldap_auth -b "ou=People,dc=tachtler,dc=net" -f "uid=%s" -h ldap.idmz.tachtler.net -D "cn=Ersatzbenutzer,dc=tachtler,dc=net" - W /etc/squid/ldap_passwd auth_param basic utf8 on auth_param basic children 5 startup=1 idle=1 concurrency=0 auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein! auth_param basic credentialsttl 60 minutes auth_param basic casesensitive off
auth_param basic program /usr/lib64/squid/basic_ldap_auth -b "ou=People,dc=tachtler,dc=net" -f "uid=%s" -h ldap.idmz.tachtler.net -D "cn=Ersatzbenutzer,dc=tachtler,dc=net" - W /etc/squid/ldap_passwd
Aufruf des Programms /usr/lib64/squid/basic_ldap_auth mit dem Pfad im LDAP-Verzeichnisbaum zu den Benutzern und mit welcher Ausprägung der Aufruf erfolgen soll z.B. (uid=%s) und der Angabe des „„Ersatzbenutzers“ für den nicht „anonymouse bind“ und die Angabe einer Passwort-Datei indem das Passwort für den „Ersatzbenutzer“ hinterlegt ist.
auth_param basic utf8 on
Bei der Übertragung des Benutzernamens und des Passwortes soll UTF-8 als Zeichensatz verwendet werden.
auth_param basic children 5 startup=1 idle=1 concurrency=0
Beim Start der Authentifizierungsdienste/-Deamons sollen 5 Dienste/Deamons zum Einsatz kommen, wobei 1 beim Start von Squid gestartet werden sollen, jedoch nach erfolgreicher Erstnutzung 1 Dienst/Deamon zur Verfügung stehen soll.
auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein!
Angabe der Zeichenkette, welche durch z.B. dem Browser beim Authentifizierungs-Dialog präsentiert werden soll.
auth_param basic credentialsttl 60 minutes
Zeit der Zwischenspeicherung der Authentifizierungsdaten, bevor diese erneut angefragt werden.
auth_param basic casesensitive off
Deaktivierung der Groß- und Kleinschreibung bei der Abfrage des Benutzernamens.
# Tachtler - LDAP authentication -
acl ldap_auth proxy_auth REQUIRED
acl ldap_auth proxy_auth REQUIRED
Definition einer ACL mit den Namen: ldap_auth und der Bedingung proxy_auth REQUIRED, was bedeutet, das eine Proxy-Authentifizierung beim Einsatz/Definition zwingend erforderlich ist.
# Tachtler - LDAP authentication - # default: http_access allow localnet # default: http_access allow localhost http_access allow localnet ldap_auth http_access allow localhost ldap_auth
http_access allow localnet ldap_auth
Definition einer HTTP-Zugriffsregel, welche besagt, dass bei einem Client aus dem lokalen Netz, zusätzlich die ACL ldap_auth erfüllt sein muss.
http_access allow localhost ncsa_users
Definition einer HTTP-Zugriffsregel, welche besagt, dass bei einem Client aus dem lokalen Host, zusätzlich die ACL ldap_auth erfüllt sein muss.
Überprüfung der Konfiguration
Mit nachfolgenden Befehlen kann überprüft werden, ob die Konfiguration des Squid Proxy-Servers syntaktisch korrekt ist.
Nachfolgender Befehl liest die Konfiguration des Squid Proxy-Server ein und gibt diese auf dem Bildschirm aus und zeigt mögliche Fehler, jeweils unter der fehlerhaften Konfigurationszeile an:
# squid -k parse 2015/02/12 14:55:29| Startup: Initializing Authentication Schemes ... 2015/02/12 14:55:29| Startup: Initialized Authentication Scheme 'basic' 2015/02/12 14:55:29| Startup: Initialized Authentication Scheme 'digest' 2015/02/12 14:55:29| Startup: Initialized Authentication Scheme 'negotiate' 2015/02/12 14:55:29| Startup: Initialized Authentication Scheme 'ntlm' 2015/02/12 14:55:29| Startup: Initialized Authentication. 2015/02/12 14:55:29| Processing Configuration File: /etc/squid/squid.conf (depth 0) 2015/02/12 14:55:29| Processing: auth_param basic program /usr/lib64/squid/basic_ncsa_auth /etc/squid/ncsa_passwd 2015/02/12 14:55:29| Processing: auth_param basic utf8 on 2015/02/12 14:55:29| Processing: auth_param basic children 5 startup=0 idle=1 concurrency=0 2015/02/12 14:55:29| Processing: auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein! 2015/02/12 14:55:29| Processing: auth_param basic credentialsttl 60 minutes 2015/02/12 14:55:29| Processing: auth_param basic casesensitive off 2015/02/12 14:55:29| Processing: acl localnet src 10.0.0.0/8 # RFC1918 possible internal network 2015/02/12 14:55:29| Processing: acl localnet src 172.16.0.0/12 # RFC1918 possible internal network 2015/02/12 14:55:29| Processing: acl localnet src 192.168.0.0/16 # RFC1918 possible internal network 2015/02/12 14:55:29| Processing: acl SSL_ports port 443 2015/02/12 14:55:29| Processing: acl Safe_ports port 80 # http 2015/02/12 14:55:29| Processing: acl Safe_ports port 21 # ftp 2015/02/12 14:55:29| Processing: acl Safe_ports port 443 # https 2015/02/12 14:55:29| Processing: acl Safe_ports port 70 # gopher 2015/02/12 14:55:29| Processing: acl Safe_ports port 210 # wais 2015/02/12 14:55:29| Processing: acl Safe_ports port 1025-65535 # unregistered ports 2015/02/12 14:55:29| Processing: acl Safe_ports port 280 # http-mgmt 2015/02/12 14:55:29| Processing: acl Safe_ports port 488 # gss-http 2015/02/12 14:55:29| Processing: acl Safe_ports port 591 # filemaker 2015/02/12 14:55:29| Processing: acl Safe_ports port 777 # multiling http 2015/02/12 14:55:29| Processing: acl ncsa_users proxy_auth REQUIRED 2015/02/12 14:55:29| Processing: acl CONNECT method CONNECT 2015/02/12 14:55:29| Processing: http_access deny !Safe_ports 2015/02/12 14:55:29| Processing: http_access deny CONNECT !SSL_ports 2015/02/12 14:55:29| Processing: http_access allow localhost manager 2015/02/12 14:55:29| Processing: http_access deny manager 2015/02/12 14:55:29| Processing: http_access deny to_localhost 2015/02/12 14:55:29| Processing: http_access allow localnet ncsa_users 2015/02/12 14:55:29| Processing: http_access allow localhost ncsa_users 2015/02/12 14:55:29| Processing: http_access deny all 2015/02/12 14:55:29| Processing: http_port 3128 2015/02/12 14:55:29| Processing: coredump_dir /var/spool/squid 2015/02/12 14:55:29| Processing: refresh_pattern ^ftp: 1440 20% 10080 2015/02/12 14:55:29| Processing: refresh_pattern ^gopher: 1440 0% 1440 2015/02/12 14:55:29| Processing: refresh_pattern -i (/cgi-bin/|\?) 0 0% 0 2015/02/12 14:55:29| Processing: refresh_pattern . 0 20% 4320 2015/02/12 14:55:29| Initializing https proxy context
Nachfolgender Befehl liest ebenfalls die Konfiguration des Squid Proxy-Server ein, gibt aber nur gefundene Fehler aus. Bei einer Überprüfung bei derSquid Proxy-Server noch nicht gestartet ist, wird dies ebenfalls mit einer Fehlerausgabe angezeigt, welche jedoch in diesem Fall ignoriert werden kann.
# squid -k check squid: ERROR: No running copy
Erster Start/Neustart squid
Mit nachfolgendem Befehl kann ein erster Start des Squid Proxy-Servers durchgeführt werden.
# systemctl start squid.service
Mit nachfolgendem Befehl kann ein Neustart des Squid Proxy-Servers durchgeführt werden.
# systemctl restart squid.service
Mit nachfolgendem Befehl kann überprüft werden, ob der Squid Proxy-Server erfolgreich gestartet werden konnte:
# systemctl status squid.service
squid.service - Squid caching proxy
Loaded: loaded (/usr/lib/systemd/system/squid.service; enabled)
Active: active (running) since Thu 2015-02-12 14:59:13 CET; 15s ago
Process: 12609 ExecStart=/usr/sbin/squid $SQUID_OPTS -f $SQUID_CONF (code=exited, status=0/SUCCESS)
Process: 12603 ExecStartPre=/usr/libexec/squid/cache_swap.sh (code=exited, status=0/SUCCESS)
Main PID: 12613 (squid)
CGroup: /system.slice/squid.service
├─12613 /usr/sbin/squid -f /etc/squid/squid.conf
├─12615 (squid-1) -f /etc/squid/squid.conf
└─12618 (logfile-daemon) /var/log/squid/access.log
Feb 12 14:59:13 server50.idmz.tachtler.net systemd[1]: Starting Squid caching proxy...
Feb 12 14:59:13 server50.idmz.tachtler.net squid[12613]: Squid Parent: will start 1 kids
Feb 12 14:59:13 server50.idmz.tachtler.net systemd[1]: Started Squid caching proxy.
Feb 12 14:59:13 server50.idmz.tachtler.net squid[12613]: Squid Parent: (squid-1) process 12615 started
Nachfolgend kann in der LOG-Datei
/var/log/squid/cache.log
überprüft werden, ob evtl. Fehler, Warnungen oder Probleme beim Startvorgang aufgetreten sind, was mit nachfolgenden Befehl durchgeführt werden kann:
# cat /var/log/squid/cache.log 2015/02/12 14:59:13 kid1| Starting Squid Cache version 3.3.8 for x86_64-redhat-linux-gnu... 2015/02/12 14:59:13 kid1| Process ID 12615 2015/02/12 14:59:13 kid1| Process Roles: worker 2015/02/12 14:59:13 kid1| With 16384 file descriptors available 2015/02/12 14:59:13 kid1| Initializing IP Cache... 2015/02/12 14:59:13 kid1| DNS Socket created at 0.0.0.0, FD 7 2015/02/12 14:59:13 kid1| Adding domain idmz.tachtler.net from /etc/resolv.conf 2015/02/12 14:59:13 kid1| Adding domain idmz.tachtler.net from /etc/resolv.conf 2015/02/12 14:59:13 kid1| Adding domain tachtler.net. from /etc/resolv.conf 2015/02/12 14:59:13 kid1| Adding domain idmz.tachtler.net. from /etc/resolv.conf 2015/02/12 14:59:13 kid1| Adding domain edmz.tachtler.net. from /etc/resolv.conf 2015/02/12 14:59:13 kid1| Adding domain intra.tachtler.net. from /etc/resolv.conf 2015/02/12 14:59:13 kid1| Adding domain dmz.tachtler.net from /etc/resolv.conf 2015/02/12 14:59:13 kid1| Adding nameserver 192.168.0.20 from /etc/resolv.conf 2015/02/12 14:59:13 kid1| Adding nameserver 192.168.1.20 from /etc/resolv.conf 2015/02/12 14:59:13 kid1| helperOpenServers: Starting 0/5 'basic_ncsa_auth' processes 2015/02/12 14:59:13 kid1| helperOpenServers: No 'basic_ncsa_auth' processes needed. 2015/02/12 14:59:13 kid1| Logfile: opening log daemon:/var/log/squid/access.log 2015/02/12 14:59:13 kid1| Logfile Daemon: opening log /var/log/squid/access.log 2015/02/12 14:59:13 kid1| Local cache digest enabled; rebuild/rewrite every 3600/3600 sec 2015/02/12 14:59:13 kid1| Store logging disabled 2015/02/12 14:59:13 kid1| Swap maxSize 0 + 262144 KB, estimated 20164 objects 2015/02/12 14:59:13 kid1| Target number of buckets: 1008 2015/02/12 14:59:13 kid1| Using 8192 Store buckets 2015/02/12 14:59:13 kid1| Max Mem size: 262144 KB 2015/02/12 14:59:13 kid1| Max Swap size: 0 KB 2015/02/12 14:59:13 kid1| Using Least Load store dir selection 2015/02/12 14:59:13 kid1| Set Current Directory to /var/spool/squid 2015/02/12 14:59:13 kid1| Loaded Icons. 2015/02/12 14:59:13 kid1| HTCP Disabled. 2015/02/12 14:59:13 kid1| Squid plugin modules loaded: 0 2015/02/12 14:59:13 kid1| Adaptation support is off. 2015/02/12 14:59:13 kid1| Accepting HTTP Socket connections at local=0.0.0.0:3128 remote=[::] FD 10 flags=9 2015/02/12 14:59:14 kid1| storeLateRelease: released 0 objects
Mit nachfolgendem Befehl kann abschließend überprüft werden, auf welchen Ports der Squid Proxy-Server lauscht:
# netstat -tulpen | grep squid tcp 0 0 0.0.0.0:3128 0.0.0.0:* LISTEN 0 159108 12615/(squid-1) udp 0 0 0.0.0.0:39954 0.0.0.0:* 23 159105 12615/(squid-1)
Erster Browser Aufruf
Nachdem nachfolgende Konfiguration im Browser, hier am Beispiel eines Mozilla Firefox-Browsers, wie in nachfolgender Bildschirmkopie dargestellt, durchgeführt wurde, sollte mit dem Surfen über den Squid Proxy-Server nichts mehr im Wege stehen:
Nachfolgende Einstellungen sind im Mozilla Firefox-Browsers unter
- Open Menu (Menü) | Preferences (Einstellungen) | Advanced (Erweitert) | Network (Netzwerk) | Settings… (Einstellungen…) | Manual proxy configuration (Manuelle Proxy-Konfiguration)
durchzuführen:
| Einstellungen | Standardwert | Wert |
|---|---|---|
| HTTP-Proxy | [leer] | 192.168.0.50 (IP des Squid Proxy-Servers) |
| Port | [leer] | 3128 |
Anschließend sollte nun beim Aufruf einer Website wie z.B. https://www.google.de nachfolgendes Browser-Dialog-Fenster erscheinen und zur Eingabe eines Benutzernamens eines Passwortes auffordern, wie auf nachfolgender Bildschirm dargestellt:
Nach korrekter Eingabe des Benutzernamens und Passwortes, kann in nachfolgender LOG-Datei
/var/log/squid/access.log
des Squid Proxy-Servers nachvollzogen werden, wie und ob die Authentifizierung erfolgreich war, was mit nachfolgendem Befehl realisiert werden kann:
# cat /var/log/squid/access.log 1423750404.846 3 192.168.0.10 TCP_DENIED/407 4014 GET http://google.de/ - HIER_NONE/- text/html 1423750410.146 293 192.168.0.10 TCP_MISS/301 755 GET http://google.de/ klaus HIER_DIRECT/216.58.211.3 text/html 1423750410.301 153 192.168.0.10 TCP_MISS/302 1233 GET http://www.google.de/ klaus HIER_DIRECT/74.125.136.94 text/html 1423750410.663 184 192.168.0.10 TCP_MISS/200 963 POST http://clients1.google.com/ocsp klaus HIER_DIRECT/216.58.211.14 application/ocsp-response 1423750411.407 151 192.168.0.10 TCP_MISS/200 963 POST http://clients1.google.com/ocsp klaus HIER_DIRECT/216.58.211.14 application/ocsp-response 1423750411.799 86 192.168.0.10 TCP_MISS/200 963 POST http://clients1.google.com/ocsp klaus HIER_DIRECT/216.58.211.14 application/ocsp-response
Cache-Konfiguration
Der Squid Proxy-Server bietet die Möglichkeit, einmal geladene Inhalte, sich in eine Speicher zu merken, bis diese Ihre Gültigkeit verlieren. Diesen Speicher nennt Cache.
Cache aktivieren
Um den Cache-Speicher zu aktivieren ist folgender Eintrag in der Konfigurationsdatei /etc/squid/squid.conf zu aktivieren, wie nachfolgend beschrieben:
# Uncomment and adjust the following to add a disk cache directory. # Tachtler - enable cache space on disk - cache_dir ufs /var/spool/squid 100 16 256
Erklärungen:
Nachfolgende soll die Aktivierung des Cache beschrieben werden:
cache_dir ufs /var/spool/squid 100 16 256
Der Parameter ufs bezeichnet die Art und Weise wie die Daten auf der Festplatte gespeichert werden. ufs ist das bewährte Speicherformat und standardmäßig im Squid Proxy-Server immer verfügbar. Nachfolgend eine Übersicht der verfügbaren Speicherformate im Squid Proxy Server in der Version 3.3.8 unter CentOS in der Version 7:
ufs- Standardaufs- Wieufs, verwendet jedoch POSIX-Threads um zu verhindern, dass Squid durch Festplattenzugriffe blockiert wird.diskd- Wieufs, verwendet jedoch einen separaten Prozess beim Schreiben des Cache, um zu verhindern, dass Squid durch Festplattenzugriffe blockiert wird.
Der Parameter 100 gibt an, wie viel Megabyte auf der Festplatte für den Cache zur Speicherung zur Verfügung stehen soll.
Der Parameter 16 gibt an, wie viele Verzeichnisse im Verzeichnis /var/spool/squid erstellt werden, um die Cache Daten zu Speichern.
Der Parameter 256 gibt an, wie viele Verzeichnisse unterhalb der obersten Verzeichnisebenen (16, Wert vom zweiten Parameter) im Verzeichnis /var/spool/squid/XX erstellt werden, um die Cache Daten zu Speichern.
* (XX steht für eines der obersten 16 Verzeichnisse)
Mit nachfolgendem Befehl kann vor einem Neustart die Verzeichnisstruktur zur Aufnahme der Cache Daten erzeugt werden:
# squid -z
Cache deaktivieren
Um den Cache-Speicher zu deaktivieren ist folgender Eintrag in der Konfigurationsdatei /etc/squid/squid.conf auskommentiert zu lassen, wie nachfolgend beschrieben:
# Uncomment and adjust the following to add a disk cache directory. #cache_dir ufs /var/spool/squid 100 16 256

Localnet-Konfiguration
Standardmäßig kennt der Squid Proxy Server alle möglichen lokalen Netzwerkadressbereiche.
Möglicherweise ist aber eine Anpassung oder Unterscheidung der lokalen Netzwerke erforderlich um erweitere Konfigurationen und Authentifizierungsmöglichkeiten zu realisieren.
Nachfolgend soll dargestellt werden, wie z.B. gewisse lokale Netze von der Authentifizierung ausgenommen werden können und andere weiterhin der Authentifizieren unterliegen.
Dabei sollen, wie in nachfolgender Tabelle dargestellt, die entsprechenden Regeln zur Anwendung kommen:
| Zone | Domain | IP-Adressbereich | Regel |
|---|---|---|---|
| localhost | localhost | 127.0.0.0/8 | KEINE Authentifizierung |
| IDMZ | idmz.tachtler.net | 192.168.0.0/24 | KEINE Authentifizierung |
| EDMZ | edmz.tachtler.net | 192.168.1.0/24 | KEINE Authentifizierung |
| Intranet | intra.tachtler.net | 192.168.2.0/24 | LDAP Authentifizierung |
Nachfolgende Ergänzungen sind in der Konfigurationsdatei
/etc/squid/squid.conf
notwendig, um eine genauere Localnet-Konfiguration im Squid Proxy-Server einsetzen zu können:
(Komplette Konfigurationsdatei)
# # Recommended minimum configuration: # # Tachtler - LDAP authentication - auth_param basic program /usr/lib64/squid/basic_ldap_auth -b "ou=People,dc=tachtler,dc=net" -f "uid=%s" -h ldap.idmz.tachtler.net -D "cn=Ersatzbenutzer,dc=tachtler,dc=net" -W /etc/squid/ldap_passwd auth_param basic utf8 on auth_param basic children 5 startup=1 idle=1 concurrency=0 auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein! auth_param basic credentialsttl 60 minutes auth_param basic casesensitive off # Example rule allowing access from your local networks. # Adapt to list your (internal) IP networks from where browsing # should be allowed # Tachtler - disabled default localnet configuration - # default: acl localnet src 10.0.0.0/8 # RFC1918 possible internal network # default: acl localnet src 172.16.0.0/12 # RFC1918 possible internal network # default: acl localnet src 192.168.0.0/16 # RFC1918 possible internal network acl idmz_net src 192.168.0.0/24 # idmz.tachtler.net acl edmz_net src 192.168.1.0/24 # edmz.tachtler.net acl intra_net src 192.168.2.0/24 # intra.tachtler.net # Tachtler - disabled IPv6 - # default: acl localnet src fc00::/7 # RFC 4193 local private network range # default: acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines acl SSL_ports port 443 acl Safe_ports port 80 # http acl Safe_ports port 21 # ftp acl Safe_ports port 443 # https acl Safe_ports port 70 # gopher acl Safe_ports port 210 # wais acl Safe_ports port 1025-65535 # unregistered ports acl Safe_ports port 280 # http-mgmt acl Safe_ports port 488 # gss-http acl Safe_ports port 591 # filemaker acl Safe_ports port 777 # multiling http # Tachtler - LDAP authentication - acl ldap_auth proxy_auth REQUIRED acl CONNECT method CONNECT # # Recommended minimum Access Permission configuration: # # Deny requests to certain unsafe ports http_access deny !Safe_ports # Deny CONNECT to other than secure SSL ports http_access deny CONNECT !SSL_ports # Only allow cachemgr access from localhost http_access allow localhost manager http_access deny manager # We strongly recommend the following be uncommented to protect innocent # web applications running on the proxy server who think the only # one who can access services on "localhost" is a local user # Tachtler - enabled, deny access to localhost via squid proxy - # default: #http_access deny to_localhost http_access deny to_localhost # # INSERT YOUR OWN RULE(S) HERE TO ALLOW ACCESS FROM YOUR CLIENTS # # Example rule allowing access from your local networks. # Adapt localnet in the ACL section to list your (internal) IP networks # from where browsing should be allowed # Tachtler - LDAP authentication - # default: http_access allow localnet # default: http_access allow localhost http_access allow localhost http_access allow idmz_net http_access allow edmz_net http_access allow intra_net ldap_auth # And finally deny all other access to this proxy http_access deny all # Squid normally listens to port 3128 http_port 3128 # Uncomment and adjust the following to add a disk cache directory. #cache_dir ufs /var/spool/squid 100 16 256 # Leave coredumps in the first cache dir coredump_dir /var/spool/squid # # Add any of your own refresh_pattern entries above these. # refresh_pattern ^ftp: 1440 20% 10080 refresh_pattern ^gopher: 1440 0% 1440 refresh_pattern -i (/cgi-bin/|\?) 0 0% 0 refresh_pattern . 0 20% 4320
Erklärungen:
# Example rule allowing access from your local networks. # Adapt to list your (internal) IP networks from where browsing # should be allowed # Tachtler - disabled default localnet configuration - # default: acl localnet src 10.0.0.0/8 # RFC1918 possible internal network # default: acl localnet src 172.16.0.0/12 # RFC1918 possible internal network # default: acl localnet src 192.168.0.0/16 # RFC1918 possible internal network acl idmz_net src 192.168.0.0/24 # idmz.tachtler.net acl edmz_net src 192.168.1.0/24 # edmz.tachtler.net acl intra_net src 192.168.2.0/24 # intra.tachtler.net # Tachtler - disabled IPv6 - # default: acl localnet src fc00::/7 # RFC 4193 local private network range # default: acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines
acl idmz_net src 192.168.0.0/24 # idmz.tachtler.net
Definition einer ACL mit dem Namen: idmz_net und hier, des Quell-IP-Adressbereichs 192.168.0.0/24.
acl edmz_net src 192.168.1.0/24 # edmz.tachtler.net
Definition einer ACL mit dem Namen: edmz_net und hier, des Quell-IP-Adressbereichs 192.168.1.0/24.
acl intra_net src 192.168.2.0/24 # intra.tachtler.net
Definition einer ACL mit dem Namen: intra_net und hier, des Quell-IP-Adressbereichs 192.168.2.0/24.

# Tachtler - LDAP authentication -
acl ldap_auth proxy_auth REQUIRED
acl ldap_auth proxy_auth REQUIRED
Definition einer ACL mit den Namen: ldap_auth und der Bedingung proxy_auth REQUIRED, was bedeutet, das eine Proxy-Authentifizierung beim Einsatz/Definition zwingend erforderlich ist.
# Tachtler - LDAP authentication - # default: http_access allow localnet # default: http_access allow localhost http_access allow localhost http_access allow idmz_net http_access allow edmz_net http_access allow intra_net ldap_auth
http_access allow localhost
Definition einer HTTP-Zugriffsregel, welche besagt, dass bei einem Client welcher in die ACL: localhost fällt, keine weiteren Beschränkungen für den Zugriff auf das Internet bestehen.
http_access allow idmz_net
Definition einer HTTP-Zugriffsregel, welche besagt, dass bei einem Client welcher in die ACL: idmz_net fällt, keine weiteren Beschränkungen für den Zugriff auf das Internet bestehen.
http_access allow edmz_net
Definition einer HTTP-Zugriffsregel, welche besagt, dass bei einem Client welcher in die ACL: edmz_net fällt, keine weiteren Beschränkungen für den Zugriff auf das Internet bestehen.
http_access allow intra_net ldap_auth
Definition einer HTTP-Zugriffsregel, welche besagt, dass bei einem Client welcher in die ACL: intra_net fällt, zusätzlich die ACL ldap_auth erfüllt sein muss.
Safe_ports-Konfiguration
Standardmäßig sind im Squid Proxy-Server gewisse Ports als sogenannte Safe_ports definiert, was bedeutet, das über diese Ports eine Verbindung hergestellt werden kann. Ports die hier nicht definiert sind, können nicht über den Squid Proxy-Server erreicht werden.
Die hier definierten Ports können je nach den persönlichen Bedürfnissen vermindert oder erweitert werden, was in nachfolgendem Beispiel auch durchgeführt werden soll.
Dazu sollen gewisse Port-Definitionen auskommentiert werden und zusätzliche Ports hinzugefügt werden. Ein Auflistung der zu Konfigurierenden Safe_ports soll in nachfolgende Tabelle aufgelistet werden.

| ACL Safe_port Definition | Beschreibung | Nutzung [ja/nein/neu] |
|---|---|---|
| acl Safe_ports port 80 | # http | ja |
| acl Safe_ports port 21 | # ftp | ja |
| acl Safe_ports port 443 | # https | ja |
| acl Safe_ports port 70 | # gopher | nein |
| acl Safe_ports port 210 | # wais | nein |
| acl Safe_ports port 1025-65535 | # unregistered ports | ja |
| acl Safe_ports port 280 | # http-mgmt | nein |
| acl Safe_ports port 488 | # gss-http | nein |
| acl Safe_ports port 591 | # filemaker | nein |
| acl Safe_ports port 777 | # multiling http | nein |
Nachfolgende Ergänzungen sind in der Konfigurationsdatei
/etc/squid/squid.conf
notwendig, um die Safe_ports Definitionen im Squid Proxy-Server einsetzen zu können:
(Komplette Konfigurationsdatei)
# # Recommended minimum configuration: # # Tachtler - LDAP authentication - auth_param basic program /usr/lib64/squid/basic_ldap_auth -b "ou=People,dc=tachtler,dc=net" -f "uid=%s" -h ldap.idmz.tachtler.net -D "cn=Ersatzbenutzer,dc=tachtler,dc=net" -W /etc/squid/ldap_passwd auth_param basic utf8 on auth_param basic children 5 startup=1 idle=1 concurrency=0 auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein! auth_param basic credentialsttl 60 minutes auth_param basic casesensitive off # Example rule allowing access from your local networks. # Adapt to list your (internal) IP networks from where browsing # should be allowed # Tachtler - disabled default localnet configuration - # default: acl localnet src 10.0.0.0/8 # RFC1918 possible internal network # default: acl localnet src 172.16.0.0/12 # RFC1918 possible internal network # default: acl localnet src 192.168.0.0/16 # RFC1918 possible internal network acl idmz_net src 192.168.0.0/24 # idmz.tachtler.net acl edmz_net src 192.168.1.0/24 # edmz.tachtler.net acl intra_net src 192.168.2.0/24 # intra.tachtler.net # Tachtler - disabled IPv6 - # default: acl localnet src fc00::/7 # RFC 4193 local private network range # default: acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines acl SSL_ports port 443 # Tachtler - Safe_ports configuration - acl Safe_ports port 80 # http acl Safe_ports port 21 # ftp acl Safe_ports port 443 # https # default: acl Safe_ports port 70 # gopher # default: acl Safe_ports port 210 # wais acl Safe_ports port 1025-65535 # unregistered ports # default: acl Safe_ports port 280 # http-mgmt # default: acl Safe_ports port 488 # gss-http # default: acl Safe_ports port 591 # filemaker # default: acl Safe_ports port 777 # multiling http # Tachtler - LDAP authentication - acl ldap_auth proxy_auth REQUIRED acl CONNECT method CONNECT # # Recommended minimum Access Permission configuration: # # Deny requests to certain unsafe ports http_access deny !Safe_ports # Deny CONNECT to other than secure SSL ports http_access deny CONNECT !SSL_ports # Only allow cachemgr access from localhost http_access allow localhost manager http_access deny manager # We strongly recommend the following be uncommented to protect innocent # web applications running on the proxy server who think the only # one who can access services on "localhost" is a local user # Tachtler - enabled, deny access to localhost via squid proxy - # default: #http_access deny to_localhost http_access deny to_localhost # # INSERT YOUR OWN RULE(S) HERE TO ALLOW ACCESS FROM YOUR CLIENTS # # Example rule allowing access from your local networks. # Adapt localnet in the ACL section to list your (internal) IP networks # from where browsing should be allowed # Tachtler - LDAP authentication - # default: http_access allow localnet # default: http_access allow localhost http_access allow localhost http_access allow idmz_net http_access allow edmz_net http_access allow intra_net ldap_auth # And finally deny all other access to this proxy http_access deny all # Squid normally listens to port 3128 http_port 3128 # Uncomment and adjust the following to add a disk cache directory. #cache_dir ufs /var/spool/squid 100 16 256 # Leave coredumps in the first cache dir coredump_dir /var/spool/squid # # Add any of your own refresh_pattern entries above these. # refresh_pattern ^ftp: 1440 20% 10080 refresh_pattern ^gopher: 1440 0% 1440 refresh_pattern -i (/cgi-bin/|\?) 0 0% 0 refresh_pattern . 0 20% 4320
Erklärungen:
Nachfolgend die explizite Konfiguration für die Safe_ports:
# Tachtler - Safe_ports configuration - acl Safe_ports port 80 # http acl Safe_ports port 21 # ftp acl Safe_ports port 443 # https # default: acl Safe_ports port 70 # gopher # default: acl Safe_ports port 210 # wais acl Safe_ports port 1025-65535 # unregistered ports # default: acl Safe_ports port 280 # http-mgmt # default: acl Safe_ports port 488 # gss-http # default: acl Safe_ports port 591 # filemaker # default: acl Safe_ports port 777 # multiling http
CONNECT-Konfiguration
Im Squid Proxy-Server können sogenannte CONNECT-Verbindungen definiert werden, was bedeutet, das über diese Ziel-Domain-Adressen und Ports eine Verbindung hergestellt werden kann, wobei es sich um einen erweiterten Verbindungsaufbau und nicht um einen klassischen „Request“ nur über einen Port handelt. Ziel-Domain-Adressen und Ports die hier nicht definiert sind, können nicht über den Squid Proxy-Server erreicht werden.
Nachfolgend sollen gewisse Ziel-Domain-Adressen und Port-Definitionen hinzugefügt werden. Ein Auflistung der zu konfigurierenden CONNECT-Verbindungen sollen in nachfolgende Tabelle aufgelistet werden.
| ACL CONNECT-Verbindung Definition | Verbindungs-Typ |
|---|---|
| Microsoft Windows Update | |
| acl windowsupdate_CONNECT_dstdoamin dstdomain www.update.microsoft.com | Ziel-Domain-Adresse |
| acl windowsupdate_CONNECT_dstdoamin dstdomain sls.micrsoft.com | Ziel-Domain-Adresse |
| Pidgin | |
| acl pidgin_CONNECT_dstdoamin dstdomain proxy.eu.jabber.org | Ziel-Domain-Adresse |
| acl pidgin_CONNECT_dstdomain dstdomain slogin.icq.com | Ziel-Domain-Adresse |
| acl pidgin_CONNECT_ports port 5190 # Pidgin (proxy) | Port |
| acl pidgin_CONNECT_ports port 5222-5223 # Pidgin | Port |
| AirDroid | |
| acl airdroid_CONNECT_ports port 8888-8890 # AirDroid | Port |
Nachfolgende Ergänzungen sind in der Konfigurationsdatei
/etc/squid/squid.conf
notwendig, um die CONNECT-Verbindungs Definitionen im Squid Proxy-Server einsetzen zu können:
(Komplette Konfigurationsdatei)
# # Recommended minimum configuration: # # Tachtler - LDAP authentication - auth_param basic program /usr/lib64/squid/basic_ldap_auth -b "ou=People,dc=tachtler,dc=net" -f "uid=%s" -h ldap.idmz.tachtler.net -D "cn=Ersatzbenutzer,dc=tachtler,dc=net" -W /etc/squid/ldap_passwd auth_param basic utf8 on auth_param basic children 5 startup=1 idle=1 concurrency=0 auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein! auth_param basic credentialsttl 60 minutes auth_param basic casesensitive off # Example rule allowing access from your local networks. # Adapt to list your (internal) IP networks from where browsing # should be allowed # Tachtler - disabled default localnet configuration - # default: acl localnet src 10.0.0.0/8 # RFC1918 possible internal network # default: acl localnet src 172.16.0.0/12 # RFC1918 possible internal network # default: acl localnet src 192.168.0.0/16 # RFC1918 possible internal network acl idmz_net src 192.168.0.0/24 # idmz.tachtler.net acl edmz_net src 192.168.1.0/24 # edmz.tachtler.net acl intra_net src 192.168.2.0/24 # intra.tachtler.net # Tachtler - disabled IPv6 - # default: acl localnet src fc00::/7 # RFC 4193 local private network range # default: acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines acl SSL_ports port 443 # Tachtler - Safe_ports configuration - acl Safe_ports port 80 # http acl Safe_ports port 21 # ftp acl Safe_ports port 443 # https # default: acl Safe_ports port 70 # gopher # default: acl Safe_ports port 210 # wais acl Safe_ports port 1025-65535 # unregistered ports # default: acl Safe_ports port 280 # http-mgmt # default: acl Safe_ports port 488 # gss-http # default: acl Safe_ports port 591 # filemaker # default: acl Safe_ports port 777 # multiling http # Tachtler - CONNECT configuration - # Tachtler - Pidgin acl pidgin_CONNECT_ports port 5190 # Pidgin (proxy) acl pidgin_CONNECT_ports port 5222-5223 # Pidgin # Tachtler - AirDroid acl airdroid_CONNECT_ports port 8888-8890 # AirDroid # Tachtler - LDAP authentication - acl ldap_auth proxy_auth REQUIRED acl CONNECT method CONNECT # Tachtler - ACL dstdomain (Destination Domain) configuration - # Tachtler - Microsoft Windows-Update acl windowsupdate_CONNECT_dstdomain dstdomain www.update.microsoft.com acl windowsupdate_CONNECT_dstdomain dstdomain sls.micrsoft.com acl windowsupdate dstdomain .windowsupdate.microsoft.com acl windowsupdate dstdomain download.microsoft.com acl windowsupdate dstdomain .update.microsoft.com acl windowsupdate dstdomain .download.windowsupdate.com acl windowsupdate dstdomain dmd.metaservices.microsoft.com acl windowsupdate dstdomain redir.metaservices.microsoft.com acl windowsupdate dstdomain images.metaservices.microsoft.com acl windowsupdate dstdomain c.microsoft.com acl windowsupdate dstdomain wustat.windows.com acl windowsupdate dstdomain crl.microsoft.com acl windowsupdate dstdomain ctldl.windowsupdate.com acl windowsupdate dstdomain sls.microsoft.com acl windowsupdate dstdomain productactivation.one.microsoft.com acl windowsupdate dstdomain ntservicepack.microsoft.com acl windowsupdate dstdomain watson.microsoft.com acl windowsupdate dstdomain www.microsoft.com acl windowsupdate dstdomain www.msftncsi.com acl windowsupdate dstdomain spynet2.microsoft.com acl windowsupdate dstdomain sqm.telemetry.microsoft.com acl windowsupdate dstdomain iecvlist.microsoft.com acl windowsupdate dstdomain sqm.microsoft.com # Tachtler - Pidgin acl pidgin_CONNECT_dstdomain dstdomain proxy.eu.jabber.org acl pidgin_CONNECT_dstdomain dstdomain slogin.icq.com # # Recommended minimum Access Permission configuration: # # Deny requests to certain unsafe ports http_access deny !Safe_ports # Deny CONNECT to other than secure SSL ports # Tachtler # default: http_access deny CONNECT !SSL_ports http_access deny CONNECT !SSL_ports !pidgin_CONNECT_ports !airdroid_CONNECT_ports # Only allow cachemgr access from localhost http_access allow localhost manager http_access deny manager # We strongly recommend the following be uncommented to protect innocent # web applications running on the proxy server who think the only # one who can access services on "localhost" is a local user # Tachtler - enabled, deny access to localhost via squid proxy - # default: #http_access deny to_localhost http_access deny to_localhost # # INSERT YOUR OWN RULE(S) HERE TO ALLOW ACCESS FROM YOUR CLIENTS # # Example rule allowing access from your local networks. # Adapt localnet in the ACL section to list your (internal) IP networks # from where browsing should be allowed # Tachtler - access rules - # default: http_access allow localnet # default: http_access allow localhost # Tachtler - Microsoft Windows-Update http_access allow CONNECT windowsupdate_CONNECT_dstdomain intra_net http_access allow windowsupdate intra_net # Tachtler - Pidgin http_access allow CONNECT pidgin_CONNECT_dstdomain intra_net http_access allow pidgin_CONNECT_ports intra_net # Tachtler - AirDroid http_access allow airdroid_CONNECT_ports intra_net # Tachtler - LDAP authentication - http_access allow localhost http_access allow idmz_net http_access allow edmz_net http_access allow intra_net ldap_auth # And finally deny all other access to this proxy http_access deny all # Squid normally listens to port 3128 http_port 3128 # Uncomment and adjust the following to add a disk cache directory. #cache_dir ufs /var/spool/squid 100 16 256 # Leave coredumps in the first cache dir coredump_dir /var/spool/squid # # Add any of your own refresh_pattern entries above these. # refresh_pattern ^ftp: 1440 20% 10080 refresh_pattern ^gopher: 1440 0% 1440 refresh_pattern -i (/cgi-bin/|\?) 0 0% 0 refresh_pattern . 0 20% 4320 # Tachtler - Microsoft Windows-Update # Tachtler - CAUTION - violates HTTP, but necessary! refresh_pattern -i microsoft.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windowsupdate.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windows.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims
Erklärungen:
Nachfolgende Erklärungen beschreiben die Verwendung von CONNECT-Verbindungen anhand der einzelnen Bereiche der Squid Proxy-Server Konfiguration.
CONNECT-Port
Nachfolgende Definition von zusätzlichen Ports, welche sich nicht in Safe_ports befinden, ermöglicht den Zugriff auf die entsprechenden Ports durch den Squid Proxy-Server. Dies kann aufgrund dieser Konfiguration später auch nur in Verbindung mit einer Ziel-Domain-Adresse erfolgen (z.B. Pidgin), oder eben auch ohne eine Ziel-Domain-Adresse (z.B. AirDroid):
# Tachtler - CONNECT configuration - # Tachtler - Pidgin acl pidgin_CONNECT_ports port 5190 # Pidgin (proxy) acl pidgin_CONNECT_ports port 5222-5223 # Pidgin # Tachtler - AirDroid acl airdroid_CONNECT_ports port 8888-8890 # AirDroid
CONNECT-Ziel-Domain-Adressen
Nachfolgende Definition von Ziel-Domain-Adressen ermöglicht es später für diese Adressen einen Zugriff zu ermöglichen, OHNE eine Authentifizierung durchführen zu müssen, was natütrlich nur bei Netzen zum tragen kommt, bei denen eine Authentifizierung zwingend definiert ist.
# Tachtler - ACL dstdomain (Destination Domain) configuration - # Tachtler - Microsoft Windows-Update acl windowsupdate_CONNECT_dstdomain dstdomain www.update.microsoft.com acl windowsupdate_CONNECT_dstdomain dstdomain sls.micrsoft.com acl windowsupdate dstdomain .windowsupdate.microsoft.com acl windowsupdate dstdomain download.microsoft.com acl windowsupdate dstdomain .update.microsoft.com acl windowsupdate dstdomain .download.windowsupdate.com acl windowsupdate dstdomain dmd.metaservices.microsoft.com acl windowsupdate dstdomain redir.metaservices.microsoft.com acl windowsupdate dstdomain images.metaservices.microsoft.com acl windowsupdate dstdomain c.microsoft.com acl windowsupdate dstdomain wustat.windows.com acl windowsupdate dstdomain crl.microsoft.com acl windowsupdate dstdomain ctldl.windowsupdate.com acl windowsupdate dstdomain sls.microsoft.com acl windowsupdate dstdomain productactivation.one.microsoft.com acl windowsupdate dstdomain ntservicepack.microsoft.com acl windowsupdate dstdomain watson.microsoft.com acl windowsupdate dstdomain www.microsoft.com acl windowsupdate dstdomain www.msftncsi.com acl windowsupdate dstdomain spynet2.microsoft.com acl windowsupdate dstdomain sqm.telemetry.microsoft.com acl windowsupdate dstdomain iecvlist.microsoft.com acl windowsupdate dstdomain sqm.microsoft.com # Tachtler - Pidgin acl pidgin_CONNECT_dstdomain dstdomain proxy.eu.jabber.org acl pidgin_CONNECT_dstdomain dstdomain slogin.icq.com
CONNECT-HTTP-Zugriff
Nachfolgende Definition des HTTP-Zugriffs auf bestimmte Ports, ermöglicht es nur auf die definierten Ports zuzugreifen. Dazu müssen die neuen Ports vom Verbot - deny ausgenommen werden. Das bedeutet in der nachfolgenden Konfiguration, das alle Ports außer die ausgenommenen Ports unzugänglich sind.
# Deny CONNECT to other than secure SSL ports # Tachtler # default: http_access deny CONNECT !SSL_ports http_access deny CONNECT !SSL_ports !pidgin_CONNECT_ports !airdroid_CONNECT_ports
Nachfolgende HTTP-Zugriffs-Regeln definieren nun den Ablauf der Erlaubnis, auf das Internet zugreifen zu dürfen, je nach Zugehörigkeit des Clients, zu einem bestimmten Netz.

# Tachtler - access rules - # default: http_access allow localnet # default: http_access allow localhost # Tachtler - Microsoft Windows-Update http_access allow CONNECT windowsupdate_CONNECT_dstdomain intra_net http_access allow windowsupdate intra_net # Tachtler - Pidgin http_access allow CONNECT pidgin_CONNECT_dstdomain pidgin_CONNECT_ports intra_net # Tachtler - AirDroid http_access allow airdroid_CONNECT_ports intra_net # Tachtler - LDAP authentication - http_access allow localhost http_access allow idmz_net http_access allow edmz_net http_access allow intra_net ldap_auth
# Tachtler - Microsoft Windows-Update http_access allow CONNECT windowsupdate_CONNECT_dstdomain intra_net http_access allow windowsupdate intra_net
Wenn ein Client aus der ACL in dem das Netz
intra_net
definiert ist stammt, und auf die in der ACL mit den Ziel-Domain-Adressen
windowsupdate_CONNECT_dstdomain
über die nachfolgend definierten weiteren Ziel-Domain-Adressen
windowsupdate
zugreifen möchte, kann dies OHNE LDAP-Authentifizierung erfolgen.
# Tachtler - Pidgin http_access allow CONNECT pidgin_CONNECT_dstdomain pidgin_CONNECT_ports intra_net
Wenn ein Client aus der ACL in dem das Netz
intra_net
definiert ist stammt, und auf die in der ACL mit den Ziel-Domain-Adressen
pidgin_CONNECT_dstdomain
über die nachfolgend definierten Ports, welche in der ACL
pidgin_CONNECT_ports
zugreifen möchte, kann dies OHNE LDAP-Authentifizierung erfolgen.
# Tachtler - AirDroid http_access allow airdroid_CONNECT_ports intra_net
Wenn ein Client aus der ACL in dem das Netz
intra_net
definiert ist stammt, und auf die nachfolgend definierten Ports, welche in der ACL
airdroid_CONNECT_ports
zugreifen möchte, kann dies OHNE LDAP-Authentifizierung erfolgen.
http_access allow localhost
Über localhost kann grundsätzlich - OHNE LDAP-Authentifizierung auf das Internet zugegriffen werden.
http_access allow idmz_net http_access allow edmz_net
Die Clients aus der ACL in dem die Netze:
idmz_netedmz_net
definiert sind, können grundsätzlich - OHNE LDAP-Authentifizierung auf das Internet zugreifen.
http_access allow intra_net ldap_auth
Die Clients aus der ACL in dem das Netz:
intra_net
definiert sind, können grundsätzlich - NUR MIT LDAP-Authentifizierung auf das Internet zugreifen.
refresh_pattern-Konfiguration
Wie bereits unter der Konfigurationsdatei im Abschnitt unter nachfolgendem internen Link
beschriebenen refresh_pattern Konfiguration
# Tachtler - Microsoft Windows-Update # Tachtler - CAUTION - violates HTTP, but necessary! refresh_pattern -i microsoft.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windowsupdate.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windows.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-imsreload-into-ims
dient diese Konfiguration dazu, für den Zugriff auf die Ziel-Domain-Adressen
microsoft.comwindowsupdate.comwindows.com
und die von diesen Ziel-Domain-Adressen heruntergeladenen Datei-Typen, welche in den entsprechenden Regex-Anweisungen:
microsoft.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip)windowsupdate.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip)windows.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip)
definiert sind, zwischen
4320Minuten (3 Tage)43200Minuten (30 Tage)
ohne weitere Einzelzugriffs Überprüfungen herunter ladbar zu machen.

reload-into-ims stellt eine Verletzung des HTTP-Standards dar !!!

ACL-Konfiguration IP-Adressen Verfolgung
Um ermitteln zu können, welcher Client tatsächlich eine Anfrage an den Squid Proxy-Server gestellt hat, kann in den sogenannten Header-Informationen die tatsächliche IP-Adresse des ursprünglich anfragenden Clients bei jeder Anfrage mit übergeben werden.
Nachfolgende Ergänzungen sind in der Konfigurationsdatei
/etc/squid/squid.conf
notwendig, um die Client IP-Adressen Ermittlung Definitionen im Squid Proxy-Server einsetzen zu können:
(Komplette Konfigurationsdatei)
# # Recommended minimum configuration: # # Tachtler - LDAP authentication - auth_param basic program /usr/lib64/squid/basic_ldap_auth -b "ou=People,dc=tachtler,dc=net" -f "uid=%s" -h ldap.idmz.tachtler.net -D "cn=Ersatzbenutzer,dc=tachtler,dc=net" -W /etc/squid/ldap_passwd auth_param basic utf8 on auth_param basic children 5 startup=1 idle=1 concurrency=0 auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein! auth_param basic credentialsttl 60 minutes auth_param basic casesensitive off # Example rule allowing access from your local networks. # Adapt to list your (internal) IP networks from where browsing # should be allowed # Tachtler - disabled default localnet configuration - # default: acl localnet src 10.0.0.0/8 # RFC1918 possible internal network # default: acl localnet src 172.16.0.0/12 # RFC1918 possible internal network # default: acl localnet src 192.168.0.0/16 # RFC1918 possible internal network acl idmz_net src 192.168.0.0/24 # idmz.tachtler.net acl edmz_net src 192.168.1.0/24 # edmz.tachtler.net acl intra_net src 192.168.2.0/24 # intra.tachtler.net # Tachtler - disabled IPv6 - # default: acl localnet src fc00::/7 # RFC 4193 local private network range # default: acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines acl SSL_ports port 443 # Tachtler - Safe_ports configuration - acl Safe_ports port 80 # http acl Safe_ports port 21 # ftp acl Safe_ports port 443 # https # default: acl Safe_ports port 70 # gopher # default: acl Safe_ports port 210 # wais acl Safe_ports port 1025-65535 # unregistered ports # default: acl Safe_ports port 280 # http-mgmt # default: acl Safe_ports port 488 # gss-http # default: acl Safe_ports port 591 # filemaker # default: acl Safe_ports port 777 # multiling http # Tachtler - CONNECT configuration - # Tachtler - Pidgin acl pidgin_CONNECT_ports port 5190 # Pidgin (proxy) acl pidgin_CONNECT_ports port 5222-5223 # Pidgin # Tachtler - AirDroid acl airdroid_CONNECT_ports port 8888-8890 # AirDroid # Tachtler - LDAP authentication - acl ldap_auth proxy_auth REQUIRED acl CONNECT method CONNECT # Tachtler - ACL follow_x_forwarded_for configuration - follow_x_forwarded_for allow localhost follow_x_forwarded_for allow idmz_net follow_x_forwarded_for allow intra_net # Tachtler - ACL dstdomain (Destination Domain) configuration - # Tachtler - Microsoft Windows-Update acl windowsupdate_CONNECT_dstdomain dstdomain www.update.microsoft.com acl windowsupdate_CONNECT_dstdomain dstdomain sls.micrsoft.com acl windowsupdate dstdomain .windowsupdate.microsoft.com acl windowsupdate dstdomain download.microsoft.com acl windowsupdate dstdomain .update.microsoft.com acl windowsupdate dstdomain .download.windowsupdate.com acl windowsupdate dstdomain dmd.metaservices.microsoft.com acl windowsupdate dstdomain redir.metaservices.microsoft.com acl windowsupdate dstdomain images.metaservices.microsoft.com acl windowsupdate dstdomain c.microsoft.com acl windowsupdate dstdomain wustat.windows.com acl windowsupdate dstdomain crl.microsoft.com acl windowsupdate dstdomain ctldl.windowsupdate.com acl windowsupdate dstdomain sls.microsoft.com acl windowsupdate dstdomain productactivation.one.microsoft.com acl windowsupdate dstdomain ntservicepack.microsoft.com acl windowsupdate dstdomain watson.microsoft.com acl windowsupdate dstdomain www.microsoft.com acl windowsupdate dstdomain www.msftncsi.com acl windowsupdate dstdomain spynet2.microsoft.com acl windowsupdate dstdomain sqm.telemetry.microsoft.com acl windowsupdate dstdomain iecvlist.microsoft.com acl windowsupdate dstdomain sqm.microsoft.com # Tachtler - Pidgin acl pidgin_CONNECT_dstdomain dstdomain proxy.eu.jabber.org acl pidgin_CONNECT_dstdomain dstdomain slogin.icq.com # # Recommended minimum Access Permission configuration: # # Deny requests to certain unsafe ports http_access deny !Safe_ports # Deny CONNECT to other than secure SSL ports # Tachtler # default: http_access deny CONNECT !SSL_ports http_access deny CONNECT !SSL_ports !pidgin_CONNECT_ports !airdroid_CONNECT_ports # Only allow cachemgr access from localhost http_access allow localhost manager http_access deny manager # We strongly recommend the following be uncommented to protect innocent # web applications running on the proxy server who think the only # one who can access services on "localhost" is a local user # Tachtler - enabled, deny access to localhost via squid proxy - # default: #http_access deny to_localhost http_access deny to_localhost # # INSERT YOUR OWN RULE(S) HERE TO ALLOW ACCESS FROM YOUR CLIENTS # # Example rule allowing access from your local networks. # Adapt localnet in the ACL section to list your (internal) IP networks # from where browsing should be allowed # Tachtler - access rules - # default: http_access allow localnet # default: http_access allow localhost # Tachtler - Microsoft Windows-Update http_access allow CONNECT windowsupdate_CONNECT_dstdomain intra_net http_access allow windowsupdate intra_net # Tachtler - Pidgin http_access allow CONNECT pidgin_CONNECT_dstdomain intra_net http_access allow pidgin_CONNECT_ports intra_net # Tachtler - AirDroid http_access allow airdroid_CONNECT_ports intra_net # Tachtler - LDAP authentication - http_access allow localhost http_access allow idmz_net http_access allow edmz_net http_access allow intra_net ldap_auth # And finally deny all other access to this proxy http_access deny all # Squid normally listens to port 3128 http_port 3128 # Uncomment and adjust the following to add a disk cache directory. #cache_dir ufs /var/spool/squid 100 16 256 # Leave coredumps in the first cache dir coredump_dir /var/spool/squid # # Add any of your own refresh_pattern entries above these. # refresh_pattern ^ftp: 1440 20% 10080 refresh_pattern ^gopher: 1440 0% 1440 refresh_pattern -i (/cgi-bin/|\?) 0 0% 0 refresh_pattern . 0 20% 4320 # Tachtler - Microsoft Windows-Update # Tachtler - CAUTION - violates HTTP, but necessary! refresh_pattern -i microsoft.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windowsupdate.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windows.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims
Erklärungen:
Nachfolgende Einstellungen dienen der Ermittlung der tatsächlichen IP-Adresse eines anfragenden Clients.
# Tachtler - ACL follow_x_forwarded_for configuration - follow_x_forwarded_for allow localhost follow_x_forwarded_for allow idmz_net follow_x_forwarded_for allow intra_net
Definition für die Erlaubnis (allow) zur Ermittlung der tatsächlichen Client IP-Adresse für
localhost
und Clients aus dem, via ACL definierten Netzen
idmz_netintra_net
ACL-Konfiguration für Seiten ohne Authentifizierung
Falls ein Zugriff auf bestimmte Seiten im Internet aus einem Netz, welches grundsätzlich eine Authentifizierung erfordern würde, ohne das eine Authentifizierung durchgeführt werden soll, kann dies wie nachfolgend dargestellt, konfiguriert werden.
Nachfolgende Tabelle liefert eine Übersicht mit den entsprechenden Regeln, für welchen Client aus welchem Netz eine Authentifizierung grundsätzlich erforderlich ist.
| Zone | Domain | IP-Adressbereich | Regel |
|---|---|---|---|
| localhost | localhost | 127.0.0.0/8 | KEINE Authentifizierung |
| IDMZ | idmz.tachtler.net | 192.168.0.0/24 | KEINE Authentifizierung |
| EDMZ | edmz.tachtler.net | 192.168.1.0/24 | KEINE Authentifizierung |
| Intranet | intra.tachtler.net | 192.168.2.0/24 | LDAP Authentifizierung |
Alle Clients aus dem Netz: 192.168.2.0/24 würden grundsätzlich eine Authentifizierung benötigen.
Damit gewisse Seiten, welche von Clients aus dem Netz: 192.168.2.0/24 aufgerufen werden, auch OHNE Authentifizierung verfügbar sind, müssen diese Seiten in mindestens einer ACL definiert werden und im Squid Proxy-Server entsprechend konfiguriert werden.
Ein Auflistung der zu konfigurierenden Seiten ohne Authentifizierung (noauthsites)- sollen in nachfolgende Tabelle aufgelistet werden.
ACL noauthsites Definition | Verbindungs-Typ |
|---|---|
| Microsoft Windows Productactivation | |
| acl noauthsites url_regex productactivation\.one\.microsoft\.com:443 | URL Regular Expression |
| acl noauthsites url_regex activation\.sls\.microsoft\.com:443 | URL Regular Expression |
| Microsoft Windows Online-Help | |
| acl noauthsites url_regex windowshelp\.microsoft\.com/* | URL Regular Expression |
| Microsoft Internet Explorer Search-Engine-Updates | |
| acl noauthsites url_regex www\.iegallery\.com/de/* | URL Regular Expression |
Nachfolgende Ergänzungen sind in der Konfigurationsdatei
/etc/squid/squid.conf
notwendig, um die CONNECT-Verbindungs Definitionen im Squid Proxy-Server einsetzen zu können:
(Komplette Konfigurationsdatei)
# # Recommended minimum configuration: # # Tachtler - LDAP authentication - auth_param basic program /usr/lib64/squid/basic_ldap_auth -b "ou=People,dc=tachtler,dc=net" -f "uid=%s" -h ldap.idmz.tachtler.net -D "cn=Ersatzbenutzer,dc=tachtler,dc=net" -W /etc/squid/ldap_passwd auth_param basic utf8 on auth_param basic children 5 startup=1 idle=1 concurrency=0 auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein! auth_param basic credentialsttl 60 minutes auth_param basic casesensitive off # Example rule allowing access from your local networks. # Adapt to list your (internal) IP networks from where browsing # should be allowed # Tachtler - disabled default localnet configuration - # default: acl localnet src 10.0.0.0/8 # RFC1918 possible internal network # default: acl localnet src 172.16.0.0/12 # RFC1918 possible internal network # default: acl localnet src 192.168.0.0/16 # RFC1918 possible internal network acl idmz_net src 192.168.0.0/24 # idmz.tachtler.net acl edmz_net src 192.168.1.0/24 # edmz.tachtler.net acl intra_net src 192.168.2.0/24 # intra.tachtler.net # Tachtler - disabled IPv6 - # default: acl localnet src fc00::/7 # RFC 4193 local private network range # default: acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines acl SSL_ports port 443 # Tachtler - Safe_ports configuration - acl Safe_ports port 80 # http acl Safe_ports port 21 # ftp acl Safe_ports port 443 # https # default: acl Safe_ports port 70 # gopher # default: acl Safe_ports port 210 # wais acl Safe_ports port 1025-65535 # unregistered ports # default: acl Safe_ports port 280 # http-mgmt # default: acl Safe_ports port 488 # gss-http # default: acl Safe_ports port 591 # filemaker # default: acl Safe_ports port 777 # multiling http # Tachtler - CONNECT configuration - # Tachtler - Pidgin acl pidgin_CONNECT_ports port 5190 # Pidgin (proxy) acl pidgin_CONNECT_ports port 5222-5223 # Pidgin # Tachtler - AirDroid acl airdroid_CONNECT_ports port 8888-8890 # AirDroid # Tachtler - LDAP authentication - acl ldap_auth proxy_auth REQUIRED acl CONNECT method CONNECT # Tachtler - ACL follow_x_forwarded_for configuration - follow_x_forwarded_for allow localhost follow_x_forwarded_for allow idmz_net follow_x_forwarded_for allow intra_net # Tachtler - ACL dstdomain (Destination Domain) configuration - # Tachtler - Microsoft Windows-Update acl windowsupdate_CONNECT_dstdomain dstdomain www.update.microsoft.com acl windowsupdate_CONNECT_dstdomain dstdomain sls.micrsoft.com acl windowsupdate dstdomain .windowsupdate.microsoft.com acl windowsupdate dstdomain download.microsoft.com acl windowsupdate dstdomain .update.microsoft.com acl windowsupdate dstdomain .download.windowsupdate.com acl windowsupdate dstdomain dmd.metaservices.microsoft.com acl windowsupdate dstdomain redir.metaservices.microsoft.com acl windowsupdate dstdomain images.metaservices.microsoft.com acl windowsupdate dstdomain c.microsoft.com acl windowsupdate dstdomain wustat.windows.com acl windowsupdate dstdomain crl.microsoft.com acl windowsupdate dstdomain ctldl.windowsupdate.com acl windowsupdate dstdomain sls.microsoft.com acl windowsupdate dstdomain productactivation.one.microsoft.com acl windowsupdate dstdomain ntservicepack.microsoft.com acl windowsupdate dstdomain watson.microsoft.com acl windowsupdate dstdomain www.microsoft.com acl windowsupdate dstdomain www.msftncsi.com acl windowsupdate dstdomain spynet2.microsoft.com acl windowsupdate dstdomain sqm.telemetry.microsoft.com acl windowsupdate dstdomain iecvlist.microsoft.com acl windowsupdate dstdomain sqm.microsoft.com # Tachtler - Pidgin acl pidgin_CONNECT_dstdomain dstdomain proxy.eu.jabber.org acl pidgin_CONNECT_dstdomain dstdomain slogin.icq.com # Tachtler - ACL url-regex (URL regular expression) configuration - # Tachtler - Microsoft Windows Productactivation acl noauthsites url_regex productactivation\.one\.microsoft\.com:443 acl noauthsites url_regex activation\.sls\.microsoft\.com:443 # Tachtler - Microsoft Windows Online-Help acl noauthsites url_regex windowshelp\.microsoft\.com/* # Tachtler - Microsoft Internet Explorer Search-Engine-Updates acl noauthsites url_regex www\.iegallery\.com/de/* # # Recommended minimum Access Permission configuration: # # Deny requests to certain unsafe ports http_access deny !Safe_ports # Deny CONNECT to other than secure SSL ports # Tachtler # default: http_access deny CONNECT !SSL_ports http_access deny CONNECT !SSL_ports !pidgin_CONNECT_ports !airdroid_CONNECT_ports # Only allow cachemgr access from localhost http_access allow localhost manager http_access deny manager # We strongly recommend the following be uncommented to protect innocent # web applications running on the proxy server who think the only # one who can access services on "localhost" is a local user # Tachtler - enabled, deny access to localhost via squid proxy - # default: #http_access deny to_localhost http_access deny to_localhost # # INSERT YOUR OWN RULE(S) HERE TO ALLOW ACCESS FROM YOUR CLIENTS # # Example rule allowing access from your local networks. # Adapt localnet in the ACL section to list your (internal) IP networks # from where browsing should be allowed # Tachtler - access rules - # default: http_access allow localnet # default: http_access allow localhost # Tachtler - Microsoft Windows-Update http_access allow CONNECT windowsupdate_CONNECT_dstdomain intra_net http_access allow windowsupdate intra_net # Tachtler - Pidgin http_access allow CONNECT pidgin_CONNECT_dstdomain intra_net http_access allow pidgin_CONNECT_ports intra_net # Tachtler - AirDroid http_access allow airdroid_CONNECT_ports intra_net # Tachtler - LDAP authentication - http_access allow localhost http_access allow idmz_net http_access allow edmz_net http_access allow intra_net noauthsites http_access allow intra_net ldap_auth # And finally deny all other access to this proxy http_access deny all # Squid normally listens to port 3128 http_port 3128 # Uncomment and adjust the following to add a disk cache directory. #cache_dir ufs /var/spool/squid 100 16 256 # Leave coredumps in the first cache dir coredump_dir /var/spool/squid # # Add any of your own refresh_pattern entries above these. # refresh_pattern ^ftp: 1440 20% 10080 refresh_pattern ^gopher: 1440 0% 1440 refresh_pattern -i (/cgi-bin/|\?) 0 0% 0 refresh_pattern . 0 20% 4320 # Tachtler - Microsoft Windows-Update # Tachtler - CAUTION - violates HTTP, but necessary! refresh_pattern -i microsoft.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windowsupdate.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windows.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims
Erklärungen:
Nachfolgende Definitionen beschreiben, wie gewisse Seiten im Internet von der Authetifizierung ausgenomme werden können, in dem Netz, in dem grundsätzlich eine Authentifizierung der Clients erforderlich ist:
noauthsites - url_regex
# Tachtler - ACL url-regex (URL regular expression) configuration - # Tachtler - Microsoft Windows Productactivation acl noauthsites url_regex productactivation\.one\.microsoft\.com:443 acl noauthsites url_regex activation\.sls\.microsoft\.com:443 # Tachtler - Microsoft Windows Online-Help acl noauthsites url_regex windowshelp\.microsoft\.com/* # Tachtler - Microsoft Internet Explorer Search-Engine-Updates acl noauthsites url_regex www\.iegallery\.com/de/*
noauthsites - HTTP-Zugriff

# Tachtler - access rules - # default: http_access allow localnet # default: http_access allow localhost # Tachtler - Microsoft Windows-Update http_access allow CONNECT windowsupdate_CONNECT_dstdomain intra_net http_access allow windowsupdate intra_net # Tachtler - Pidgin http_access allow CONNECT pidgin_CONNECT_dstdomain intra_net http_access allow pidgin_CONNECT_ports intra_net # Tachtler - AirDroid http_access allow airdroid_CONNECT_ports intra_net # Tachtler - LDAP authentication - http_access allow localhost http_access allow idmz_net http_access allow edmz_net http_access allow intra_net noauthsites http_access allow intra_net ldap_auth
http_access allow intra_net noauthsites
Wenn ein Client aus der ACL in dem das Netz
intra_net
definiert ist stammt, und auf die in der ACL mit den URL Regular Expression
noauthsites
zugreifen möchte, kann dies OHNE LDAP-Authentifizierung erfolgen.
ACL-Konfiguration für interne Netze ohne Authentifizierung
Falls ein Zugriff auf Seiten aus internen Netzen, welches auch grundsätzlich eine Authentifizierung erfordern würde, ohne eine Authentifizierung erreichbar sein sollen, kann dies wie nachfolgend dargestellt, konfiguriert werden.
Nachfolgende Tabelle liefert eine Übersicht mit den entsprechenden Regeln, für welchen Client aus welchem Netz eine Authentifizierung grundsätzlich erforderlich ist.
| Zone | Domain | IP-Adressbereich | Regel |
|---|---|---|---|
| localhost | localhost | 127.0.0.0/8 | KEINE Authentifizierung |
| IDMZ | idmz.tachtler.net | 192.168.0.0/24 | KEINE Authentifizierung |
| EDMZ | edmz.tachtler.net | 192.168.1.0/24 | KEINE Authentifizierung |
| Intranet | intra.tachtler.net | 192.168.2.0/24 | LDAP Authentifizierung |
Alle Clients aus dem Netz: 192.168.2.0/24 würden grundsätzlich auch für Seiten aus internen Netzen eine Authentifizierung benötigen.
Nachfolgende Ergänzungen sind in der Konfigurationsdatei
/etc/squid/squid.conf
notwendig, um die CONNECT-Verbindungs Definitionen im Squid Proxy-Server einsetzen zu können:
(Komplette Konfigurationsdatei)
# # Recommended minimum configuration: # # Tachtler - LDAP authentication - auth_param basic program /usr/lib64/squid/basic_ldap_auth -b "ou=People,dc=tachtler,dc=net" -f "uid=%s" -h ldap.idmz.tachtler.net -D "cn=Ersatzbenutzer,dc=tachtler,dc=net" -W /etc/squid/ldap_passwd auth_param basic utf8 on auth_param basic children 5 startup=1 idle=1 concurrency=0 auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein! auth_param basic credentialsttl 60 minutes auth_param basic casesensitive off # Example rule allowing access from your local networks. # Adapt to list your (internal) IP networks from where browsing # should be allowed # Tachtler - disabled default localnet configuration - # default: acl localnet src 10.0.0.0/8 # RFC1918 possible internal network # default: acl localnet src 172.16.0.0/12 # RFC1918 possible internal network # default: acl localnet src 192.168.0.0/16 # RFC1918 possible internal network acl idmz_net src 192.168.0.0/24 # idmz.tachtler.net acl edmz_net src 192.168.1.0/24 # edmz.tachtler.net acl intra_net src 192.168.2.0/24 # intra.tachtler.net acl edmz_dst dst 192.168.0.0/24 # edmz.tachtler.net destination acl idmz_dst dst 192.168.1.0/24 # idmz.tachtler.net destination acl intra_dst dst 192.168.2.0/24 # intra.tachtler.net destination # Tachtler - disabled IPv6 - # default: acl localnet src fc00::/7 # RFC 4193 local private network range # default: acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines acl SSL_ports port 443 # Tachtler - Safe_ports configuration - acl Safe_ports port 80 # http acl Safe_ports port 21 # ftp acl Safe_ports port 443 # https # default: acl Safe_ports port 70 # gopher # default: acl Safe_ports port 210 # wais acl Safe_ports port 1025-65535 # unregistered ports # default: acl Safe_ports port 280 # http-mgmt # default: acl Safe_ports port 488 # gss-http # default: acl Safe_ports port 591 # filemaker # default: acl Safe_ports port 777 # multiling http # Tachtler - CONNECT configuration - # Tachtler - Pidgin acl pidgin_CONNECT_ports port 5190 # Pidgin (proxy) acl pidgin_CONNECT_ports port 5222-5223 # Pidgin # Tachtler - AirDroid acl airdroid_CONNECT_ports port 8888-8890 # AirDroid # Tachtler - LDAP authentication - acl ldap_auth proxy_auth REQUIRED acl CONNECT method CONNECT # Tachtler - ACL follow_x_forwarded_for configuration - follow_x_forwarded_for allow localhost follow_x_forwarded_for allow idmz_net follow_x_forwarded_for allow intra_net # Tachtler - ACL dstdomain (Destination Domain) configuration - # Tachtler - Microsoft Windows-Update acl windowsupdate_CONNECT_dstdomain dstdomain www.update.microsoft.com acl windowsupdate_CONNECT_dstdomain dstdomain sls.micrsoft.com acl windowsupdate dstdomain .windowsupdate.microsoft.com acl windowsupdate dstdomain download.microsoft.com acl windowsupdate dstdomain .update.microsoft.com acl windowsupdate dstdomain .download.windowsupdate.com acl windowsupdate dstdomain dmd.metaservices.microsoft.com acl windowsupdate dstdomain redir.metaservices.microsoft.com acl windowsupdate dstdomain images.metaservices.microsoft.com acl windowsupdate dstdomain c.microsoft.com acl windowsupdate dstdomain wustat.windows.com acl windowsupdate dstdomain crl.microsoft.com acl windowsupdate dstdomain ctldl.windowsupdate.com acl windowsupdate dstdomain sls.microsoft.com acl windowsupdate dstdomain productactivation.one.microsoft.com acl windowsupdate dstdomain ntservicepack.microsoft.com acl windowsupdate dstdomain watson.microsoft.com acl windowsupdate dstdomain www.microsoft.com acl windowsupdate dstdomain www.msftncsi.com acl windowsupdate dstdomain spynet2.microsoft.com acl windowsupdate dstdomain sqm.telemetry.microsoft.com acl windowsupdate dstdomain iecvlist.microsoft.com acl windowsupdate dstdomain sqm.microsoft.com # Tachtler - Pidgin acl pidgin_CONNECT_dstdomain dstdomain proxy.eu.jabber.org acl pidgin_CONNECT_dstdomain dstdomain slogin.icq.com # Tachtler - ACL url-regex (URL regular expression) configuration - # Tachtler - Microsoft Windows Productactivation acl noauthsites url_regex productactivation\.one\.microsoft\.com:443 acl noauthsites url_regex activation\.sls\.microsoft\.com:443 # Tachtler - Microsoft Windows Online-Help acl noauthsites url_regex windowshelp\.microsoft\.com/* # Tachtler - Microsoft Internet Explorer Search-Engine-Updates acl noauthsites url_regex www\.iegallery\.com/de/* # # Recommended minimum Access Permission configuration: # # Deny requests to certain unsafe ports http_access deny !Safe_ports # Deny CONNECT to other than secure SSL ports # Tachtler # default: http_access deny CONNECT !SSL_ports http_access deny CONNECT !SSL_ports !pidgin_CONNECT_ports !airdroid_CONNECT_ports # Only allow cachemgr access from localhost http_access allow localhost manager http_access deny manager # We strongly recommend the following be uncommented to protect innocent # web applications running on the proxy server who think the only # one who can access services on "localhost" is a local user # Tachtler - enabled, deny access to localhost via squid proxy - # default: #http_access deny to_localhost http_access deny to_localhost # # INSERT YOUR OWN RULE(S) HERE TO ALLOW ACCESS FROM YOUR CLIENTS # # Example rule allowing access from your local networks. # Adapt localnet in the ACL section to list your (internal) IP networks # from where browsing should be allowed # Tachtler - access rules - # default: http_access allow localnet # default: http_access allow localhost # Tachtler - Microsoft Windows-Update http_access allow CONNECT windowsupdate_CONNECT_dstdomain intra_net http_access allow windowsupdate intra_net # Tachtler - Pidgin http_access allow CONNECT pidgin_CONNECT_dstdomain intra_net http_access allow pidgin_CONNECT_ports intra_net # Tachtler - AirDroid http_access allow airdroid_CONNECT_ports intra_net # Tachtler - Access part of local networks without authentication - http_access allow intra_net idmz_dst http_access allow intra_net edmz_dst # Tachtler - LDAP authentication - http_access allow localhost http_access allow idmz_net http_access allow edmz_net http_access allow intra_net noauthsites http_access allow intra_net ldap_auth # And finally deny all other access to this proxy http_access deny all # Squid normally listens to port 3128 http_port 3128 # Uncomment and adjust the following to add a disk cache directory. #cache_dir ufs /var/spool/squid 100 16 256 # Leave coredumps in the first cache dir coredump_dir /var/spool/squid # # Add any of your own refresh_pattern entries above these. # refresh_pattern ^ftp: 1440 20% 10080 refresh_pattern ^gopher: 1440 0% 1440 refresh_pattern -i (/cgi-bin/|\?) 0 0% 0 refresh_pattern . 0 20% 4320 # Tachtler - Microsoft Windows-Update # Tachtler - CAUTION - violates HTTP, but necessary! refresh_pattern -i microsoft.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windowsupdate.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windows.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims
Erklärungen:
# Example rule allowing access from your local networks. # Adapt to list your (internal) IP networks from where browsing # should be allowed # Tachtler - disabled default localnet configuration - # default: acl localnet src 10.0.0.0/8 # RFC1918 possible internal network # default: acl localnet src 172.16.0.0/12 # RFC1918 possible internal network # default: acl localnet src 192.168.0.0/16 # RFC1918 possible internal network acl idmz_net src 192.168.0.0/24 # idmz.tachtler.net acl edmz_net src 192.168.1.0/24 # edmz.tachtler.net acl intra_net src 192.168.2.0/24 # intra.tachtler.net acl edmz_dst dst 192.168.0.0/24 # edmz.tachtler.net destination acl idmz_dst dst 192.168.1.0/24 # idmz.tachtler.net destination acl intra_dst dst 192.168.2.0/24 # intra.tachtler.net destination # Tachtler - disabled IPv6 - # default: acl localnet src fc00::/7 # RFC 4193 local private network range # default: acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines
acl edmz_dst dst 192.168.0.0/24 # edmz.tachtler.net destination
Definition einer ACL mit dem Namen: idmz_dst und hier, des Ziel-IP-Adressbereichs 192.168.0.0/24.
acl idmz_dst dst 192.168.1.0/24 # idmz.tachtler.net destination
Definition einer ACL mit dem Namen: edmz_dst und hier, des Ziel-IP-Adressbereichs 192.168.1.0/24.
acl intra_dst dst 192.168.2.0/24 # intra.tachtler.net destination
Definition einer ACL mit dem Namen: intra_dst und hier, des Ziel-IP-Adressbereichs 192.168.2.0/24.
Es müssen alle internen Netze, nochmals auch als Ziel-IP-Adressbereich (destination) definiert werden.

# Example rule allowing access from your local networks. # Adapt localnet in the ACL section to list your (internal) IP networks # from where browsing should be allowed # Tachtler - access rules - # default: http_access allow localnet # default: http_access allow localhost # Tachtler - Microsoft Windows-Update http_access allow CONNECT windowsupdate_CONNECT_dstdomain intra_net http_access allow windowsupdate intra_net # Tachtler - Pidgin http_access allow CONNECT pidgin_CONNECT_dstdomain intra_net http_access allow pidgin_CONNECT_ports intra_net # Tachtler - AirDroid http_access allow airdroid_CONNECT_ports intra_net # Tachtler - Access part of local networks without authentication - http_access allow intra_net idmz_dst http_access allow intra_net edmz_dst # Tachtler - LDAP authentication - http_access allow localhost http_access allow idmz_net http_access allow edmz_net http_access allow intra_net noauthsites http_access allow intra_net ldap_auth
http_access allow intra_net idmz_dst
Wenn ein Client aus der ACL in dem das Netz
intra_net
definiert ist stammt, und auf das in der ACL
idmz_dst
genannte Netz zugreifen möchte, kann dies OHNE LDAP-Authentifizierung erfolgen.
http_access allow intra_net edmz_dst
Wenn ein Client aus der ACL in dem das Netz
intra_net
definiert ist stammt, und auf das in der ACL
edmz_dst
genannte Netz zugreifen möchte, kann dies OHNE LDAP-Authentifizierung erfolgen.
Administrative-Konfiguration
Nachfolgende Einstellungen sind sogenannte Administrative Parameter des Squid Proxy-Server.
Nachfolgende Ergänzungen sind in der Konfigurationsdatei
/etc/squid/squid.conf
notwendig, um die Administrativen Parameter Definitionen im Squid Proxy-Server einsetzen zu können:
(Komplette Konfigurationsdatei)
# # Recommended minimum configuration: # # Tachtler - LDAP authentication - auth_param basic program /usr/lib64/squid/basic_ldap_auth -b "ou=People,dc=tachtler,dc=net" -f "uid=%s" -h ldap.idmz.tachtler.net -D "cn=Ersatzbenutzer,dc=tachtler,dc=net" -W /etc/squid/ldap_passwd auth_param basic utf8 on auth_param basic children 5 startup=1 idle=1 concurrency=0 auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein! auth_param basic credentialsttl 60 minutes auth_param basic casesensitive off # Example rule allowing access from your local networks. # Adapt to list your (internal) IP networks from where browsing # should be allowed # Tachtler - disabled default localnet configuration - # default: acl localnet src 10.0.0.0/8 # RFC1918 possible internal network # default: acl localnet src 172.16.0.0/12 # RFC1918 possible internal network # default: acl localnet src 192.168.0.0/16 # RFC1918 possible internal network acl idmz_net src 192.168.0.0/24 # idmz.tachtler.net acl edmz_net src 192.168.1.0/24 # edmz.tachtler.net acl intra_net src 192.168.2.0/24 # intra.tachtler.net acl edmz_dst dst 192.168.0.0/24 # edmz.tachtler.net destination acl idmz_dst dst 192.168.1.0/24 # idmz.tachtler.net destination acl intra_dst dst 192.168.2.0/24 # intra.tachtler.net destination # Tachtler - disabled IPv6 - # default: acl localnet src fc00::/7 # RFC 4193 local private network range # default: acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines acl SSL_ports port 443 # Tachtler - Safe_ports configuration - acl Safe_ports port 80 # http acl Safe_ports port 21 # ftp acl Safe_ports port 443 # https # default: acl Safe_ports port 70 # gopher # default: acl Safe_ports port 210 # wais acl Safe_ports port 1025-65535 # unregistered ports # default: acl Safe_ports port 280 # http-mgmt # default: acl Safe_ports port 488 # gss-http # default: acl Safe_ports port 591 # filemaker # default: acl Safe_ports port 777 # multiling http # Tachtler - CONNECT configuration - # Tachtler - Pidgin acl pidgin_CONNECT_ports port 5190 # Pidgin (proxy) acl pidgin_CONNECT_ports port 5222-5223 # Pidgin # Tachtler - AirDroid acl airdroid_CONNECT_ports port 8888-8890 # AirDroid # Tachtler - LDAP authentication - acl ldap_auth proxy_auth REQUIRED acl CONNECT method CONNECT # Tachtler - ACL follow_x_forwarded_for configuration - follow_x_forwarded_for allow localhost follow_x_forwarded_for allow idmz_net follow_x_forwarded_for allow intra_net # Tachtler - ACL dstdomain (Destination Domain) configuration - # Tachtler - Microsoft Windows-Update acl windowsupdate_CONNECT_dstdomain dstdomain www.update.microsoft.com acl windowsupdate_CONNECT_dstdomain dstdomain sls.micrsoft.com acl windowsupdate dstdomain .windowsupdate.microsoft.com acl windowsupdate dstdomain download.microsoft.com acl windowsupdate dstdomain .update.microsoft.com acl windowsupdate dstdomain .download.windowsupdate.com acl windowsupdate dstdomain dmd.metaservices.microsoft.com acl windowsupdate dstdomain redir.metaservices.microsoft.com acl windowsupdate dstdomain images.metaservices.microsoft.com acl windowsupdate dstdomain c.microsoft.com acl windowsupdate dstdomain wustat.windows.com acl windowsupdate dstdomain crl.microsoft.com acl windowsupdate dstdomain ctldl.windowsupdate.com acl windowsupdate dstdomain sls.microsoft.com acl windowsupdate dstdomain productactivation.one.microsoft.com acl windowsupdate dstdomain ntservicepack.microsoft.com acl windowsupdate dstdomain watson.microsoft.com acl windowsupdate dstdomain www.microsoft.com acl windowsupdate dstdomain www.msftncsi.com acl windowsupdate dstdomain spynet2.microsoft.com acl windowsupdate dstdomain sqm.telemetry.microsoft.com acl windowsupdate dstdomain iecvlist.microsoft.com acl windowsupdate dstdomain sqm.microsoft.com # Tachtler - Pidgin acl pidgin_CONNECT_dstdomain dstdomain proxy.eu.jabber.org acl pidgin_CONNECT_dstdomain dstdomain slogin.icq.com # Tachtler - ACL url-regex (URL regular expression) configuration - # Tachtler - Microsoft Windows Productactivation acl noauthsites url_regex productactivation\.one\.microsoft\.com:443 acl noauthsites url_regex activation\.sls\.microsoft\.com:443 # Tachtler - Microsoft Windows Online-Help acl noauthsites url_regex windowshelp\.microsoft\.com/* # Tachtler - Microsoft Internet Explorer Search-Engine-Updates acl noauthsites url_regex www\.iegallery\.com/de/* # # Recommended minimum Access Permission configuration: # # Deny requests to certain unsafe ports http_access deny !Safe_ports # Deny CONNECT to other than secure SSL ports # Tachtler # default: http_access deny CONNECT !SSL_ports http_access deny CONNECT !SSL_ports !pidgin_CONNECT_ports !airdroid_CONNECT_ports # Only allow cachemgr access from localhost http_access allow localhost manager http_access deny manager # We strongly recommend the following be uncommented to protect innocent # web applications running on the proxy server who think the only # one who can access services on "localhost" is a local user # Tachtler - enabled, deny access to localhost via squid proxy - # default: #http_access deny to_localhost http_access deny to_localhost # # INSERT YOUR OWN RULE(S) HERE TO ALLOW ACCESS FROM YOUR CLIENTS # # Example rule allowing access from your local networks. # Adapt localnet in the ACL section to list your (internal) IP networks # from where browsing should be allowed # Tachtler - access rules - # default: http_access allow localnet # default: http_access allow localhost # Tachtler - Microsoft Windows-Update http_access allow CONNECT windowsupdate_CONNECT_dstdomain intra_net http_access allow windowsupdate intra_net # Tachtler - Pidgin http_access allow CONNECT pidgin_CONNECT_dstdomain intra_net http_access allow pidgin_CONNECT_ports intra_net # Tachtler - AirDroid http_access allow airdroid_CONNECT_ports intra_net # Tachtler - Access part of local networks without authentication - http_access allow intra_net idmz_dst http_access allow intra_net edmz_dst # Tachtler - LDAP authentication - http_access allow localhost http_access allow idmz_net http_access allow edmz_net http_access allow intra_net noauthsites http_access allow intra_net ldap_auth # And finally deny all other access to this proxy http_access deny all # Squid normally listens to port 3128 http_port 3128 # Uncomment and adjust the following to add a disk cache directory. #cache_dir ufs /var/spool/squid 100 16 256 # Leave coredumps in the first cache dir coredump_dir /var/spool/squid # # Add any of your own refresh_pattern entries above these. # refresh_pattern ^ftp: 1440 20% 10080 refresh_pattern ^gopher: 1440 0% 1440 refresh_pattern -i (/cgi-bin/|\?) 0 0% 0 refresh_pattern . 0 20% 4320 # Tachtler - Microsoft Windows-Update # Tachtler - CAUTION - violates HTTP, but necessary! refresh_pattern -i microsoft.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windowsupdate.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windows.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims # Tachtler - Administrative parameter - # Tachtler - cache_mgr - default: root, presents the mail to user for e-mails from squid-cache cache_mgr squid # Tachtler - mail_from - presents the rcpt to user for emails from squid-cache mail_from squid-cache@tachtler.net # Tachtler - visible_hostname - hostname presented in error messages etc. visible_hostname proxy.idmz.tachtler.net # Tachtler - unique_hostname - hostname, that identifies this squid-cache unique_hostname proxy.idmz.tachtler.net # Tachtler - hostname_aliases - a list of hostnames, thas presented in the DNS for this squid-cache hostname_aliases server50.idmz.tachtler.net
Erklärungen:
# Tachtler - Administrative parameter - # Tachtler - cache_mgr - default: root, presents the mail to user for e-mails from squid-cache cache_mgr squid # Tachtler - mail_from - presents the rcpt to user for emails from squid-cache mail_from squid-cache@tachtler.net # Tachtler - visible_hostname - hostname presented in error messages etc. visible_hostname proxy.idmz.tachtler.net # Tachtler - unique_hostname - hostname, that identifies this squid-cache unique_hostname proxy.idmz.tachtler.net # Tachtler - hostname_aliases - a list of hostnames, thas presented in the DNS for this squid-cache hostname_aliases server50.idmz.tachtler.net
cache_mgr squid
Definiert den Benutzer, welcher e-Mails empfängt, wenn der Squid Proxy-Server stoppt. Der Standardbenutzer wäre root.
mail_from squid-cache@tachtler.net
Definiert die e-Mail-Adresse, welche als Absender verwendet wird, wenn der Squid Proxy-Server stoppt.
visible_hostname proxy.idmz.tachtler.net
Definiert den „Hostnamen“, welcher in z.B. Fehlermeldungen angegeben wird. Falls hier kein Wert gesetzt wird, wird der „Hostname“ über gethostname() ermittelt.
unique_hostname proxy.idmz.tachtler.net
Definiert den „Hostname“ als eindeutigen „Hostnamen“ für diesen Squid Proxy-Server, was beim Einsatz von mehreren Squid Proxy-Servern hauptsächlich zum tragen kommt.
hostname_aliases server50.idmz.tachtler.net
Definiert weitere im DNS hinterlegte „Hostnamen“ für diesen Squid Proxy-Server.
Fehlerseiten-Konfiguration
Nachfolgende Einstellungen bestimmen die Fehlerseiten-Konfiguration, wie z.B. die anzuzeigende Sprache des Squid Proxy-Server, z.B. auf Fehlerseiten.
Fehlerseiten Anpassungen
Nachfolgende Anpassung des CSS der Fehlerseite, soll das Nachladen des Squid-Logos durch den Squid Proxy-Server von der Internet-Seite
bei jedem Aufruf der Fehlerseite, gegen das Laden des Squid-Logos durch den Apache HTTP Webserver auf dem Squid Proxy-Server ersetzen.
Dazu ist nachfolgende Anpassung an der Konfigurationsdatei
/etc/squid/errorpage.css
erforderlich:
(komplette Konfigurationsdatei)
/* Stylesheet for Squid Error pages Adapted from design by Free CSS Templates http://www.freecsstemplates.org Released for free under a Creative Commons Attribution 2.5 License */ /* Page basics */ * { font-family: verdana, sans-serif; } html body { margin: 0; padding: 0; background: #efefef; font-size: 12px; color: #1e1e1e; } /* Page displayed title area */ #titles { margin-left: 15px; padding: 10px; padding-left: 100px; /* Tachtler */ /* default: background: url('http://www.squid-cache.org/Artwork/SN.png') no-repeat left; */ background: url('http://squid.tachtler.net/icons/SN.png') no-repeat left; } /* initial title */ #titles h1 { color: #000000; } #titles h2 { color: #000000; } /* special event: FTP success page titles */ #titles ftpsuccess { background-color:#00ff00; width:100%; } /* Page displayed body content area */ #content { padding: 10px; background: #ffffff; } /* General text */ p { } /* error brief description */ #error p { } /* some data which may have caused the problem */ #data { } /* the error message received from the system or other software */ #sysmsg { } pre { font-family:sans-serif; } /* special event: FTP / Gopher directory listing */ #dirmsg { font-family: courier; color: black; font-size: 10pt; } #dirlisting { margin-left: 2%; margin-right: 2%; } #dirlisting tr.entry td.icon,td.filename,td.size,td.date { border-bottom: groove; } #dirlisting td.size { width: 50px; text-align: right; padding-right: 5px; } /* horizontal lines */ hr { margin: 0; } /* page displayed footer area */ #footer { font-size: 9px; padding-left: 10px; }
/* Tachtler */ /* default: background: url('http://www.squid-cache.org/Artwork/SN.png') no-repeat left; */ background: url('http://squid.tachtler.net/icons/SN.png') no-repeat left;
Anpassung des Herunterladen des Squid-Logos vom Apache HTTP Webserver der auf dem Squid Proxy-Server läuft.
Spracheinstellungen
Nachfolgende Ergänzungen sind in der Konfigurationsdatei
/etc/squid/squid.conf
notwendig, um die Fehlerseiten Definitionen im Squid Proxy-Server einsetzen zu können:
(Komplette Konfigurationsdatei)
# # Recommended minimum configuration: # # Tachtler - LDAP authentication - auth_param basic program /usr/lib64/squid/basic_ldap_auth -b "ou=People,dc=tachtler,dc=net" -f "uid=%s" -h ldap.idmz.tachtler.net -D "cn=Ersatzbenutzer,dc=tachtler,dc=net" -W /etc/squid/ldap_passwd auth_param basic utf8 on auth_param basic children 5 startup=1 idle=1 concurrency=0 auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein! auth_param basic credentialsttl 60 minutes auth_param basic casesensitive off # Example rule allowing access from your local networks. # Adapt to list your (internal) IP networks from where browsing # should be allowed # Tachtler - disabled default localnet configuration - # default: acl localnet src 10.0.0.0/8 # RFC1918 possible internal network # default: acl localnet src 172.16.0.0/12 # RFC1918 possible internal network # default: acl localnet src 192.168.0.0/16 # RFC1918 possible internal network acl idmz_net src 192.168.0.0/24 # idmz.tachtler.net acl edmz_net src 192.168.1.0/24 # edmz.tachtler.net acl intra_net src 192.168.2.0/24 # intra.tachtler.net acl edmz_dst dst 192.168.0.0/24 # edmz.tachtler.net destination acl idmz_dst dst 192.168.1.0/24 # idmz.tachtler.net destination acl intra_dst dst 192.168.2.0/24 # intra.tachtler.net destination # Tachtler - disabled IPv6 - # default: acl localnet src fc00::/7 # RFC 4193 local private network range # default: acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines acl SSL_ports port 443 # Tachtler - Safe_ports configuration - acl Safe_ports port 80 # http acl Safe_ports port 21 # ftp acl Safe_ports port 443 # https # default: acl Safe_ports port 70 # gopher # default: acl Safe_ports port 210 # wais acl Safe_ports port 1025-65535 # unregistered ports # default: acl Safe_ports port 280 # http-mgmt # default: acl Safe_ports port 488 # gss-http # default: acl Safe_ports port 591 # filemaker # default: acl Safe_ports port 777 # multiling http # Tachtler - CONNECT configuration - # Tachtler - Pidgin acl pidgin_CONNECT_ports port 5190 # Pidgin (proxy) acl pidgin_CONNECT_ports port 5222-5223 # Pidgin # Tachtler - AirDroid acl airdroid_CONNECT_ports port 8888-8890 # AirDroid # Tachtler - LDAP authentication - acl ldap_auth proxy_auth REQUIRED acl CONNECT method CONNECT # Tachtler - ACL follow_x_forwarded_for configuration - follow_x_forwarded_for allow localhost follow_x_forwarded_for allow idmz_net follow_x_forwarded_for allow intra_net # Tachtler - ACL dstdomain (Destination Domain) configuration - # Tachtler - Microsoft Windows-Update acl windowsupdate_CONNECT_dstdomain dstdomain www.update.microsoft.com acl windowsupdate_CONNECT_dstdomain dstdomain sls.micrsoft.com acl windowsupdate dstdomain .windowsupdate.microsoft.com acl windowsupdate dstdomain download.microsoft.com acl windowsupdate dstdomain .update.microsoft.com acl windowsupdate dstdomain .download.windowsupdate.com acl windowsupdate dstdomain dmd.metaservices.microsoft.com acl windowsupdate dstdomain redir.metaservices.microsoft.com acl windowsupdate dstdomain images.metaservices.microsoft.com acl windowsupdate dstdomain c.microsoft.com acl windowsupdate dstdomain wustat.windows.com acl windowsupdate dstdomain crl.microsoft.com acl windowsupdate dstdomain ctldl.windowsupdate.com acl windowsupdate dstdomain sls.microsoft.com acl windowsupdate dstdomain productactivation.one.microsoft.com acl windowsupdate dstdomain ntservicepack.microsoft.com acl windowsupdate dstdomain watson.microsoft.com acl windowsupdate dstdomain www.microsoft.com acl windowsupdate dstdomain www.msftncsi.com acl windowsupdate dstdomain spynet2.microsoft.com acl windowsupdate dstdomain sqm.telemetry.microsoft.com acl windowsupdate dstdomain iecvlist.microsoft.com acl windowsupdate dstdomain sqm.microsoft.com # Tachtler - Pidgin acl pidgin_CONNECT_dstdomain dstdomain proxy.eu.jabber.org acl pidgin_CONNECT_dstdomain dstdomain slogin.icq.com # Tachtler - ACL url-regex (URL regular expression) configuration - # Tachtler - Microsoft Windows Productactivation acl noauthsites url_regex productactivation\.one\.microsoft\.com:443 acl noauthsites url_regex activation\.sls\.microsoft\.com:443 # Tachtler - Microsoft Windows Online-Help acl noauthsites url_regex windowshelp\.microsoft\.com/* # Tachtler - Microsoft Internet Explorer Search-Engine-Updates acl noauthsites url_regex www\.iegallery\.com/de/* # # Recommended minimum Access Permission configuration: # # Deny requests to certain unsafe ports http_access deny !Safe_ports # Deny CONNECT to other than secure SSL ports # Tachtler # default: http_access deny CONNECT !SSL_ports http_access deny CONNECT !SSL_ports !pidgin_CONNECT_ports !airdroid_CONNECT_ports # Only allow cachemgr access from localhost http_access allow localhost manager http_access deny manager # We strongly recommend the following be uncommented to protect innocent # web applications running on the proxy server who think the only # one who can access services on "localhost" is a local user # Tachtler - enabled, deny access to localhost via squid proxy - # default: #http_access deny to_localhost http_access deny to_localhost # # INSERT YOUR OWN RULE(S) HERE TO ALLOW ACCESS FROM YOUR CLIENTS # # Example rule allowing access from your local networks. # Adapt localnet in the ACL section to list your (internal) IP networks # from where browsing should be allowed # Tachtler - access rules - # default: http_access allow localnet # default: http_access allow localhost # Tachtler - Microsoft Windows-Update http_access allow CONNECT windowsupdate_CONNECT_dstdomain intra_net http_access allow windowsupdate intra_net # Tachtler - Pidgin http_access allow CONNECT pidgin_CONNECT_dstdomain intra_net http_access allow pidgin_CONNECT_ports intra_net # Tachtler - AirDroid http_access allow airdroid_CONNECT_ports intra_net # Tachtler - Access part of local networks without authentication - http_access allow intra_net idmz_dst http_access allow intra_net edmz_dst # Tachtler - LDAP authentication - http_access allow localhost http_access allow idmz_net http_access allow edmz_net http_access allow intra_net noauthsites http_access allow intra_net ldap_auth # And finally deny all other access to this proxy http_access deny all # Squid normally listens to port 3128 http_port 3128 # Uncomment and adjust the following to add a disk cache directory. #cache_dir ufs /var/spool/squid 100 16 256 # Leave coredumps in the first cache dir coredump_dir /var/spool/squid # # Add any of your own refresh_pattern entries above these. # refresh_pattern ^ftp: 1440 20% 10080 refresh_pattern ^gopher: 1440 0% 1440 refresh_pattern -i (/cgi-bin/|\?) 0 0% 0 refresh_pattern . 0 20% 4320 # Tachtler - Microsoft Windows-Update # Tachtler - CAUTION - violates HTTP, but necessary! refresh_pattern -i microsoft.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windowsupdate.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windows.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims # Tachtler - Administrative parameter - # Tachtler - cache_mgr - default: root, presents the mail to user for e-mails from squid-cache cache_mgr squid # Tachtler - mail_from - presents the rcpt to user for emails from squid-cache mail_from squid-cache@tachtler.net # Tachtler - visible_hostname - hostname presented in error messages etc. visible_hostname proxy.idmz.tachtler.net # Tachtler - unique_hostname - hostname, that identifies this squid-cache unique_hostname proxy.idmz.tachtler.net # Tachtler - hostname_aliases - a list of hostnames, thas presented in the DNS for this squid-cache hostname_aliases server50.idmz.tachtler.net # Tachtler - Error page language and settings - # Tachtler - error_default_language # error_directory /usr/share/squid/errors/de-tachtler # error_default_language de-tachtler error_default_language de-de
Erklärungen:
error_default_language de-de
Definition, in welcher Sprache die Fehlermeldungen angezeigt werden sollen.
Falls Veränderungen an den Fehlermeldungen, bzw. den HTML-Seiten vorgenommen werden sollen, ist eine neues Verzeichnis zu erstellen, welches z.B. durch kopieren eines bestehenden Verzeichnisses, hier z.B. /usr/share/squid/errors/de nach z.B. /usr/share/squid/errors/de-tachtler mit nachfolgenden Befehl durchgeführt werden kann:
# cp -ar /usr/share/squid/errors/de /usr/share/squid/errors/de-tachtler
Anschließend muss dieses das eben neu erstellte Verzeichnis mit nachfolgenden Änderungen eingebunden werden:
error_directory /usr/share/squid/errors/de-tachtler
Angabe der Speicherortes, wo die Fehlermeldungen abgelegt sind.
error_default_language de-tachtler
Definition, in welcher Sprache die Fehlermeldungen angezeigt werden sollen.
Logdatei-Konfiguration
Nachfolgende Einstellungen beeinflussen die Ausgabe der Logdatei des Squid Proxy-Server.
Nachfolgende Ergänzungen sind in der Konfigurationsdatei
/etc/squid/squid.conf
notwendig, um die Logdatei Definitionen im Squid Proxy-Server einsetzen zu können:
(Komplette Konfigurationsdatei)
# # Recommended minimum configuration: # # Tachtler - LDAP authentication - auth_param basic program /usr/lib64/squid/basic_ldap_auth -b "ou=People,dc=tachtler,dc=net" -f "uid=%s" -h ldap.idmz.tachtler.net -D "cn=Ersatzbenutzer,dc=tachtler,dc=net" -W /etc/squid/ldap_passwd auth_param basic utf8 on auth_param basic children 5 startup=1 idle=1 concurrency=0 auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein! auth_param basic credentialsttl 60 minutes auth_param basic casesensitive off # Example rule allowing access from your local networks. # Adapt to list your (internal) IP networks from where browsing # should be allowed # Tachtler - disabled default localnet configuration - # default: acl localnet src 10.0.0.0/8 # RFC1918 possible internal network # default: acl localnet src 172.16.0.0/12 # RFC1918 possible internal network # default: acl localnet src 192.168.0.0/16 # RFC1918 possible internal network acl idmz_net src 192.168.0.0/24 # idmz.tachtler.net acl edmz_net src 192.168.1.0/24 # edmz.tachtler.net acl intra_net src 192.168.2.0/24 # intra.tachtler.net acl edmz_dst dst 192.168.0.0/24 # edmz.tachtler.net destination acl idmz_dst dst 192.168.1.0/24 # idmz.tachtler.net destination acl intra_dst dst 192.168.2.0/24 # intra.tachtler.net destination # Tachtler - disabled IPv6 - # default: acl localnet src fc00::/7 # RFC 4193 local private network range # default: acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines acl SSL_ports port 443 # Tachtler - Safe_ports configuration - acl Safe_ports port 80 # http acl Safe_ports port 21 # ftp acl Safe_ports port 443 # https # default: acl Safe_ports port 70 # gopher # default: acl Safe_ports port 210 # wais acl Safe_ports port 1025-65535 # unregistered ports # default: acl Safe_ports port 280 # http-mgmt # default: acl Safe_ports port 488 # gss-http # default: acl Safe_ports port 591 # filemaker # default: acl Safe_ports port 777 # multiling http # Tachtler - CONNECT configuration - # Tachtler - Pidgin acl pidgin_CONNECT_ports port 5190 # Pidgin (proxy) acl pidgin_CONNECT_ports port 5222-5223 # Pidgin # Tachtler - AirDroid acl airdroid_CONNECT_ports port 8888-8890 # AirDroid # Tachtler - LDAP authentication - acl ldap_auth proxy_auth REQUIRED acl CONNECT method CONNECT # Tachtler - ACL follow_x_forwarded_for configuration - follow_x_forwarded_for allow localhost follow_x_forwarded_for allow idmz_net follow_x_forwarded_for allow intra_net # Tachtler - ACL dstdomain (Destination Domain) configuration - # Tachtler - Microsoft Windows-Update acl windowsupdate_CONNECT_dstdomain dstdomain www.update.microsoft.com acl windowsupdate_CONNECT_dstdomain dstdomain sls.micrsoft.com acl windowsupdate dstdomain .windowsupdate.microsoft.com acl windowsupdate dstdomain download.microsoft.com acl windowsupdate dstdomain .update.microsoft.com acl windowsupdate dstdomain .download.windowsupdate.com acl windowsupdate dstdomain dmd.metaservices.microsoft.com acl windowsupdate dstdomain redir.metaservices.microsoft.com acl windowsupdate dstdomain images.metaservices.microsoft.com acl windowsupdate dstdomain c.microsoft.com acl windowsupdate dstdomain wustat.windows.com acl windowsupdate dstdomain crl.microsoft.com acl windowsupdate dstdomain ctldl.windowsupdate.com acl windowsupdate dstdomain sls.microsoft.com acl windowsupdate dstdomain productactivation.one.microsoft.com acl windowsupdate dstdomain ntservicepack.microsoft.com acl windowsupdate dstdomain watson.microsoft.com acl windowsupdate dstdomain www.microsoft.com acl windowsupdate dstdomain www.msftncsi.com acl windowsupdate dstdomain spynet2.microsoft.com acl windowsupdate dstdomain sqm.telemetry.microsoft.com acl windowsupdate dstdomain iecvlist.microsoft.com acl windowsupdate dstdomain sqm.microsoft.com # Tachtler - Pidgin acl pidgin_CONNECT_dstdomain dstdomain proxy.eu.jabber.org acl pidgin_CONNECT_dstdomain dstdomain slogin.icq.com # Tachtler - ACL url-regex (URL regular expression) configuration - # Tachtler - Microsoft Windows Productactivation acl noauthsites url_regex productactivation\.one\.microsoft\.com:443 acl noauthsites url_regex activation\.sls\.microsoft\.com:443 # Tachtler - Microsoft Windows Online-Help acl noauthsites url_regex windowshelp\.microsoft\.com/* # Tachtler - Microsoft Internet Explorer Search-Engine-Updates acl noauthsites url_regex www\.iegallery\.com/de/* # # Recommended minimum Access Permission configuration: # # Deny requests to certain unsafe ports http_access deny !Safe_ports # Deny CONNECT to other than secure SSL ports # Tachtler # default: http_access deny CONNECT !SSL_ports http_access deny CONNECT !SSL_ports !pidgin_CONNECT_ports !airdroid_CONNECT_ports # Only allow cachemgr access from localhost http_access allow localhost manager http_access deny manager # We strongly recommend the following be uncommented to protect innocent # web applications running on the proxy server who think the only # one who can access services on "localhost" is a local user # Tachtler - enabled, deny access to localhost via squid proxy - # default: #http_access deny to_localhost http_access deny to_localhost # # INSERT YOUR OWN RULE(S) HERE TO ALLOW ACCESS FROM YOUR CLIENTS # # Example rule allowing access from your local networks. # Adapt localnet in the ACL section to list your (internal) IP networks # from where browsing should be allowed # Tachtler - access rules - # default: http_access allow localnet # default: http_access allow localhost # Tachtler - Microsoft Windows-Update http_access allow CONNECT windowsupdate_CONNECT_dstdomain intra_net http_access allow windowsupdate intra_net # Tachtler - Pidgin http_access allow CONNECT pidgin_CONNECT_dstdomain intra_net http_access allow pidgin_CONNECT_ports intra_net # Tachtler - AirDroid http_access allow airdroid_CONNECT_ports intra_net # Tachtler - Access part of local networks without authentication - http_access allow intra_net idmz_dst http_access allow intra_net edmz_dst # Tachtler - LDAP authentication - http_access allow localhost http_access allow idmz_net http_access allow edmz_net http_access allow intra_net noauthsites http_access allow intra_net ldap_auth # And finally deny all other access to this proxy http_access deny all # Squid normally listens to port 3128 http_port 3128 # Uncomment and adjust the following to add a disk cache directory. #cache_dir ufs /var/spool/squid 100 16 256 # Leave coredumps in the first cache dir coredump_dir /var/spool/squid # # Add any of your own refresh_pattern entries above these. # refresh_pattern ^ftp: 1440 20% 10080 refresh_pattern ^gopher: 1440 0% 1440 refresh_pattern -i (/cgi-bin/|\?) 0 0% 0 refresh_pattern . 0 20% 4320 # Tachtler - Microsoft Windows-Update # Tachtler - CAUTION - violates HTTP, but necessary! refresh_pattern -i microsoft.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windowsupdate.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windows.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims # Tachtler - Administrative parameter - # Tachtler - cache_mgr - default: root, presents the mail to user for e-mails from squid-cache cache_mgr squid # Tachtler - mail_from - presents the rcpt to user for emails from squid-cache mail_from squid-cache@tachtler.net # Tachtler - visible_hostname - hostname presented in error messages etc. visible_hostname proxy.idmz.tachtler.net # Tachtler - unique_hostname - hostname, that identifies this squid-cache unique_hostname proxy.idmz.tachtler.net # Tachtler - hostname_aliases - a list of hostnames, thas presented in the DNS for this squid-cache hostname_aliases server50.idmz.tachtler.net # Tachtler - Error page language and settings - # Tachtler - error_default_language error_default_language de-de # Tachtler - Logfile settings - # Tachtler - strip_query_terms - default: on - squid-cache strips query terms from requested URLs before logging. # This protects your users's privacy and reduces log size. # But you can disable this, to see the FULL URL used by squid-cache. strip_query_terms off
Erklärungen:
# Tachtler - Logfile settings - # Tachtler - strip_query_terms - default: on - squid-cache strips query terms from requested URLs before logging. # This protects your users's privacy and reduces log size. # But you can disable this, to see the FULL URL used by squid-cache. strip_query_terms off
Definiert, ob der Squid Proxy-Server die volle URL in die LOG-Datei schreibt, oder zum Schutz der Privatsphäre der Benutzer und um das LOG-Volumen zu reduzieren, Anfrage-Parameter innerhalb der URL nicht bei der LOG-Schreibung berücksichtigen soll.

DNS-Konfiguration
Nachfolgende Einstellungen beeinflussen die DNS-Abfrage Reihenfolge des Squid Proxy-Server.
Nachfolgende Ergänzungen sind in der Konfigurationsdatei
/etc/squid/squid.conf
notwendig, um die DNS-Abfrage Reihenfolge Definitionen im Squid Proxy-Server einsetzen zu können:
(Komplette Konfigurationsdatei)
# # Recommended minimum configuration: # # Tachtler - LDAP authentication - auth_param basic program /usr/lib64/squid/basic_ldap_auth -b "ou=People,dc=tachtler,dc=net" -f "uid=%s" -h ldap.idmz.tachtler.net -D "cn=Ersatzbenutzer,dc=tachtler,dc=net" -W /etc/squid/ldap_passwd auth_param basic utf8 on auth_param basic children 5 startup=1 idle=1 concurrency=0 auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein! auth_param basic credentialsttl 60 minutes auth_param basic casesensitive off # Example rule allowing access from your local networks. # Adapt to list your (internal) IP networks from where browsing # should be allowed # Tachtler - disabled default localnet configuration - # default: acl localnet src 10.0.0.0/8 # RFC1918 possible internal network # default: acl localnet src 172.16.0.0/12 # RFC1918 possible internal network # default: acl localnet src 192.168.0.0/16 # RFC1918 possible internal network acl idmz_net src 192.168.0.0/24 # idmz.tachtler.net acl edmz_net src 192.168.1.0/24 # edmz.tachtler.net acl intra_net src 192.168.2.0/24 # intra.tachtler.net acl edmz_dst dst 192.168.0.0/24 # edmz.tachtler.net destination acl idmz_dst dst 192.168.1.0/24 # idmz.tachtler.net destination acl intra_dst dst 192.168.2.0/24 # intra.tachtler.net destination # Tachtler - disabled IPv6 - # default: acl localnet src fc00::/7 # RFC 4193 local private network range # default: acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines acl SSL_ports port 443 # Tachtler - Safe_ports configuration - acl Safe_ports port 80 # http acl Safe_ports port 21 # ftp acl Safe_ports port 443 # https # default: acl Safe_ports port 70 # gopher # default: acl Safe_ports port 210 # wais acl Safe_ports port 1025-65535 # unregistered ports # default: acl Safe_ports port 280 # http-mgmt # default: acl Safe_ports port 488 # gss-http # default: acl Safe_ports port 591 # filemaker # default: acl Safe_ports port 777 # multiling http # Tachtler - CONNECT configuration - # Tachtler - Pidgin acl pidgin_CONNECT_ports port 5190 # Pidgin (proxy) acl pidgin_CONNECT_ports port 5222-5223 # Pidgin # Tachtler - AirDroid acl airdroid_CONNECT_ports port 8888-8890 # AirDroid # Tachtler - LDAP authentication - acl ldap_auth proxy_auth REQUIRED acl CONNECT method CONNECT # Tachtler - ACL follow_x_forwarded_for configuration - follow_x_forwarded_for allow localhost follow_x_forwarded_for allow idmz_net follow_x_forwarded_for allow intra_net # Tachtler - ACL dstdomain (Destination Domain) configuration - # Tachtler - Microsoft Windows-Update acl windowsupdate_CONNECT_dstdomain dstdomain www.update.microsoft.com acl windowsupdate_CONNECT_dstdomain dstdomain sls.micrsoft.com acl windowsupdate dstdomain .windowsupdate.microsoft.com acl windowsupdate dstdomain download.microsoft.com acl windowsupdate dstdomain .update.microsoft.com acl windowsupdate dstdomain .download.windowsupdate.com acl windowsupdate dstdomain dmd.metaservices.microsoft.com acl windowsupdate dstdomain redir.metaservices.microsoft.com acl windowsupdate dstdomain images.metaservices.microsoft.com acl windowsupdate dstdomain c.microsoft.com acl windowsupdate dstdomain wustat.windows.com acl windowsupdate dstdomain crl.microsoft.com acl windowsupdate dstdomain ctldl.windowsupdate.com acl windowsupdate dstdomain sls.microsoft.com acl windowsupdate dstdomain productactivation.one.microsoft.com acl windowsupdate dstdomain ntservicepack.microsoft.com acl windowsupdate dstdomain watson.microsoft.com acl windowsupdate dstdomain www.microsoft.com acl windowsupdate dstdomain www.msftncsi.com acl windowsupdate dstdomain spynet2.microsoft.com acl windowsupdate dstdomain sqm.telemetry.microsoft.com acl windowsupdate dstdomain iecvlist.microsoft.com acl windowsupdate dstdomain sqm.microsoft.com # Tachtler - Pidgin acl pidgin_CONNECT_dstdomain dstdomain proxy.eu.jabber.org acl pidgin_CONNECT_dstdomain dstdomain slogin.icq.com # Tachtler - ACL url-regex (URL regular expression) configuration - # Tachtler - Microsoft Windows Productactivation acl noauthsites url_regex productactivation\.one\.microsoft\.com:443 acl noauthsites url_regex activation\.sls\.microsoft\.com:443 # Tachtler - Microsoft Windows Online-Help acl noauthsites url_regex windowshelp\.microsoft\.com/* # Tachtler - Microsoft Internet Explorer Search-Engine-Updates acl noauthsites url_regex www\.iegallery\.com/de/* # # Recommended minimum Access Permission configuration: # # Deny requests to certain unsafe ports http_access deny !Safe_ports # Deny CONNECT to other than secure SSL ports # Tachtler # default: http_access deny CONNECT !SSL_ports http_access deny CONNECT !SSL_ports !pidgin_CONNECT_ports !airdroid_CONNECT_ports # Only allow cachemgr access from localhost http_access allow localhost manager http_access deny manager # We strongly recommend the following be uncommented to protect innocent # web applications running on the proxy server who think the only # one who can access services on "localhost" is a local user # Tachtler - enabled, deny access to localhost via squid proxy - # default: #http_access deny to_localhost http_access deny to_localhost # # INSERT YOUR OWN RULE(S) HERE TO ALLOW ACCESS FROM YOUR CLIENTS # # Example rule allowing access from your local networks. # Adapt localnet in the ACL section to list your (internal) IP networks # from where browsing should be allowed # Tachtler - access rules - # default: http_access allow localnet # default: http_access allow localhost # Tachtler - Microsoft Windows-Update http_access allow CONNECT windowsupdate_CONNECT_dstdomain intra_net http_access allow windowsupdate intra_net # Tachtler - Pidgin http_access allow CONNECT pidgin_CONNECT_dstdomain intra_net http_access allow pidgin_CONNECT_ports intra_net # Tachtler - AirDroid http_access allow airdroid_CONNECT_ports intra_net # Tachtler - Access part of local networks without authentication - http_access allow intra_net idmz_dst http_access allow intra_net edmz_dst # Tachtler - LDAP authentication - http_access allow localhost http_access allow idmz_net http_access allow edmz_net http_access allow intra_net noauthsites http_access allow intra_net ldap_auth # And finally deny all other access to this proxy http_access deny all # Squid normally listens to port 3128 http_port 3128 # Uncomment and adjust the following to add a disk cache directory. #cache_dir ufs /var/spool/squid 100 16 256 # Leave coredumps in the first cache dir coredump_dir /var/spool/squid # # Add any of your own refresh_pattern entries above these. # refresh_pattern ^ftp: 1440 20% 10080 refresh_pattern ^gopher: 1440 0% 1440 refresh_pattern -i (/cgi-bin/|\?) 0 0% 0 refresh_pattern . 0 20% 4320 # Tachtler - Microsoft Windows-Update # Tachtler - CAUTION - violates HTTP, but necessary! refresh_pattern -i microsoft.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windowsupdate.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windows.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims # Tachtler - Administrative parameter - # Tachtler - cache_mgr - default: root, presents the mail to user for e-mails from squid-cache cache_mgr squid # Tachtler - mail_from - presents the rcpt to user for emails from squid-cache mail_from squid-cache@tachtler.net # Tachtler - visible_hostname - hostname presented in error messages etc. visible_hostname proxy.idmz.tachtler.net # Tachtler - unique_hostname - hostname, that identifies this squid-cache unique_hostname proxy.idmz.tachtler.net # Tachtler - hostname_aliases - a list of hostnames, thas presented in the DNS for this squid-cache hostname_aliases server50.idmz.tachtler.net # Tachtler - Error page language and settings - # Tachtler - error_default_language error_default_language de-de # Tachtler - Logfile settings - # Tachtler - strip_query_terms - default: on - squid-cache strips query terms from requested URLs before logging. # This protects your users's privacy and reduces log size. # But you can disable this, to see the FULL URL used by squid-cache. strip_query_terms off # Tachtler - DNS-Query order - # Tachtler - dns_v4_first - default: off - controls the order of IPv6 and IPv4 DNS-Requests. dns_v4_first on
Erklärungen:
# Tachtler - DNS-Query order - # Tachtler - dns_v4_first - default: off - controls the order of IPv6 and IPv4 DNS-Requests. dns_v4_first on
Definiert die Reihenfolge der DNS-Abfragen, ob diese zuerst via IPv6 und dann via IPv4 erfolgen sollen oder andersherum.

Sonstige Konfigurationen
Nachfolgende Konfigurationen beschreiben verschiedene Konfigurationsmöglichkeiten des Squid Proxy-Server, die in keine bestimmte Kategorie hineinfallen.
Nachfolgende Ergänzungen sind in der Konfigurationsdatei
/etc/squid/squid.conf
im Squid Proxy-Server durchzuführen:
(Komplette Konfigurationsdatei)
# # Recommended minimum configuration: # # Tachtler - LDAP authentication - auth_param basic program /usr/lib64/squid/basic_ldap_auth -b "ou=People,dc=tachtler,dc=net" -f "uid=%s" -h ldap.idmz.tachtler.net -D "cn=Ersatzbenutzer,dc=tachtler,dc=net" -W /etc/squid/ldap_passwd auth_param basic utf8 on auth_param basic children 5 startup=1 idle=1 concurrency=0 auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein! auth_param basic credentialsttl 60 minutes auth_param basic casesensitive off # Example rule allowing access from your local networks. # Adapt to list your (internal) IP networks from where browsing # should be allowed # Tachtler - disabled default localnet configuration - # default: acl localnet src 10.0.0.0/8 # RFC1918 possible internal network # default: acl localnet src 172.16.0.0/12 # RFC1918 possible internal network # default: acl localnet src 192.168.0.0/16 # RFC1918 possible internal network acl idmz_net src 192.168.0.0/24 # idmz.tachtler.net acl edmz_net src 192.168.1.0/24 # edmz.tachtler.net acl intra_net src 192.168.2.0/24 # intra.tachtler.net acl edmz_dst dst 192.168.0.0/24 # edmz.tachtler.net destination acl idmz_dst dst 192.168.1.0/24 # idmz.tachtler.net destination acl intra_dst dst 192.168.2.0/24 # intra.tachtler.net destination # Tachtler - disabled IPv6 - # default: acl localnet src fc00::/7 # RFC 4193 local private network range # default: acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines acl SSL_ports port 443 # Tachtler - Safe_ports configuration - acl Safe_ports port 80 # http acl Safe_ports port 21 # ftp acl Safe_ports port 443 # https # default: acl Safe_ports port 70 # gopher # default: acl Safe_ports port 210 # wais acl Safe_ports port 1025-65535 # unregistered ports # default: acl Safe_ports port 280 # http-mgmt # default: acl Safe_ports port 488 # gss-http # default: acl Safe_ports port 591 # filemaker # default: acl Safe_ports port 777 # multiling http # Tachtler - CONNECT configuration - # Tachtler - Pidgin acl pidgin_CONNECT_ports port 5190 # Pidgin (proxy) acl pidgin_CONNECT_ports port 5222-5223 # Pidgin # Tachtler - AirDroid acl airdroid_CONNECT_ports port 8888-8890 # AirDroid # Tachtler - LDAP authentication - acl ldap_auth proxy_auth REQUIRED acl CONNECT method CONNECT # Tachtler - ACL follow_x_forwarded_for configuration - follow_x_forwarded_for allow localhost follow_x_forwarded_for allow idmz_net follow_x_forwarded_for allow intra_net # Tachtler - ACL dstdomain (Destination Domain) configuration - # Tachtler - Microsoft Windows-Update acl windowsupdate_CONNECT_dstdomain dstdomain www.update.microsoft.com acl windowsupdate_CONNECT_dstdomain dstdomain sls.micrsoft.com acl windowsupdate dstdomain .windowsupdate.microsoft.com acl windowsupdate dstdomain download.microsoft.com acl windowsupdate dstdomain .update.microsoft.com acl windowsupdate dstdomain .download.windowsupdate.com acl windowsupdate dstdomain dmd.metaservices.microsoft.com acl windowsupdate dstdomain redir.metaservices.microsoft.com acl windowsupdate dstdomain images.metaservices.microsoft.com acl windowsupdate dstdomain c.microsoft.com acl windowsupdate dstdomain wustat.windows.com acl windowsupdate dstdomain crl.microsoft.com acl windowsupdate dstdomain ctldl.windowsupdate.com acl windowsupdate dstdomain sls.microsoft.com acl windowsupdate dstdomain productactivation.one.microsoft.com acl windowsupdate dstdomain ntservicepack.microsoft.com acl windowsupdate dstdomain watson.microsoft.com acl windowsupdate dstdomain www.microsoft.com acl windowsupdate dstdomain www.msftncsi.com acl windowsupdate dstdomain spynet2.microsoft.com acl windowsupdate dstdomain sqm.telemetry.microsoft.com acl windowsupdate dstdomain iecvlist.microsoft.com acl windowsupdate dstdomain sqm.microsoft.com # Tachtler - Pidgin acl pidgin_CONNECT_dstdomain dstdomain proxy.eu.jabber.org acl pidgin_CONNECT_dstdomain dstdomain slogin.icq.com # Tachtler - ACL url-regex (URL regular expression) configuration - # Tachtler - Microsoft Windows Productactivation acl noauthsites url_regex productactivation\.one\.microsoft\.com:443 acl noauthsites url_regex activation\.sls\.microsoft\.com:443 # Tachtler - Microsoft Windows Online-Help acl noauthsites url_regex windowshelp\.microsoft\.com/* # Tachtler - Microsoft Internet Explorer Search-Engine-Updates acl noauthsites url_regex www\.iegallery\.com/de/* # # Recommended minimum Access Permission configuration: # # Deny requests to certain unsafe ports http_access deny !Safe_ports # Deny CONNECT to other than secure SSL ports # Tachtler # default: http_access deny CONNECT !SSL_ports http_access deny CONNECT !SSL_ports !pidgin_CONNECT_ports !airdroid_CONNECT_ports # Only allow cachemgr access from localhost http_access allow localhost manager http_access deny manager # We strongly recommend the following be uncommented to protect innocent # web applications running on the proxy server who think the only # one who can access services on "localhost" is a local user # Tachtler - enabled, deny access to localhost via squid proxy - # default: #http_access deny to_localhost http_access deny to_localhost # # INSERT YOUR OWN RULE(S) HERE TO ALLOW ACCESS FROM YOUR CLIENTS # # Example rule allowing access from your local networks. # Adapt localnet in the ACL section to list your (internal) IP networks # from where browsing should be allowed # Tachtler - access rules - # default: http_access allow localnet # default: http_access allow localhost # Tachtler - Microsoft Windows-Update http_access allow CONNECT windowsupdate_CONNECT_dstdomain intra_net http_access allow windowsupdate intra_net # Tachtler - Pidgin http_access allow CONNECT pidgin_CONNECT_dstdomain intra_net http_access allow pidgin_CONNECT_ports intra_net # Tachtler - AirDroid http_access allow airdroid_CONNECT_ports intra_net # Tachtler - Access part of local networks without authentication - http_access allow intra_net idmz_dst http_access allow intra_net edmz_dst # Tachtler - LDAP authentication - http_access allow localhost http_access allow idmz_net http_access allow edmz_net http_access allow intra_net noauthsites http_access allow intra_net ldap_auth # And finally deny all other access to this proxy http_access deny all # Squid normally listens to port 3128 http_port 3128 # Uncomment and adjust the following to add a disk cache directory. #cache_dir ufs /var/spool/squid 100 16 256 # Leave coredumps in the first cache dir coredump_dir /var/spool/squid # # Add any of your own refresh_pattern entries above these. # refresh_pattern ^ftp: 1440 20% 10080 refresh_pattern ^gopher: 1440 0% 1440 refresh_pattern -i (/cgi-bin/|\?) 0 0% 0 refresh_pattern . 0 20% 4320 # Tachtler - Microsoft Windows-Update # Tachtler - CAUTION - violates HTTP, but necessary! refresh_pattern -i microsoft.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windowsupdate.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windows.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims # Tachtler - Administrative parameter - # Tachtler - cache_mgr - default: root, presents the mail to user for e-mails from squid-cache cache_mgr squid # Tachtler - mail_from - presents the rcpt to user for emails from squid-cache mail_from squid-cache@tachtler.net # Tachtler - visible_hostname - hostname presented in error messages etc. visible_hostname proxy.idmz.tachtler.net # Tachtler - unique_hostname - hostname, that identifies this squid-cache unique_hostname proxy.idmz.tachtler.net # Tachtler - hostname_aliases - a list of hostnames, thas presented in the DNS for this squid-cache hostname_aliases server50.idmz.tachtler.net # Tachtler - Error page language and settings - # Tachtler - error_default_language error_default_language de-de # Tachtler - Logfile settings - # Tachtler - strip_query_terms - default: on - squid-cache strips query terms from requested URLs before logging. # This protects your users's privacy and reduces log size. # But you can disable this, to see the FULL URL used by squid-cache. strip_query_terms off # Tachtler - DNS-Query order - # Tachtler - dns_v4_first - default: off - controls the order of IPv6 and IPv4 DNS-Requests. dns_v4_first on # Tachtler - Miscellaneous Settings - # Tachtler - forwarded_for - default: on - controls, how squid-cache dealing with X-Forwarded-For Header. # forwarded_for on|off|transparent|truncate|delete forwarded_for delete
forwarded_for
Die Definition forwarded_for steuert, wie der Squid Proxy-Server beim Verlassen einer Anfrage mit den X-Forwarded-For - Headern umgehen soll
Nachfolgende Tabelle zeigt die Einstellungsmöglichkeiten für die Parameter der Definition
forwarded_for
| Definition | Wert | Beschreibung |
|---|---|---|
forwarded_for | on | Die IP-Adresse des Clients wird an den X-Forwarded-For Header angehängt |
forwarded_for | off | Es wird das Wort unknown an den X-Forwarded-For Header angehängt |
forwarded_for | transparent | Es wird keine Veränderung am X-Forwarded-For Header durchgeführt |
forwarded_for | truncate | Es wird der X-Forwarded-For Header gelöscht und nur die Client IP-Adresse gesetzt |
forwarded_for | delete | Es wird der X-Forwarded-For Header komplett entfernt |
# Tachtler - Miscellaneous Settings - # Tachtler - forwarded_for - default: on - controls, how squid-cache dealing with X-Forwarded-For Header. # forwarded_for on|off|transparent|truncate|delete forwarded_for delete
Definition, dass der komplette X-Forwarded-For - Header der Anfrage, beim verlassen des Squid Proxy-Server entfernt wird.
Bandbreitenbegrenzung-Konfiguration
Es gibt verschiedene Ausprägungen der Möglichkeit im Squid die Bandbreite der Verbindung zum Internet, zu begrenzen.

delay_pools !
Nachfolgendes Beispiel, soll die Möglichkeit zeigen, wie
- ein Benutzer, welcher sich am Squid authentifiziert hat (z.B. gegen LDAP)
- eine Benutzer bezogene Bandbreitenbeschränkung
eingerichtet werden kann.
Nachfolgende Ergänzungen sind in der Konfigurationsdatei
/etc/squid/squid.conf
notwendig, um die Delay Pool-Bandbreitenbeschränkungs Definitionen im Squid Proxy-Server einsetzen zu können:
(Komplette Konfigurationsdatei)
# # Recommended minimum configuration: # # Tachtler - LDAP authentication - auth_param basic program /usr/lib64/squid/basic_ldap_auth -b "ou=People,dc=tachtler,dc=net" -f "uid=%s" -h ldap.idmz.tachtler.net -D "cn=Ersatzbenutzer,dc=tachtler,dc=net" -W /etc/squid/ldap_passwd auth_param basic utf8 on auth_param basic children 5 startup=1 idle=1 concurrency=0 auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein! auth_param basic credentialsttl 60 minutes auth_param basic casesensitive off # Example rule allowing access from your local networks. # Adapt to list your (internal) IP networks from where browsing # should be allowed # Tachtler - disabled default localnet configuration - # default: acl localnet src 10.0.0.0/8 # RFC1918 possible internal network # default: acl localnet src 172.16.0.0/12 # RFC1918 possible internal network # default: acl localnet src 192.168.0.0/16 # RFC1918 possible internal network acl idmz_net src 192.168.0.0/24 # idmz.tachtler.net acl edmz_net src 192.168.1.0/24 # edmz.tachtler.net acl intra_net src 192.168.2.0/24 # intra.tachtler.net acl edmz_dst dst 192.168.0.0/24 # edmz.tachtler.net destination acl idmz_dst dst 192.168.1.0/24 # idmz.tachtler.net destination acl intra_dst dst 192.168.2.0/24 # intra.tachtler.net destination # Tachtler - disabled IPv6 - # default: acl localnet src fc00::/7 # RFC 4193 local private network range # default: acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines acl SSL_ports port 443 # Tachtler - Safe_ports configuration - acl Safe_ports port 80 # http acl Safe_ports port 21 # ftp acl Safe_ports port 443 # https # default: acl Safe_ports port 70 # gopher # default: acl Safe_ports port 210 # wais acl Safe_ports port 1025-65535 # unregistered ports # default: acl Safe_ports port 280 # http-mgmt # default: acl Safe_ports port 488 # gss-http # default: acl Safe_ports port 591 # filemaker # default: acl Safe_ports port 777 # multiling http # Tachtler - CONNECT configuration - # Tachtler - Pidgin acl pidgin_CONNECT_ports port 5190 # Pidgin (proxy) acl pidgin_CONNECT_ports port 5222-5223 # Pidgin # Tachtler - AirDroid acl airdroid_CONNECT_ports port 8888-8890 # AirDroid # Tachtler - Delay-Pool configuration - acl delay_pool_klaus proxy_auth klaus # Tachtler - LDAP authentication - acl ldap_auth proxy_auth REQUIRED acl CONNECT method CONNECT # Tachtler - ACL follow_x_forwarded_for configuration - follow_x_forwarded_for allow localhost follow_x_forwarded_for allow idmz_net follow_x_forwarded_for allow intra_net # Tachtler - ACL dstdomain (Destination Domain) configuration - # Tachtler - Microsoft Windows-Update acl windowsupdate_CONNECT_dstdomain dstdomain www.update.microsoft.com acl windowsupdate_CONNECT_dstdomain dstdomain sls.micrsoft.com acl windowsupdate dstdomain .windowsupdate.microsoft.com acl windowsupdate dstdomain download.microsoft.com acl windowsupdate dstdomain .update.microsoft.com acl windowsupdate dstdomain .download.windowsupdate.com acl windowsupdate dstdomain dmd.metaservices.microsoft.com acl windowsupdate dstdomain redir.metaservices.microsoft.com acl windowsupdate dstdomain images.metaservices.microsoft.com acl windowsupdate dstdomain c.microsoft.com acl windowsupdate dstdomain wustat.windows.com acl windowsupdate dstdomain crl.microsoft.com acl windowsupdate dstdomain ctldl.windowsupdate.com acl windowsupdate dstdomain sls.microsoft.com acl windowsupdate dstdomain productactivation.one.microsoft.com acl windowsupdate dstdomain ntservicepack.microsoft.com acl windowsupdate dstdomain watson.microsoft.com acl windowsupdate dstdomain www.microsoft.com acl windowsupdate dstdomain www.msftncsi.com acl windowsupdate dstdomain spynet2.microsoft.com acl windowsupdate dstdomain sqm.telemetry.microsoft.com acl windowsupdate dstdomain iecvlist.microsoft.com acl windowsupdate dstdomain sqm.microsoft.com # Tachtler - Pidgin acl pidgin_CONNECT_dstdomain dstdomain proxy.eu.jabber.org acl pidgin_CONNECT_dstdomain dstdomain slogin.icq.com # Tachtler - ACL url-regex (URL regular expression) configuration - # Tachtler - Microsoft Windows Productactivation acl noauthsites url_regex productactivation\.one\.microsoft\.com:443 acl noauthsites url_regex activation\.sls\.microsoft\.com:443 # Tachtler - Microsoft Windows Online-Help acl noauthsites url_regex windowshelp\.microsoft\.com/* # Tachtler - Microsoft Internet Explorer Search-Engine-Updates acl noauthsites url_regex www\.iegallery\.com/de/* # # Recommended minimum Access Permission configuration: # # Deny requests to certain unsafe ports http_access deny !Safe_ports # Deny CONNECT to other than secure SSL ports # Tachtler # default: http_access deny CONNECT !SSL_ports http_access deny CONNECT !SSL_ports !pidgin_CONNECT_ports !airdroid_CONNECT_ports # Only allow cachemgr access from localhost http_access allow localhost manager http_access deny manager # We strongly recommend the following be uncommented to protect innocent # web applications running on the proxy server who think the only # one who can access services on "localhost" is a local user # Tachtler - enabled, deny access to localhost via squid proxy - # default: #http_access deny to_localhost http_access deny to_localhost # # INSERT YOUR OWN RULE(S) HERE TO ALLOW ACCESS FROM YOUR CLIENTS # # Example rule allowing access from your local networks. # Adapt localnet in the ACL section to list your (internal) IP networks # from where browsing should be allowed # Tachtler - access rules - # default: http_access allow localnet # default: http_access allow localhost # Tachtler - Microsoft Windows-Update http_access allow CONNECT windowsupdate_CONNECT_dstdomain intra_net http_access allow windowsupdate intra_net # Tachtler - Pidgin http_access allow CONNECT pidgin_CONNECT_dstdomain intra_net http_access allow pidgin_CONNECT_ports intra_net # Tachtler - AirDroid http_access allow airdroid_CONNECT_ports intra_net # Tachtler - Access part of local networks without authentication - http_access allow intra_net idmz_dst http_access allow intra_net edmz_dst # Tachtler - LDAP authentication - http_access allow localhost http_access allow idmz_net http_access allow edmz_net http_access allow intra_net noauthsites http_access allow intra_net ldap_auth # And finally deny all other access to this proxy http_access deny all # Squid normally listens to port 3128 http_port 3128 # Uncomment and adjust the following to add a disk cache directory. #cache_dir ufs /var/spool/squid 100 16 256 # Leave coredumps in the first cache dir coredump_dir /var/spool/squid # # Add any of your own refresh_pattern entries above these. # refresh_pattern ^ftp: 1440 20% 10080 refresh_pattern ^gopher: 1440 0% 1440 refresh_pattern -i (/cgi-bin/|\?) 0 0% 0 refresh_pattern . 0 20% 4320 # Tachtler - Microsoft Windows-Update # Tachtler - CAUTION - violates HTTP, but necessary! refresh_pattern -i microsoft.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windowsupdate.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windows.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims # Tachtler - Administrative parameter - # Tachtler - cache_mgr - default: root, presents the mail to user for e-mails from squid-cache cache_mgr squid # Tachtler - mail_from - presents the rcpt to user for emails from squid-cache mail_from squid-cache@tachtler.net # Tachtler - visible_hostname - hostname presented in error messages etc. visible_hostname proxy.idmz.tachtler.net # Tachtler - unique_hostname - hostname, that identifies this squid-cache unique_hostname proxy.idmz.tachtler.net # Tachtler - hostname_aliases - a list of hostnames, thas presented in the DNS for this squid-cache hostname_aliases server50.idmz.tachtler.net # Tachtler - Error page language and settings - # Tachtler - error_default_language error_default_language de-de # Tachtler - Logfile settings - # Tachtler - strip_query_terms - default: on - squid-cache strips query terms from requested URLs before logging. # This protects your users's privacy and reduces log size. # But you can disable this, to see the FULL URL used by squid-cache. strip_query_terms off # Tachtler - DNS-Query order - # Tachtler - dns_v4_first - default: off - controls the order of IPv6 and IPv4 DNS-Requests. dns_v4_first on # Tachtler - Miscellaneous Settings - # Tachtler - forwarded_for - default: on - controls, how squid-cache dealing with X-Forwarded-For Header. # forwarded_for on|off|transparent|truncate|delete forwarded_for delete # Tachtler - Cache Manager configuration - cachemgr_passwd disable shutdown offline_toggle cachemgr_passwd bekannt info cachemgr_passwd geheim all # Tachtler - Delay pool configuration - # Tachtler - delay_pools - default: 0 - number of delay pools, best practice is, one per user. delay_pools 1 # Tachtler - delay_class - default: none - it MUST be one for each delay_pool. delay_class 1 1 # Tachtler - delay_access - default: none - access control, best practise, only allow the specific user on his own delay pool. delay_access 1 allow delay_pool_klaus delay_access 1 deny all # Tachtler - delay_parameters - default: none - control the restore/maximum byte per download for the specific delay pool. # 64k = 8000/8000 delay_parameters 1 8000/8000
Nachfolgend sollen die einzelnen Zeilen und deren Bedeutung dargestellt werden
# Tachtler - Delay-Pool configuration -
acl delay_pool_klaus proxy_auth klaus
Erstellung einer ACL mit dem Inhalt des Benutzernamens, mit dem sich der Benutzer authentifiziert hat:
acl delay_pool_klaus proxy_auth klaus
# Tachtler - Delay pool configuration - # Tachtler - delay_pools - default: 0 - number of delay pools, best practice is, one per user. delay_pools 1 # Tachtler - delay_class - default: none - it MUST be one for each delay_pool. delay_class 1 1 # Tachtler - delay_access - default: none - access control, best practise, only allow the specific user on his own delay pool. delay_access 1 allow delay_pool_klaus delay_access 1 deny all # Tachtler - delay_parameters - default: none - control the restore/maximum byte per download for the specific delay pool. # 64k = 8000/8000 delay_parameters 1 8000/8000
Angabe, wie viele delay_pools eingerichtet und von Squid verwaltet werden sollen:
delay_pools 1
Angabe welcher delay_pool von welchem Klasse-Typ (class) sein soll:
delay_class 1 1
* Hier ist delay_pool 1 vom Klassen-Typ delay_class 1 !!!

| Klassen-Typ | Erklärung |
|---|---|
| class 1 | Alles ist nur in einem gesamten Klassen-Container limitiert |
| class 2 | Alles ist jeweils in einem Klassen-Container limitiert, welche zusätzlich anhand der IP-Adressen Bits 25 bis 32 (d) einer IPv4-Adresse unterschieden werden (a.b.c.d) |
| class 3 | Alles ist jeweils in einem Klassen-Container limitiert, welche jedoch in „Netzwerke“ anhand der Bits 17 bis 24 © unterschieden werden und zusätzlich auch noch anhand der IP-Adressen Bits 25 bis 32 (d) einer IPv4-Adresse unterschieden werden (a.b.c.d) |
| class 4 | Genau wie class 3, jedoch mit einem zusätzlichen Limit basierend auf einer Benutzerkennung, was nur im Zusammenhang mit einer Authentifizierung angewandt werden kann |
| class 5 | Anfragen, welche gruppiert mit einem „tag“ versehen, in einer „externen ACL„ hinterlegt sind |
Angabe unter welchen Umständen der delay_pool 1 zum tragen kommt bzw. welche „ACL„ auf diesen delay_pool Anwendung findet und vor allem auch welche nicht!:
delay_access 1 allow delay_pool_klaus delay_access 1 deny all
Angabe der Bandbreitenbeschränkung für den delay_pool 1:
delay_parameters 1 8000/8000

| Parameter | Erklärung |
|---|---|
| 1 | delay_pool (Nummer) |
| 8000/8000 | „restore“/„maximum“ |

- „restore“ in Byte, bezeichnet nach wie vielen Byte pro Zeiteinheit (1 Sekunde), der Angeforderte (Download, URL usw.) - auf die Byte Angabe, hier 8000, begrenzt wird = 8k pro Sekunde.
- „maximum“ in Byte, bezeichnet nach wie vielen Byte - ohne Zeitbeschränkung, der Angeforderte (Download, URL usw.) - auf die Byte Angabe, hier 8000, begrenzt wird = 8k pro Anfrage.
Cache Manager Interface
Squid Proxy-Server liefert ein recht einfach zu bedienendes und sehr aussagekräftiges Webinterface mit, das Cache Manager Interface (CMI). Das CMI ist ein CGI (Common Gateway Interface). Dieses CGI kann grundsätzlich auf einen beliebigen Webserver installiert werden.
Voraussetzung: Der Webserver unterstützt CGI-Funktionalität und es besteht eine Netzverbindung zum Squid Proxy-Server.
Nachfolgend soll der Apache HTTP Webserver dazu genutzt werden, um das Webinterface aufrufbar zu machen.
Apache VHOST-Konfiguration
Es soll anstelle der mitgelieferten Konfigurationsdatei in nachfolgendem Verzeichnis, mit nachfolgendem Namen:
/etc/httpd/conf.d/squid.conf
ein virtueller Host im Apache HTTP Server eingerichtet werden.
Siehe dazu auch nachfolgende interne Links:
Dazu soll zuerst die mitgelieferte Konfigurationsdatei mit nachfolgendem Befehl kopiert werden:
# cp -a /etc/httpd/conf.d/squid.conf /etc/httpd/conf.d/squid.conf.orig
Zur Vorbereitung auf spätere Erweiterungen des virtuellen Hosts, sollte mit nachfolgendem Befehl ein neues Verzeichnis angelegt werden:
# mkdir /usr/share/squid/html
Anschließend kann dann der Inhalt der Konfigurationsdatei /etc/httpd/conf.d/squid.conf wie nachfolgend dargestellt entsprechend abgeändert werden:
(Komplette Konfigurationsdatei)
# # squid.tachtler.net (Squid Cache Manager Interface) # <VirtualHost *:80> ServerAdmin webmaster@tachtler.net ServerName squid.tachtler.net ServerAlias www.squid.tachtler.net ServerPath / ScriptAlias /Squid/cgi-bin/cachemgr.cgi /usr/lib64/squid/cachemgr.cgi Alias /icons /usr/share/squid/icons DocumentRoot "/usr/share/squid/html" <Directory "/usr/share/squid/html"> Options -Indexes +FollowSymLinks # Tachtler (enable for .htaccess file support) # AllowOverride AuthConfig AllowOverride None # Tachtler (enable for unlimited access) Require all granted </Directory> <Location /Squid/cgi-bin/cachemgr.cgi> Options -Indexes +FollowSymLinks # Tachtler (enable for .htaccess file support) # AllowOverride AuthConfig AllowOverride None # Tachtler (enable for unlimited access) Require all granted </Location> <Location /icons> Options -Indexes +FollowSymLinks # Tachtler (enable for .htaccess file support) # AllowOverride AuthConfig AllowOverride None # Tachtler (enable for unlimited access) Require all granted </Location> DirectoryIndex /Squid/cgi-bin/cachemgr.cgi ErrorLog logs/squid_error.log SetEnvIf X-Forwarded-For "^.*\..*\..*\..*" forwarded CustomLog logs/squid_access.log combined env=!forwarded CustomLog logs/squid_access.log combined_proxypass env=forwarded </VirtualHost>

Cache Manager Interface Passwörter
Nachfolgend können verschiedene Passwörter, je nach Rechte bzw. Funktionen, vergeben werden. In diesem Beispiel zeigt nachfolgende Tabelle die Einrichtung der Passwörter für gewisse Funktionen und den kompletten Zugriff auf das Cache Manager Interface (CMI) des Squid Proxy-Servers:
| Cache Manager Passwort Definition | Bedeutung |
|---|---|
| cachemgr_passwd disable shutdown offline_toggle | Die Funktion shutdown wird abgeschaltet |
| cachemgr_passwd bekannt info | Die Funktion info erhält das Passwort bekannt |
| cachemgr_passwd geheim all | Unbegrenzten Zugriff gewährt das Passwort geheim |
Nachfolgende Ergänzungen sind in der Konfigurationsdatei
/etc/squid/squid.conf
notwendig, um die Cache Manager-Passwörter Definitionen im Squid Proxy-Server einsetzen zu können:
(Komplette Konfigurationsdatei)
# # Recommended minimum configuration: # # Tachtler - LDAP authentication - auth_param basic program /usr/lib64/squid/basic_ldap_auth -b "ou=People,dc=tachtler,dc=net" -f "uid=%s" -h ldap.idmz.tachtler.net -D "cn=Ersatzbenutzer,dc=tachtler,dc=net" -W /etc/squid/ldap_passwd auth_param basic utf8 on auth_param basic children 5 startup=1 idle=1 concurrency=0 auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein! auth_param basic credentialsttl 60 minutes auth_param basic casesensitive off # Example rule allowing access from your local networks. # Adapt to list your (internal) IP networks from where browsing # should be allowed # Tachtler - disabled default localnet configuration - # default: acl localnet src 10.0.0.0/8 # RFC1918 possible internal network # default: acl localnet src 172.16.0.0/12 # RFC1918 possible internal network # default: acl localnet src 192.168.0.0/16 # RFC1918 possible internal network acl idmz_net src 192.168.0.0/24 # idmz.tachtler.net acl edmz_net src 192.168.1.0/24 # edmz.tachtler.net acl intra_net src 192.168.2.0/24 # intra.tachtler.net acl edmz_dst dst 192.168.0.0/24 # edmz.tachtler.net destination acl idmz_dst dst 192.168.1.0/24 # idmz.tachtler.net destination acl intra_dst dst 192.168.2.0/24 # intra.tachtler.net destination # Tachtler - disabled IPv6 - # default: acl localnet src fc00::/7 # RFC 4193 local private network range # default: acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines acl SSL_ports port 443 # Tachtler - Safe_ports configuration - acl Safe_ports port 80 # http acl Safe_ports port 21 # ftp acl Safe_ports port 443 # https # default: acl Safe_ports port 70 # gopher # default: acl Safe_ports port 210 # wais acl Safe_ports port 1025-65535 # unregistered ports # default: acl Safe_ports port 280 # http-mgmt # default: acl Safe_ports port 488 # gss-http # default: acl Safe_ports port 591 # filemaker # default: acl Safe_ports port 777 # multiling http # Tachtler - CONNECT configuration - # Tachtler - Pidgin acl pidgin_CONNECT_ports port 5190 # Pidgin (proxy) acl pidgin_CONNECT_ports port 5222-5223 # Pidgin # Tachtler - AirDroid acl airdroid_CONNECT_ports port 8888-8890 # AirDroid # Tachtler - LDAP authentication - acl ldap_auth proxy_auth REQUIRED acl CONNECT method CONNECT # Tachtler - ACL follow_x_forwarded_for configuration - follow_x_forwarded_for allow localhost follow_x_forwarded_for allow idmz_net follow_x_forwarded_for allow intra_net # Tachtler - ACL dstdomain (Destination Domain) configuration - # Tachtler - Microsoft Windows-Update acl windowsupdate_CONNECT_dstdomain dstdomain www.update.microsoft.com acl windowsupdate_CONNECT_dstdomain dstdomain sls.micrsoft.com acl windowsupdate dstdomain .windowsupdate.microsoft.com acl windowsupdate dstdomain download.microsoft.com acl windowsupdate dstdomain .update.microsoft.com acl windowsupdate dstdomain .download.windowsupdate.com acl windowsupdate dstdomain dmd.metaservices.microsoft.com acl windowsupdate dstdomain redir.metaservices.microsoft.com acl windowsupdate dstdomain images.metaservices.microsoft.com acl windowsupdate dstdomain c.microsoft.com acl windowsupdate dstdomain wustat.windows.com acl windowsupdate dstdomain crl.microsoft.com acl windowsupdate dstdomain ctldl.windowsupdate.com acl windowsupdate dstdomain sls.microsoft.com acl windowsupdate dstdomain productactivation.one.microsoft.com acl windowsupdate dstdomain ntservicepack.microsoft.com acl windowsupdate dstdomain watson.microsoft.com acl windowsupdate dstdomain www.microsoft.com acl windowsupdate dstdomain www.msftncsi.com acl windowsupdate dstdomain spynet2.microsoft.com acl windowsupdate dstdomain sqm.telemetry.microsoft.com acl windowsupdate dstdomain iecvlist.microsoft.com acl windowsupdate dstdomain sqm.microsoft.com # Tachtler - Pidgin acl pidgin_CONNECT_dstdomain dstdomain proxy.eu.jabber.org acl pidgin_CONNECT_dstdomain dstdomain slogin.icq.com # Tachtler - ACL url-regex (URL regular expression) configuration - # Tachtler - Microsoft Windows Productactivation acl noauthsites url_regex productactivation\.one\.microsoft\.com:443 acl noauthsites url_regex activation\.sls\.microsoft\.com:443 # Tachtler - Microsoft Windows Online-Help acl noauthsites url_regex windowshelp\.microsoft\.com/* # Tachtler - Microsoft Internet Explorer Search-Engine-Updates acl noauthsites url_regex www\.iegallery\.com/de/* # # Recommended minimum Access Permission configuration: # # Deny requests to certain unsafe ports http_access deny !Safe_ports # Deny CONNECT to other than secure SSL ports # Tachtler # default: http_access deny CONNECT !SSL_ports http_access deny CONNECT !SSL_ports !pidgin_CONNECT_ports !airdroid_CONNECT_ports # Only allow cachemgr access from localhost http_access allow localhost manager http_access deny manager # We strongly recommend the following be uncommented to protect innocent # web applications running on the proxy server who think the only # one who can access services on "localhost" is a local user # Tachtler - enabled, deny access to localhost via squid proxy - # default: #http_access deny to_localhost http_access deny to_localhost # # INSERT YOUR OWN RULE(S) HERE TO ALLOW ACCESS FROM YOUR CLIENTS # # Example rule allowing access from your local networks. # Adapt localnet in the ACL section to list your (internal) IP networks # from where browsing should be allowed # Tachtler - access rules - # default: http_access allow localnet # default: http_access allow localhost # Tachtler - Microsoft Windows-Update http_access allow CONNECT windowsupdate_CONNECT_dstdomain intra_net http_access allow windowsupdate intra_net # Tachtler - Pidgin http_access allow CONNECT pidgin_CONNECT_dstdomain intra_net http_access allow pidgin_CONNECT_ports intra_net # Tachtler - AirDroid http_access allow airdroid_CONNECT_ports intra_net # Tachtler - Access part of local networks without authentication - http_access allow intra_net idmz_dst http_access allow intra_net edmz_dst # Tachtler - LDAP authentication - http_access allow localhost http_access allow idmz_net http_access allow edmz_net http_access allow intra_net noauthsites http_access allow intra_net ldap_auth # And finally deny all other access to this proxy http_access deny all # Squid normally listens to port 3128 http_port 3128 # Uncomment and adjust the following to add a disk cache directory. #cache_dir ufs /var/spool/squid 100 16 256 # Leave coredumps in the first cache dir coredump_dir /var/spool/squid # # Add any of your own refresh_pattern entries above these. # refresh_pattern ^ftp: 1440 20% 10080 refresh_pattern ^gopher: 1440 0% 1440 refresh_pattern -i (/cgi-bin/|\?) 0 0% 0 refresh_pattern . 0 20% 4320 # Tachtler - Microsoft Windows-Update # Tachtler - CAUTION - violates HTTP, but necessary! refresh_pattern -i microsoft.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windowsupdate.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windows.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims # Tachtler - Administrative parameter - # Tachtler - cache_mgr - default: root, presents the mail to user for e-mails from squid-cache cache_mgr squid # Tachtler - mail_from - presents the rcpt to user for emails from squid-cache mail_from squid-cache@tachtler.net # Tachtler - visible_hostname - hostname presented in error messages etc. visible_hostname proxy.idmz.tachtler.net # Tachtler - unique_hostname - hostname, that identifies this squid-cache unique_hostname proxy.idmz.tachtler.net # Tachtler - hostname_aliases - a list of hostnames, thas presented in the DNS for this squid-cache hostname_aliases server50.idmz.tachtler.net # Tachtler - Error page language and settings - # Tachtler - error_default_language error_default_language de-de # Tachtler - Logfile settings - # Tachtler - strip_query_terms - default: on - squid-cache strips query terms from requested URLs before logging. # This protects your users's privacy and reduces log size. # But you can disable this, to see the FULL URL used by squid-cache. strip_query_terms off # Tachtler - DNS-Query order - # Tachtler - dns_v4_first - default: off - controls the order of IPv6 and IPv4 DNS-Requests. dns_v4_first on # Tachtler - Miscellaneous Settings - # Tachtler - forwarded_for - default: on - controls, how squid-cache dealing with X-Forwarded-For Header. # forwarded_for on|off|transparent|truncate|delete forwarded_for delete # Tachtler - Cache Manager configuration - cachemgr_passwd disable shutdown offline_toggle cachemgr_passwd bekannt info cachemgr_passwd geheim all

Erklärung:
# Tachtler - Cache Manager configuration - cachemgr_passwd disable shutdown offline_toggle cachemgr_passwd bekannt info cachemgr_passwd geheim all
Es werden drei verschiedene Passwörter-Konfigurationen durchgeführt, wie in oben gezeigter Tabelle dargestellt.
HTTPS - ssl_bump-Konfiguration
Der Einsatz eines Squid Proxy-Servers als „man-in-the-middle“ Entschlüsselungs- und Verschlüsselungs-Proxy einer direkten oder transparent umgeleiteten HTTPS-Verbindung, kann durch den Einsatz einer eigenen CA umgesetzt werden.
Durch den Einsatz des Squid Proxy-Servers im Modus „man-in-the-middle“ als Entschlüsselungs- und Verschlüsselungs-Proxy, kann der Datenverkehr analysiert und geblockt werden, oder die entsprechenden ACL's zur Anwendung kommen und die Verwendung von Funktionen wie ICAP und eCAP können ebenfalls genutzt werden.


| Beschreibung | Externer Link |
|---|---|
| Homepage | http://www.squid-cache.org/ |
| Feature ssl_bump | http://wiki.squid-cache.org/Features/SslBump |
| Feature DynamicSslCert | http://wiki.squid-cache.org/Features/DynamicSslCert |
| Feature MimicSslServerCert | http://wiki.squid-cache.org/Features/MimicSslServerCert |
Nachfolgende Skizze beschreibt vereinfacht die Funktionsweise des Squid Proxy-Servers mit ssl_bump-Konfiguration:
+--------------------------+ +----------------------------------------------+ +---------+ | | | squid-cache | | Browser | | | | | | | | | | 1. squid nimmt Anfrage vom Browser entgegen | <-1-- | Anfrage | | https://www.tachtler.net | <-2-- | 2. squid holt das Zertifikat vom Ziel-Server | | | | https://www.tachtler.net | --3-> | 3. squid bekommt das Ziel-Server Zertifikat | | | | | | | | | | | | !. squid erstellt ein EIGENES ZERTIFIKAT mit | | | | | | den Daten aus dem geholten Zertifikat vom | | | | | | Ziel-Server unter Zuhilfenahme seiner ei- | | | | | | genen Root-CA | | | | | | | | | | | | 4. squid gibt Anfrage an den Browser zurück | --4-> | Antwort | | | | | | | +--------------------------+ +----------------------------------------------+ +---------+
Root-CA erstellen
Damit der Squid Proxy-Server als „man-in-the-middle“ Entschlüsselungs- und Verschlüsselungs-Proxy einer direkten oder transparent umgeleiteten HTTPS-Verbindung agieren kann, muss eine eigenen CA erstellt werden, falls nicht schon eine eigene CA vorhanden ist.
Nachfolgende Befehle erstellen eine eigene CA zur Verwendung mit dem Squid Proxy-Server.
Nachfolgender Befehl erstellt zuerst zwei neue Verzeichnisse unterhalb des Verzeichnisses
/etc/pki
mit den Namen
/etc/pki/squid/certs/etc/pki/squid/private
# mkdir -p /etc/pki/squid/{certs,private}
Anschließend werden mit nachfolgenden Befehlen die Besitzrechte
# chown -R squid:squid /etc/pki/squid/{certs,private}
und die Dateirechte
# chmod -R 700 /etc/pki/squid/{certs,private}
entsprechend gesetzt.
Anschließend kann nun mit nachfolgendem Befehl
- ein Schlüssel (Key)
- ein Root-Zertifikat (Root-CA)
in den entsprechenden Verzeichnissen, mit bestimmten Ausprägungen erstellt werden:
# openssl req -new -newkey rsa:2048 -sha256 -days 3652 -nodes -x509 -keyout /etc/pki/squid/private/squidCA.key -out /etc/pki/squid/certs/squidCA.crt Generating a 2048 bit RSA private key ..................+++ .................+++ writing new private key to '/etc/pki/squid/private/squidCA.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:DE State or Province Name (full name) []:Bavaria (Bayern) Locality Name (eg, city) [Default City]:Munich (Muenchen) Organization Name (eg, company) [Default Company Ltd]:Klaus Tachtler Organizational Unit Name (eg, section) []:. Common Name (eg, your name or your server's hostname) []:www.tachtler.net Email Address []:hostmaster@tachtler.net
Erklärungen:
Es wird eine Schlüssel vom Typ rsa in der Länge von 2048 Byte verwendet, was aktuell den meisten Zertifikaten entspricht:
rsa:2048
Es kommt der Verschlüsselungsalgorithmus sha256 zum Einsatz, was ebenfalls aktuell den meisten Zertifikaten entspricht:
-sha256
Es wurde eine Laufzeit von ca. 10 Jahren gewählt, meist die Unterstützung für Betriebssysteme im „Long term support“ im „Enterprise“ Segment, wie z.B. bei CentOS.
-days 3652
Nachfolgend sind die Zertifikatsinformationen, wie
- Land:
DE - Bundesland:
Bavaria (Bayern) - Name der Organisation:
Klaus Tachtler - Weitere Organisationsbezeichnung (Abteilung usw.):
.- (Punkt bedeutet keine Angabe!) - Name des Zertifikats, Hostname:
www.tachtler.net - E-Mail-Adresse des Ansprachpartners:
hostmaster@tachtler.net
genannt:
Country Name (2 letter code) [XX]:DE State or Province Name (full name) []:Bavaria (Bayern) Locality Name (eg, city) [Default City]:Munich (Muenchen) Organization Name (eg, company) [Default Company Ltd]:Klaus Tachtler Organizational Unit Name (eg, section) []:. Common Name (eg, your name or your server's hostname) []:www.tachtler.net Email Address []:hostmaster@tachtler.net
Anschließend werden mit nachfolgenden Befehlen die Besitzrechte
# chown -R squid:squid /etc/pki/squid/{certs,private}/squidCA.*
und die Dateirechte
# chmod -R 400 /etc/pki/squid/{certs,private}/squidCA.*
für die Dateien entsprechend gesetzt.
Abschließend kann mit nachfolgendem Befehl überprüft werden, ob die Dateien richtig erstellt wurden, was eine Ausgabe, wie die nachfolgend gezeigte, zum Vorschein bringen sollte:
# ls -l /etc/pki/squid/* /etc/pki/squid/certs: total 4 -r-------- 1 squid squid 1476 Mar 5 09:30 squidCA.crt /etc/pki/squid/private: total 4 -r-------- 1 squid squid 1704 Mar 5 09:30 squidCA.key
Eine Überprüfung, ob das Zertifikat korrekt erstellt wurde, kann mit nachfolgendem Befehl durchgeführt werden:
# openssl x509 -noout -text -in /etc/pki/squid/certs/squidCA.crt
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 18351035949067543440 (0xfeabf9f7bc982390)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=DE, ST=Bavaria (Bayern), L=Munich (Muenchen), O=Klaus Tachtler, CN=www.tachtler.net/emailAddress=hostmaster@tachtler.net
Validity
Not Before: Mar 5 08:30:27 2015 GMT
Not After : Mar 4 08:30:27 2025 GMT
Subject: C=DE, ST=Bavaria (Bayern), L=Munich (Muenchen), O=Klaus Tachtler, CN=www.tachtler.net/emailAddress=hostmaster@tachtler.net
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:d2:73:76:c0:a6:c1:3a:d0:e6:9e:9a:62:6d:56:
a6:b0:99:22:dd:30:47:c6:dc:e7:2d:d6:8e:e2:15:
a6:09:10:35:73:97:88:29:e6:95:03:2a:8c:78:48:
22:4b:fc:ac:c6:8f:2c:20:cc:06:0b:f8:72:9d:e2:
b5:ff:37:52:27:63:f1:7f:04:c2:22:74:1f:16:fc:
f9:6d:95:67:cd:7b:c3:4e:5f:25:d4:6f:3c:d9:3e:
11:9a:c6:15:96:ed:7d:3c:76:aa:2f:93:f6:bc:fa:
4c:74:5d:25:98:99:61:ad:2a:8b:bd:b3:92:97:68:
eb:fa:e4:58:e9:33:36:93:3c:ed:ad:28:24:55:26:
68:b8:6c:e8:b8:c6:63:57:af:9a:c9:1c:96:99:7f:
2f:ec:ed:b3:e3:8a:01:5a:d5:b4:48:36:ec:55:12:
79:97:d5:93:28:df:3b:86:a1:0f:16:0d:c9:d0:4d:
58:8a:ea:a9:15:76:20:49:5a:07:41:01:4b:cb:0e:
a0:74:01:68:38:e5:07:a9:9e:a7:fe:ae:de:01:35:
36:43:2d:6d:4b:56:d4:be:4e:47:3e:a6:13:c7:f3:
f1:77:0b:37:1a:78:32:63:b9:14:b9:2a:69:80:ad:
59:28:ad:56:2c:4f:1d:5a:7c:fa:af:b0:dc:a1:25:
8b:5a
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
14:08:11:A4:ED:02:27:70:64:0C:18:4D:20:BE:04:DC:D7:A3:8E:58
X509v3 Authority Key Identifier:
keyid:14:08:11:A4:ED:02:27:70:64:0C:18:4D:20:BE:04:DC:D7:A3:8E:58
X509v3 Basic Constraints:
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
4a:9b:21:79:97:74:7a:e2:a0:84:32:af:aa:6d:c8:eb:81:7d:
ea:1d:94:c8:c8:39:f3:3e:13:aa:f6:a3:05:9e:17:10:85:24:
f8:cd:e7:3f:d3:bb:e2:51:b7:ad:21:75:50:48:fb:ca:8b:da:
a0:78:59:df:57:82:86:54:ba:d2:ba:f1:b4:ab:ce:75:db:62:
21:25:fb:74:74:cd:ae:50:ec:27:f6:5f:b6:65:9a:ce:ed:cc:
ee:da:ca:0b:02:a1:bc:49:e9:96:68:37:6a:8e:6b:c9:b5:ec:
a9:99:1e:bc:99:65:c4:c5:95:78:a6:54:bf:88:d1:f4:65:9e:
02:c0:54:50:50:77:d5:3d:f0:6b:87:e1:de:68:37:fa:bb:46:
fa:f2:a3:e4:23:d7:5b:f3:26:20:9e:2b:d1:a1:7f:38:05:e3:
05:66:ed:3a:21:60:e0:8d:5b:ca:4d:f1:3e:61:dd:96:c4:dd:
c4:8e:71:c8:58:cd:f7:d1:4c:71:20:78:8d:06:83:c7:4a:ff:
24:4c:22:b4:0a:aa:3b:32:a3:6f:bb:8e:15:8b:56:10:70:04:
1d:cf:b5:01:b2:94:d4:76:c8:ca:05:18:10:72:a3:5b:4c:84:
be:b9:c6:e0:4b:e1:8a:83:ca:1d:8c:16:a7:94:34:4d:95:be:
45:e2:59:7b
ssl_bump-Konfiguration
Die Konfigurationen ergänzen die bisherige Konfiguration beim Parameter
http_port 3128
Nachfolgende Ergänzungen sind in der Konfigurationsdatei
/etc/squid/squid.conf
notwendig, um die ssl_bump-Konifgurations Definitionen im Squid Proxy-Server einsetzen zu können:
(Komplette Konfigurationsdatei)
# # Recommended minimum configuration: # # Tachtler - LDAP authentication - auth_param basic program /usr/lib64/squid/basic_ldap_auth -b "ou=People,dc=tachtler,dc=net" -f "uid=%s" -h ldap.idmz.tachtler.net -D "cn=Ersatzbenutzer,dc=tachtler,dc=net" -W /etc/squid/ldap_passwd auth_param basic utf8 on auth_param basic children 5 startup=1 idle=1 concurrency=0 auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein! auth_param basic credentialsttl 60 minutes auth_param basic casesensitive off # Example rule allowing access from your local networks. # Adapt to list your (internal) IP networks from where browsing # should be allowed # Tachtler - disabled default localnet configuration - # default: acl localnet src 10.0.0.0/8 # RFC1918 possible internal network # default: acl localnet src 172.16.0.0/12 # RFC1918 possible internal network # default: acl localnet src 192.168.0.0/16 # RFC1918 possible internal network acl idmz_net src 192.168.0.0/24 # idmz.tachtler.net acl edmz_net src 192.168.1.0/24 # edmz.tachtler.net acl intra_net src 192.168.2.0/24 # intra.tachtler.net acl edmz_dst dst 192.168.0.0/24 # edmz.tachtler.net destination acl idmz_dst dst 192.168.1.0/24 # idmz.tachtler.net destination acl intra_dst dst 192.168.2.0/24 # intra.tachtler.net destination # Tachtler - disabled IPv6 - # default: acl localnet src fc00::/7 # RFC 4193 local private network range # default: acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines acl SSL_ports port 443 # Tachtler - Safe_ports configuration - acl Safe_ports port 80 # http acl Safe_ports port 21 # ftp acl Safe_ports port 443 # https # default: acl Safe_ports port 70 # gopher # default: acl Safe_ports port 210 # wais acl Safe_ports port 1025-65535 # unregistered ports # default: acl Safe_ports port 280 # http-mgmt # default: acl Safe_ports port 488 # gss-http # default: acl Safe_ports port 591 # filemaker # default: acl Safe_ports port 777 # multiling http # Tachtler - CONNECT configuration - # Tachtler - Pidgin acl pidgin_CONNECT_ports port 5190 # Pidgin (proxy) acl pidgin_CONNECT_ports port 5222-5223 # Pidgin # Tachtler - AirDroid acl airdroid_CONNECT_ports port 8888-8890 # AirDroid # Tachtler - LDAP authentication - acl ldap_auth proxy_auth REQUIRED acl CONNECT method CONNECT # Tachtler - ACL follow_x_forwarded_for configuration - follow_x_forwarded_for allow localhost follow_x_forwarded_for allow idmz_net follow_x_forwarded_for allow intra_net # Tachtler - ACL dstdomain (Destination Domain) configuration - # Tachtler - Microsoft Windows-Update acl windowsupdate_CONNECT_dstdomain dstdomain www.update.microsoft.com acl windowsupdate_CONNECT_dstdomain dstdomain sls.micrsoft.com acl windowsupdate dstdomain .windowsupdate.microsoft.com acl windowsupdate dstdomain download.microsoft.com acl windowsupdate dstdomain .update.microsoft.com acl windowsupdate dstdomain .download.windowsupdate.com acl windowsupdate dstdomain dmd.metaservices.microsoft.com acl windowsupdate dstdomain redir.metaservices.microsoft.com acl windowsupdate dstdomain images.metaservices.microsoft.com acl windowsupdate dstdomain c.microsoft.com acl windowsupdate dstdomain wustat.windows.com acl windowsupdate dstdomain crl.microsoft.com acl windowsupdate dstdomain ctldl.windowsupdate.com acl windowsupdate dstdomain sls.microsoft.com acl windowsupdate dstdomain productactivation.one.microsoft.com acl windowsupdate dstdomain ntservicepack.microsoft.com acl windowsupdate dstdomain watson.microsoft.com acl windowsupdate dstdomain www.microsoft.com acl windowsupdate dstdomain www.msftncsi.com acl windowsupdate dstdomain spynet2.microsoft.com acl windowsupdate dstdomain sqm.telemetry.microsoft.com acl windowsupdate dstdomain iecvlist.microsoft.com acl windowsupdate dstdomain sqm.microsoft.com # Tachtler - Pidgin acl pidgin_CONNECT_dstdomain dstdomain proxy.eu.jabber.org acl pidgin_CONNECT_dstdomain dstdomain slogin.icq.com # Tachtler - ACL url-regex (URL regular expression) configuration - # Tachtler - Microsoft Windows Productactivation acl noauthsites url_regex productactivation\.one\.microsoft\.com:443 acl noauthsites url_regex activation\.sls\.microsoft\.com:443 # Tachtler - Microsoft Windows Online-Help acl noauthsites url_regex windowshelp\.microsoft\.com/* # Tachtler - Microsoft Internet Explorer Search-Engine-Updates acl noauthsites url_regex www\.iegallery\.com/de/* # # Recommended minimum Access Permission configuration: # # Deny requests to certain unsafe ports http_access deny !Safe_ports # Deny CONNECT to other than secure SSL ports # Tachtler # default: http_access deny CONNECT !SSL_ports http_access deny CONNECT !SSL_ports !pidgin_CONNECT_ports !airdroid_CONNECT_ports # Only allow cachemgr access from localhost http_access allow localhost manager http_access deny manager # We strongly recommend the following be uncommented to protect innocent # web applications running on the proxy server who think the only # one who can access services on "localhost" is a local user # Tachtler - enabled, deny access to localhost via squid proxy - # default: #http_access deny to_localhost http_access deny to_localhost # # INSERT YOUR OWN RULE(S) HERE TO ALLOW ACCESS FROM YOUR CLIENTS # # Example rule allowing access from your local networks. # Adapt localnet in the ACL section to list your (internal) IP networks # from where browsing should be allowed # Tachtler - access rules - # default: http_access allow localnet # default: http_access allow localhost # Tachtler - Microsoft Windows-Update http_access allow CONNECT windowsupdate_CONNECT_dstdomain intra_net http_access allow windowsupdate intra_net # Tachtler - Pidgin http_access allow CONNECT pidgin_CONNECT_dstdomain intra_net http_access allow pidgin_CONNECT_ports intra_net # Tachtler - AirDroid http_access allow airdroid_CONNECT_ports intra_net # Tachtler - Access part of local networks without authentication - http_access allow intra_net idmz_dst http_access allow intra_net edmz_dst # Tachtler - LDAP authentication - http_access allow localhost http_access allow idmz_net http_access allow edmz_net http_access allow intra_net noauthsites http_access allow intra_net ldap_auth # And finally deny all other access to this proxy http_access deny all # Squid normally listens to port 3128 # Tachtler - ssl_bump configuration - # default: http_port 3128 http_port 3128 ssl-bump generate-host-certificates=on dynamic_cert_mem_cache_size=4MB key=/etc/pki/proxy/private/proxyCA.key cert=/etc/pki/proxy/certs/proxyCA.crt ssl_bump server-first all sslproxy_options NO_SSLv2,NO_SSLv3,SINGLE_DH_USE sslcrtd_program /usr/lib64/squid/ssl_crtd -s /var/lib/ssl_squid -M 4MB sslcrtd_children 5 startup=1 idle=1 # Uncomment and adjust the following to add a disk cache directory. #cache_dir ufs /var/spool/squid 100 16 256 # Leave coredumps in the first cache dir coredump_dir /var/spool/squid # # Add any of your own refresh_pattern entries above these. # refresh_pattern ^ftp: 1440 20% 10080 refresh_pattern ^gopher: 1440 0% 1440 refresh_pattern -i (/cgi-bin/|\?) 0 0% 0 refresh_pattern . 0 20% 4320 # Tachtler - Microsoft Windows-Update # Tachtler - CAUTION - violates HTTP, but necessary! refresh_pattern -i microsoft.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windowsupdate.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windows.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims # Tachtler - Administrative parameter - # Tachtler - cache_mgr - default: root, presents the mail to user for e-mails from squid-cache cache_mgr squid # Tachtler - mail_from - presents the rcpt to user for emails from squid-cache mail_from squid-cache@tachtler.net # Tachtler - visible_hostname - hostname presented in error messages etc. visible_hostname proxy.idmz.tachtler.net # Tachtler - unique_hostname - hostname, that identifies this squid-cache unique_hostname proxy.idmz.tachtler.net # Tachtler - hostname_aliases - a list of hostnames, thas presented in the DNS for this squid-cache hostname_aliases server50.idmz.tachtler.net # Tachtler - Error page language and settings - # Tachtler - error_default_language error_default_language de-de # Tachtler - Logfile settings - # Tachtler - strip_query_terms - default: on - squid-cache strips query terms from requested URLs before logging. # This protects your users's privacy and reduces log size. # But you can disable this, to see the FULL URL used by squid-cache. strip_query_terms off # Tachtler - DNS-Query order - # Tachtler - dns_v4_first - default: off - controls the order of IPv6 and IPv4 DNS-Requests. dns_v4_first on # Tachtler - Miscellaneous Settings - # Tachtler - forwarded_for - default: on - controls, how squid-cache dealing with X-Forwarded-For Header. # forwarded_for on|off|transparent|truncate|delete forwarded_for delete # Tachtler - Cache Manager configuration - cachemgr_passwd disable shutdown offline_toggle cachemgr_passwd bekannt info cachemgr_passwd geheim all
Erklärungen:
Nachfolgende Erklärungen beschreiben die einzelnen Konfigurationsdirektiven zur ssl_bump-Konfiguration.
# Squid normally listens to port 3128 # Tachtler - ssl_bump configuration - # default: http_port 3128 http_port 3128 ssl-bump generate-host-certificates=on dynamic_cert_mem_cache_size=4MB key=/etc/pki/proxy/private/proxyCA.key cert=/etc/pki/proxy/certs/proxyCA.crt ssl_bump server-first all sslproxy_options NO_SSLv2,NO_SSLv3,SINGLE_DH_USE sslcrtd_program /usr/lib64/squid/ssl_crtd -s /var/lib/ssl_squid -M 4MB sslcrtd_children 5 startup=1 idle=1
http_port 3128 ssl-bump generate-host-certificates=on dynamic_cert_mem_cache_size=4MB key=/etc/pki/squid/private/squidCA.key cert=/etc/pki/squid/certs/squidCA.crt
Es wird die Konfiguration des http_port 3128 um nachfolgende Parameter ergänzt:
ssl-bump- Einschalten der „man-in-the-middle“ Funktionalitätgenerate-host-certificates=on- Einschalten der dynamischen Zertifikatserstellung „on-the-fly“dynamic_cert_mem_cache_size=4MB- Größe des zu verwendenden Speicher für die Zertifikate,
4 MegaByte entsprechen dabei ca. 1.000 Zertifikatenkey=/etc/pki/squid/private/squidCA.key- Speicherort des Schlüssels (key) der verwendet werden sollcert=/etc/pki/squid/certs/squidCA.crt- Speicherort des Zertifikates (Root-CA) das verwendet werden soll
ssl_bump server-first all
Ermöglicht es dem Squid Proxy-Server, im Modus server-first zuerst eine Verbindung zum Ziel-Server aufzubauen, um anschließend ein Zertifikat unter Zuhilfenahme der eigenen CA zu erstellen, oder ein bereits von der eigenen CA erstelltes Zertifikat zu verwenden, bevor die Kommunikation mit dem z.B. Browser des Endbenutzer statt findet.

deny all gesetzt werden !
sslproxy_options NO_SSLv2,NO_SSLv3,SINGLE_DH_USE
Weist den Squid Proxy-Server an, die angegebenen Cipher-Suiten nur zu verwenden.
sslcrtd_program /usr/lib64/squid/ssl_crtd -s /var/lib/ssl_squid -M 4MB
Bestimmt welches Programm der Squid Proxy-Server zur Erstellung der Zertifikate „on-the-fly“ unter Zuhilfenahme der eigenen CA verwenden soll und wie das Verzeichnis erstellt werden soll, die die so erstellten Zertifikate aufnehmen soll. Ebenfalls muss die maximale Größe des Verzeichnisses, hier mit 4 MegaByte angegeben, beziffert werden.
sslcrtd_children 5 startup=1 idle=1
Gibt an wie viele Prozesse zur Erstellung von Zertifikaten „on-the-fly“ gestartet werden sollen, und in welcher Ausprägung.
Verzeichnis /var/lib/ssl_squid einrichten
Nachdem die Konfiguration des Squid Proxy-Servers zur Nutzung mit ssl_bump erfolgreich abgeschlossen ist, ist es noch erforderlich nachfolgendes Verzeichnis, welche die „on-the-fly“ unter Zuhilfenahme der eigenen CA erstellten Zertifikate, aufnehmen soll einzurichten.
/var/lib/ssl_squid
Nachfolgender Befehl erstellt das Verzeichnis und dessen Komponenten unter Zuhilfenahme des Programms
/usr/lib64/squid/ssl_crtd
# /usr/lib64/squid/ssl_crtd -c -s /var/lib/ssl_squid Initialization SSL db... Done
Anschließend werden mit nachfolgendem Befehl die Besitzrechte
# chown -R squid:squid /var/lib/ssl_squid
für das Verzeichnis und das darin enthaltene Unterverzeichnis und die Dateien entsprechend gesetzt.
Abschließend kann mit nachfolgendem Befehl überprüft werden, ob das Verzeichnis und das darin enthaltene Unterverzeichnis und die Dateien richtig erstellt wurden, was eine Ausgabe, wie die nachfolgend gezeigte, zum Vorschein bringen sollte:
# ls -l /var/lib/ssl_squid total 4 drwxr-xr-x 2 squid squid 6 Mar 5 10:58 certs -rw-r--r-- 1 squid squid 0 Mar 5 10:58 index.txt -rw-r--r-- 1 squid squid 1 Mar 5 10:58 size
Browser-Konfiguration
Nachfolgend soll die Konfiguration eines Browsers, in diesem Fall der Browser Mozilla Firefox Desktop Variante, durchgeführt werden.
Proxy-Konfiguration
Nachdem nachfolgende Konfiguration im Browser, hier am Beispiel eines Mozilla Firefox-Browsers, wie in nachfolgender Bildschirmkopie dargestellt, durchgeführt wurde, sollte mit dem Surfen, auch auf HTTPS gesicherte Seiten, über den Squid Proxy-Server nichts mehr im Wege stehen:
Nachfolgende Einstellungen sind im Mozilla Firefox-Browsers unter
- Open Menu (Menü) | Preferences (Einstellungen) | Advanced (Erweitert) | Network (Netzwerk) | Settings… (Einstellungen…) | Manual proxy configuration (Manuelle Proxy-Konfiguration)
durchzuführen:
Browser HTTPS Aufruf
Anschließend sollte nun beim Aufruf einer Website wie z.B. https://www.google.de nachfolgendes Browser-Dialog-Fenster erscheinen und zur Eingabe eines Benutzernamens eines Passwortes auffordern, wie auf nachfolgender Bildschirm dargestellt:
Anschließend sollte, korrekterweise nachfolgende Reaktion des Mozilla Firefox-Browsers auf die „man-in-the-moddle“ Attacke, durch den Squid Proxy-Server erfolgen, wie in nachfolgender Bildschirmkopie dargestellt:

Erklärung:
Was ist hier passiert? - Korrekterweise erkennt der Mozilla Firefox-Browsers, dass es sich hierbei um kein Zertifikat für https://www.google.de, welches von einer vertrauenswürdigen Root-CA ausgestellt wurde, handelt.
Nachfolgende Bildschirmkopien zeigen den Unterschied.
Als erstes kann im aktuellen Mozilla Firefox-Browser Fenster nun auf den Bereich
- I Understand the Risks (Ich kenne das Risiko)
mit der linken Maustaste geklickt werden, wonach nachfolgende Erweiterung der aktuell dargestellten Fehlerseite erscheinen sollte:
Anschließend kann nun mit der linken Maustaste auf die Schaltfläche [Add Exception…] ([Ausnahme hinzufügen…]) geklickt werden, woraufhin sich nachfolgendes zusätzliches Dialog-Fenster öffnet:

- Permanentliy store this exception (Diese Ausnahme dauerhaft speichern)
entfernt werden, um später keine verfälschten Ergebnisse zu erhalten!
Anschließend sollte mit der linken Maustaste auf die Schaltfläche [Get Certificate] ([Zertifikat herunterladen]) geklickt werden, um sich Details zum verwendeten Zertifikat anzeigen zu lassen, welches nachfolgendes weiteres Dialogfenster öffnen sollte:
| Zertifikat aus „man-in-the-middle“ vom Squid Proxy-Server | Zertifikat von der Original Web-Seite |
|---|---|
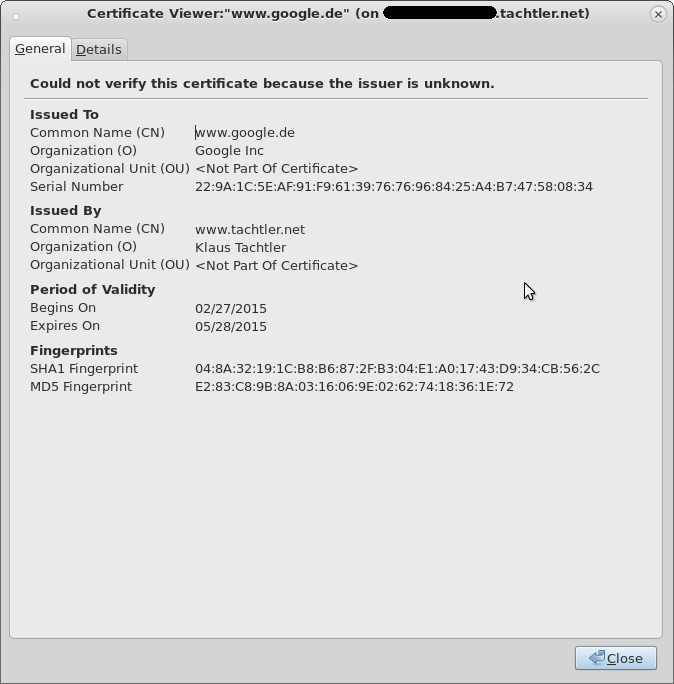 | 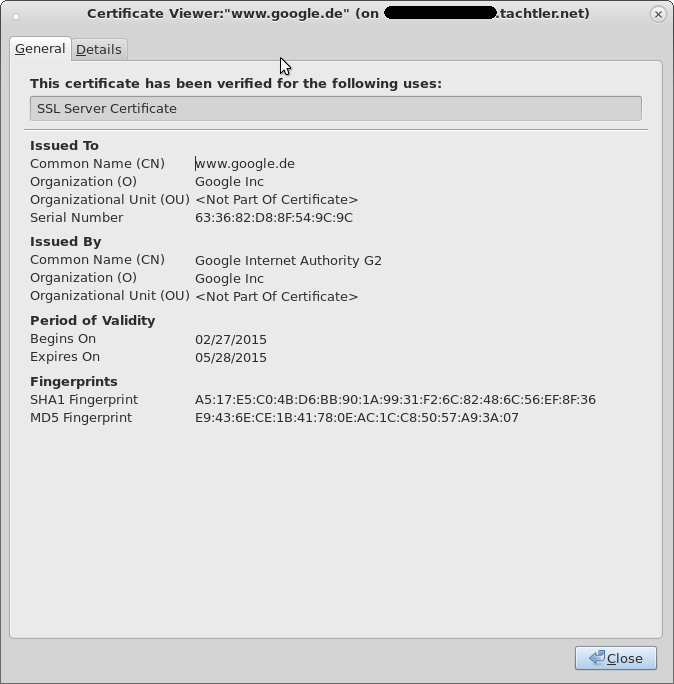 |
Der relevante Unterschied sind hier die Angaben bei: Issued by (Augestellt von)
| Zertifikat aus „man-in-the-middle“ vom Squid Proxy-Server | Zertifikat von der Original Web-Seite | ||
|---|---|---|---|
| Common Name (CN) | www.tachtler.net | Common Name (CN) | Google Internet Authority G2 |
| Organization (O) | Klaus Tachtler | Organization (O) | Google Inc |
| Organizational Unit (OU) | <Not Part Of Certificate> | Organizational Unit (OU) | <Not Part Of Certificate> |

Browser Root-Zertifikat importieren
Um das, wie unter nachfolgendem internen Link beschrieben Verhalten zu verhindern,
ist es erforderlich das Root-Zertifikat aus der eigenen CA welche, wie unter nachfolgendem internen Link dargestellt
erstellt wurde, in den jeweiligen Browser des Endbenutzers zu importieren!
Ausgehend davon, das die Root-Zertifikat aus der eigenen CA bereits heruntergeladen wurden und hier als Beispiel im Verzeichnis - /tmp/squidCA.crt gespeichert wurden.
Nachfolgende Einstellungen sind im Mozilla Firefox-Browsers unter
- Open Menu (Menü) | Preferences (Einstellungen) | Advanced (Erweitert) | Certificates (Zertifikate)
durchzuführen:
Anschließend sollte dann auf die Schaltfläche [View Certificates] ([Zertifikate anzeigen]) geklickt werden, damit sich nachfolgender Dialog öffnet und der [Reiter: Authorities (Zertifizierungsstellen)] ausgewählt sein sollte:
Durch anklicken der Schaltfläche [Import…] ([Importieren…]), kann dann im sich öffnenden Dialog-Fenster eine Zertifikatsdatei, hier
/tmp/squidCA.crt
ausgewählt werden:
Durch drücken der Schaltfläche [Open] ([Speichern]) wird dann nachfolgendes Dialog-Fenster angezeigt, in dem der Rahmen festgelegt werden kann, in welchem Umfang dem Zertifikat vertraut wird. Nachfolgend wurden alle Haken entsprechend wie nachfolgend beschrieben gesetzt:
| Haken | Bezeichnung |
|---|---|
| ✔ | Trust this CA to identify websites. |
| ✔ | Trust this CA to identify email users. |
| ✔ | Trust this CA to identify software developers. |
Zum Abschluss und zum tatsächlichen Import muss dann die Schaltfläche [OK] angeklickt werden.
Anschließend kann dann in der Liste der importierten Zertifikate überprüft werden ob der jeweilig Importvorgang erfolgreich war und es sollte eine Anzeige wie die nachfolgende zur Anzeige kommen:
Anschließend sollte nun beim Aufruf einer Website wie z.B. https://www.google.de nachfolgendes Browser-Dialog-Fenster erscheinen und zur Eingabe eines Benutzernamens eines Passwortes auffordern, wie auf nachfolgender Bildschirm dargestellt:
Anschließend sollte nun im Mozilla Firefox-Browsers auf die „man-in-the-middle“ Attacke, durch den Squid Proxy-Server kein Zertifikats-Hinweis mehr erfolgen!
Portal Splash Pages
Mit dem Einsatz von Squid als Proxy-Server besteht die Möglichkeit, vor der Nutzung von Squid, eine sogenannte „Splash Page“ (Vorabanzeige Seite) einzublenden, wodurch z.B. Benutzerbedingungen, Bedienhinweise oder andere Informationen vorab dem Benutzer angezeigt werden können.
| Beschreibung | Externer Link |
|---|---|
| Homepage | http://www.squid-cache.org/ |
| Portal Splash Pages | http://wiki.squid-cache.org/ConfigExamples/Portal/Splash |
Nachfolgende Skizze beschreibt vereinfacht die Funktionsweise des Squid Proxy-Servers unter Verwendung einer „Portal Splash Page“-Konfiguration in Kombination mit einr Authentifizierung des Benutzers gegen LDAP:
+--------------------------+ +----------------------------------------------+ +-----------+ | | | squid-cache | | Browser | | | | | | | | | | 1. squid nimmt Anfrage vom Browser entgegen | <-1-- | Anfrage | | | | | | | | | | 2. squid Anzeige der Authentifizierung-LDAP | --2-> | Anzeige | | | | 3. user Benutzername/Passwort Eingaben | <-3-- | Benutzer/ | | | | | | Passwort | | | | | | | | | | !. squid überprüft Benutzername/Passwort und | | | | | | ACL für den Zugriff, (hier erfolgreich !) | | | | | | | | | | | | 4. squid blendet die Portal Splash Page ein | --4-> | Anzeige | | | | 5. user drückt die "Zustimmen" Schaltfläche | <-5-- | Zustimmen | | | | | | | | | | !. squid laden der Portal Accept Page mit | | | | | | einem "redirect" auf die eigentliche URL | | | | | | des Browsers/Benutzers | | | | | | | | | | http://www.tachtler.net | <-6-- | 6. squid laden der eigentlichen user URL | | | | http://www.tachtler.net | --7-> | 7. squid erhält Daten der eigentlichen URL | | | | | | | | | | | | 8. squid gibt Anfrage an den Browser zurück | --8-> | Antwort | | | | | | | +--------------------------+ +----------------------------------------------+ +-----------+
Portal Splash Pages - Installation
Zu späteren Verwendung von PHP-Seiten, soll nachfolgend PHP installiert werden.
Zur Installation von PHP wird nachfolgendes Paket benötigt:
Mit nachfolgendem Befehl, wird das Pakete php installiert:
# yum install php Loaded plugins: changelog, priorities 61 packages excluded due to repository priority protections Resolving Dependencies --> Running transaction check ---> Package php.x86_64 0:5.4.16-23.el7_0.3 will be installed --> Finished Dependency Resolution Changes in packages about to be updated: Dependencies Resolved ================================================================================ Package Arch Version Repository Size ================================================================================ Installing: php x86_64 5.4.16-23.el7_0.3 updates 1.3 M Transaction Summary ================================================================================ Install 1 Package Total download size: 1.3 M Installed size: 4.4 M Is this ok [y/d/N]: y ownloading packages: php-5.4.16-23.el7_0.3.x86_64.rpm | 1.3 MB 00:00 Running transaction check Running transaction test Transaction test succeeded Running transaction Installing : php-5.4.16-23.el7_0.3.x86_64 1/1 Verifying : php-5.4.16-23.el7_0.3.x86_64 1/1 Installed: php.x86_64 0:5.4.16-23.el7_0.3 Complete!
Mit nachfolgendem Befehl kann überprüft werden, welche Inhalte mit den Paket php installiert wurden.
# rpm -qil php Name : php Version : 5.4.16 Release : 23.el7_0.3 Architecture: x86_64 Install Date: Thu 04 Dec 2014 09:15:06 PM CET Group : Development/Languages Size : 4595894 License : PHP and Zend and BSD Signature : RSA/SHA256, Fri 31 Oct 2014 03:24:33 PM CET, Key ID 24c6a8a7f4a80eb5 Source RPM : php-5.4.16-23.el7_0.3.src.rpm Build Date : Fri 31 Oct 2014 02:07:27 PM CET Build Host : worker1.bsys.centos.org Relocations : (not relocatable) Packager : CentOS BuildSystem <http://bugs.centos.org> Vendor : CentOS URL : http://www.php.net/ Summary : PHP scripting language for creating dynamic web sites Description : PHP is an HTML-embedded scripting language. PHP attempts to make it easy for developers to write dynamically generated web pages. PHP also offers built-in database integration for several commercial and non-commercial database management systems, so writing a database-enabled webpage with PHP is fairly simple. The most common use of PHP coding is probably as a replacement for CGI scripts. The php package contains the module (often referred to as mod_php) which adds support for the PHP language to Apache HTTP Server. /etc/httpd/conf.d/php.conf /etc/httpd/conf.modules.d/10-php.conf /usr/lib64/httpd/modules/libphp5.so /usr/share/httpd/icons/php.gif /var/lib/php/session
Portal Splash Pages - Vorbereitungen
/var/lib/squid/sessions
bevor mit der eigentlichen Konfiguration begonnen werden kann, muss mit nachfolgendem Befehl nachfolgendes Verzeichnis erstellt werden:
# mkdir -p /var/lib/squid/sessions
Anschließend müssen mit nachfolgendem Befehl, die Besitzrechte entsprechend zugewiesen werden:
# chown squid:squid /var/lib/squid
Vorhergehendes Verzeichnis dient der Aufnahme einer BerkelyDB in der Session-Informationen vom Squid abgelegt werden und müssen durch dieser beschreibbar sein.
/usr/share/squid/html/splash.php
Nachfolgend eine mögliche Portal Splash Page in zum Teil PHP gestaltet, welche zur Anzeige kommt, bevor der Benutzer weitere Seiten aufrufen kann:
Der nachfolgend gezeigte Inhalt einer möglichen Portal Splash Page ist in nachfolgendem Verzeichnis, mit z.B. nachfolgendem Befehl, zu erstellen:
# touch /usr/share/squid/html/splash.php
Beispiel:
<!DOCTYPE html PUBLIC "-//W3C//DTD HTML 4.01//EN" "http://www.w3.org/TR/html4/strict.dtd"> <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=utf-8"> <title>Benutzerrichtlinie Infrastruktur des Betreibers</title> <style type="text/css"> <!-- /* Stylesheet for Squid Error pages Adapted from design by Free CSS Templates http://www.freecsstemplates.org Released for free under a Creative Commons Attribution 2.5 License */ /* Page basics */ * { font-family: verdana, sans-serif; } html body { margin: 0; padding: 0; background: #efefef; font-size: 12px; color: #1e1e1e; } /* Page displayed title area */ #titles { margin-left: 15px; padding: 10px; padding-left: 100px; /* Tachtler */ /* default: background: url('http://www.squid-cache.org/Artwork/SN.png') no-repeat left; */ background: url('http://squid.tachtler.net/icons/SN.png') no-repeat left; left; } /* initial title */ #titles h1 { color: #000000; } #titles h2 { color: #000000; } /* special event: FTP success page titles */ #titles ftpsuccess { background-color: #00ff00; width: 100%; } /* Page displayed body content area */ #content { padding: 10px 15px 10px 10px; background: #ffffff; } textarea { font-family: sans-serif; color: black; font-size: 10pt; width: 100%; } /* General text */ p { } /* error brief description */ #error p { } /* some data which may have caused the problem */ #data { } /* the error message received from the system or other software */ #sysmsg { } pre { font-family: sans-serif; } /* special event: FTP / Gopher directory listing */ #dirmsg { font-family: courier; color: black; font-size: 10pt; } #dirlisting { margin-left: 2%; margin-right: 2%; } #dirlisting tr.entry td.icon,td.filename,td.size,td.date { border-bottom: groove; } #dirlisting td.size { width: 50px; text-align: right; padding-right: 5px; } /* horizontal lines */ hr { margin: 0; } /* page displayed footer area */ #footer { font-size: 9px; padding-left: 10px; } body :lang(fa) { direction: rtl; font-size: 100%; font-family: Tahoma, Roya, sans-serif; float: right; } :lang(he) { direction: rtl; } --> </style> </head> <body id=BENUTZERRICHTLINIE> <div id="titles"> <h1>Benutzerrichtlinie</h1> <h2>für die Infrastruktur des Betreibers</h2> </div> <hr> <div id="content"> <p> <b><u>Betreiber</u></b> </p> <blockquote id="error"> <p> <b>Thomas Mustermann</b><br> Strasse Hausnummer<br> PLZ Ort </p> </blockquote> <p> <textarea rows="5" readonly> Benutzerrichtlinie für die Infrastruktur des Betreibers... <hier eigene Richtlinien einfügen...> </textarea> </p> <p> Kontakt zum <a href="mailto:ihre-email-adresse@example.com?subject=Benutzerrichtlinie">Betreiber</a>. </p> </div> <hr> <div id="footer"> <?php session_start(); $_SESSION["goto"] = htmlspecialchars($_GET["url"]); ?> <br> <form action="http://www.squid.tachtler.net/html/accept.php" target="_self"> <input type="submit" value="Zustimmen"> </form> <p> <?php date_default_timezone_set("Europe/Berlin"); // date_default_timezone_set("GMT"); $timestamp = time(); $datum = date("D, d M Y",$timestamp); $uhrzeit = date("H:i:s T",$timestamp); echo "Erzeugt am ",$datum," ",$uhrzeit; ?> </p> </div> </body> </html>
Entscheidend ist nur nachfolgender PHP/HTML-Code, alles andere ist das Design der HTML/PHP-Seite:
<br> <form action="http://www.squid.tachtler.net/html/accept.php" target="_self"> <input type="submit" value="Zustimmen"> </form> <p>
Oben stehender Code führt nachfolgende Funktionen aus:
- Erstellen einer Schaltfläche mit dem Namen -
Zustimmenund der damit verbundenen Aktion - Aufruf der Seite -http://www.squid.tachtler.net/html/accept.phpim gleichen Fenster.
Eigene Anpassungen:
In nachfolgendem Bereich der oben gezeigten Portal Splash Page sollten eigene Anpassungen durchgeführt werden:
(Nur relevanter Ausschnitt):
--> </style> </head> <body id=BENUTZERRICHTLINIE> <div id="titles"> <h1>Benutzerrichtlinie</h1> <h2>für die Infrastruktur des Betreibers</h2> </div> <hr> <div id="content"> <p> <b><u>Betreiber</u></b> </p> <blockquote id="error"> <p> <b>Thomas Mustermann</b><br> Strasse Hausnummer<br> PLZ Ort </p> </blockquote> <p> <textarea rows="5" readonly> Benutzerrichtlinie für die Infrastruktur des Betreibers... <hier eigene Richtlinien einfügen...> </textarea> </p> <p> Kontakt zum <a href="mailto:ihre-email-adresse@example.com?subject=Benutzerrichtlinie">Betreiber</a>. </p> </div> <hr>
Nach Abschluss der Erstellung der /usr/share/squid/html/splash.php Seite, muss nachfolgender symblischer Link mit nachfolgendem Befehl erstellt werden, da sonst dieser nicht mit dem entsprechendem Aufruf aus der Squid heraus durchgeführt werden kann:
# ln -s /usr/share/squid/html/splash.php splash.php
/usr/share/squid/html/accept.php
Nachfolgend eine mögliche Portal Splash „Accept“ Page im überwiegendem Teil in PHP gestaltet, welche die Weiterleitung auf die ursprünglich durch den Browser/Benutzer eingegebene Seite durchführt:
Der nachfolgend gezeigte Inhalt einer möglichen Portal Splash „Accept“ Page ist in nachfolgendem Verzeichnis, mit z.B. nachfolgendem Befehl, zu erstellen:
# touch /usr/share/squid/html/accept.php
Beispiel:
<?php session_start(); header("Location: " . $_SERVER['HTTP_REFERER'] ); /* Browser umleiten */ session_unset(); session_destroy(); exit; ?> <body> </body> </html>
Oben stehender Code führt nachfolgende Funktionen aus:
- Erstellen/Starten einer PHP-Session.
- Erstellen einer „Browser Umleitung“ unter Einbindung der URL des Browsers/Benutzer, welche dieser ursprünglich erreichen wollte bzw. eingegeben hat
- Leeren der PHP-Session!
- Löschen/Beenden der PHP-Session!
Portal Splash Pages - Konfiguration
Abschließend kann nun die Konfiguration des Squid Proxy-Servers zur Anzeige einer Portal Splash Page durchgeführt werden.

/etc/squid/squid.conf
Nachfolgende Konfiguration ermöglicht die Anzeige einer Portal Splash Page.
Nachfolgende Ergänzungen sind in der Konfigurationsdatei
/etc/squid/squid.conf
notwendig, um die Portal Splash Pages-Konfigurations Definitionen im Squid Proxy-Server einsetzen zu können:
(Komplette Konfigurationsdatei)
# # Recommended minimum configuration: # # Tachtler - LDAP authentication - auth_param basic program /usr/lib64/squid/basic_ldap_auth -b "ou=People,dc=tachtler,dc=net" -f "uid=%s" -h ldap.idmz.tachtler.net -D "cn=Ersatzbenutzer,dc=tachtler,dc=net" -W /etc/squid/ldap_passwd auth_param basic utf8 on auth_param basic children 5 startup=1 idle=1 concurrency=0 auth_param basic realm Bitte geben Sie Ihren Benutzernamen und Ihr Passwort zur Internet-Authentifizierung ein! auth_param basic credentialsttl 60 minutes auth_param basic casesensitive off # Example rule allowing access from your local networks. # Adapt to list your (internal) IP networks from where browsing # should be allowed # Tachtler - disabled default localnet configuration - # default: acl localnet src 10.0.0.0/8 # RFC1918 possible internal network # default: acl localnet src 172.16.0.0/12 # RFC1918 possible internal network # default: acl localnet src 192.168.0.0/16 # RFC1918 possible internal network acl idmz_net src 192.168.0.0/24 # idmz.tachtler.net acl edmz_net src 192.168.1.0/24 # edmz.tachtler.net acl intra_net src 192.168.2.0/24 # intra.tachtler.net acl edmz_dst dst 192.168.0.0/24 # edmz.tachtler.net destination acl idmz_dst dst 192.168.1.0/24 # idmz.tachtler.net destination acl intra_dst dst 192.168.2.0/24 # intra.tachtler.net destination # Tachtler - disabled IPv6 - # default: acl localnet src fc00::/7 # RFC 4193 local private network range # default: acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines acl SSL_ports port 443 # Tachtler - Safe_ports configuration - acl Safe_ports port 80 # http acl Safe_ports port 21 # ftp acl Safe_ports port 443 # https # default: acl Safe_ports port 70 # gopher # default: acl Safe_ports port 210 # wais acl Safe_ports port 1025-65535 # unregistered ports # default: acl Safe_ports port 280 # http-mgmt # default: acl Safe_ports port 488 # gss-http # default: acl Safe_ports port 591 # filemaker # default: acl Safe_ports port 777 # multiling http # Tachtler - CONNECT configuration - # Tachtler - Pidgin acl pidgin_CONNECT_ports port 5190 # Pidgin (proxy) acl pidgin_CONNECT_ports port 5222-5223 # Pidgin # Tachtler - AirDroid acl airdroid_CONNECT_ports port 8888-8890 # AirDroid # Tachtler - LDAP authentication - acl ldap_auth proxy_auth REQUIRED acl CONNECT method CONNECT # Tachtler - ACL follow_x_forwarded_for configuration - follow_x_forwarded_for allow localhost follow_x_forwarded_for allow idmz_net follow_x_forwarded_for allow intra_net # Tachtler - ACL dstdomain (Destination Domain) configuration - # Tachtler - Microsoft Windows-Update acl windowsupdate_CONNECT_dstdomain dstdomain www.update.microsoft.com acl windowsupdate_CONNECT_dstdomain dstdomain sls.micrsoft.com acl windowsupdate dstdomain .windowsupdate.microsoft.com acl windowsupdate dstdomain download.microsoft.com acl windowsupdate dstdomain .update.microsoft.com acl windowsupdate dstdomain .download.windowsupdate.com acl windowsupdate dstdomain dmd.metaservices.microsoft.com acl windowsupdate dstdomain redir.metaservices.microsoft.com acl windowsupdate dstdomain images.metaservices.microsoft.com acl windowsupdate dstdomain c.microsoft.com acl windowsupdate dstdomain wustat.windows.com acl windowsupdate dstdomain crl.microsoft.com acl windowsupdate dstdomain ctldl.windowsupdate.com acl windowsupdate dstdomain sls.microsoft.com acl windowsupdate dstdomain productactivation.one.microsoft.com acl windowsupdate dstdomain ntservicepack.microsoft.com acl windowsupdate dstdomain watson.microsoft.com acl windowsupdate dstdomain www.microsoft.com acl windowsupdate dstdomain www.msftncsi.com acl windowsupdate dstdomain spynet2.microsoft.com acl windowsupdate dstdomain sqm.telemetry.microsoft.com acl windowsupdate dstdomain iecvlist.microsoft.com acl windowsupdate dstdomain sqm.microsoft.com # Tachtler - Pidgin acl pidgin_CONNECT_dstdomain dstdomain proxy.eu.jabber.org acl pidgin_CONNECT_dstdomain dstdomain slogin.icq.com # Tachtler - ACL url-regex (URL regular expression) configuration - # Tachtler - Microsoft Windows Productactivation acl noauthsites url_regex productactivation\.one\.microsoft\.com:443 acl noauthsites url_regex activation\.sls\.microsoft\.com:443 # Tachtler - Microsoft Windows Online-Help acl noauthsites url_regex windowshelp\.microsoft\.com/* # Tachtler - Microsoft Internet Explorer Search-Engine-Updates acl noauthsites url_regex www\.iegallery\.com/de/* # # Recommended minimum Access Permission configuration: # # Deny requests to certain unsafe ports http_access deny !Safe_ports # Deny CONNECT to other than secure SSL ports # Tachtler # default: http_access deny CONNECT !SSL_ports http_access deny CONNECT !SSL_ports !pidgin_CONNECT_ports !airdroid_CONNECT_ports # Only allow cachemgr access from localhost http_access allow localhost manager http_access deny manager # We strongly recommend the following be uncommented to protect innocent # web applications running on the proxy server who think the only # one who can access services on "localhost" is a local user # Tachtler - enabled, deny access to localhost via squid proxy - # default: #http_access deny to_localhost http_access deny to_localhost # # INSERT YOUR OWN RULE(S) HERE TO ALLOW ACCESS FROM YOUR CLIENTS # # Tachtler # splash screen configuration - start - acl proxy url_regex -i http://squid.tachtler.net/* # Set up the session helper in active mode. Mind the wrap - this is one line: external_acl_type session concurrency=100 ttl=3 %SRC /usr/lib64/squid/ext_session_acl -a -T 15 -b /var/lib/squid/sessions/ # Pass the LOGIN command to the session helper with this ACL acl session_login external session LOGIN # Normal session ACL as per simple example acl session_is_active external session # ACL to match URL acl clicked_login_url url_regex -i ^http://squid.tachtler.net/html/accept.php$ # First check for the login URL. If present, login session http_access allow clicked_login_url session_login http_access allow proxy # If we get here, URL not present, so renew session or deny request. http_access deny !session_is_active # Deny page to display deny_info 511:splash.php session_is_active # splash screen configuration - stopp - # Example rule allowing access from your local networks. # Adapt localnet in the ACL section to list your (internal) IP networks # from where browsing should be allowed # Tachtler - access rules - # default: http_access allow localnet # default: http_access allow localhost # Tachtler - Microsoft Windows-Update http_access allow CONNECT windowsupdate_CONNECT_dstdomain intra_net http_access allow windowsupdate intra_net # Tachtler - Pidgin http_access allow CONNECT pidgin_CONNECT_dstdomain intra_net http_access allow pidgin_CONNECT_ports intra_net # Tachtler - AirDroid http_access allow airdroid_CONNECT_ports intra_net # Tachtler - Access part of local networks without authentication - http_access allow intra_net idmz_dst http_access allow intra_net edmz_dst # Tachtler - LDAP authentication - http_access allow localhost http_access allow idmz_net http_access allow edmz_net http_access allow intra_net noauthsites http_access allow intra_net ldap_auth # And finally deny all other access to this proxy http_access deny all # Squid normally listens to port 3128 http_port 3128 # Uncomment and adjust the following to add a disk cache directory. #cache_dir ufs /var/spool/squid 100 16 256 # Leave coredumps in the first cache dir coredump_dir /var/spool/squid # # Add any of your own refresh_pattern entries above these. # refresh_pattern ^ftp: 1440 20% 10080 refresh_pattern ^gopher: 1440 0% 1440 refresh_pattern -i (/cgi-bin/|\?) 0 0% 0 refresh_pattern . 0 20% 4320 # Tachtler - Microsoft Windows-Update # Tachtler - CAUTION - violates HTTP, but necessary! refresh_pattern -i microsoft.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windowsupdate.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims refresh_pattern -i windows.com/.*\.(cab|exe|ms[i|u|f]|[ap]sf|wm[v|a]|dat|zip) 4320 80% 43200 reload-into-ims # Tachtler - Administrative parameter - # Tachtler - cache_mgr - default: root, presents the mail to user for e-mails from squid-cache cache_mgr squid # Tachtler - mail_from - presents the rcpt to user for emails from squid-cache mail_from squid-cache@tachtler.net # Tachtler - visible_hostname - hostname presented in error messages etc. visible_hostname proxy.idmz.tachtler.net # Tachtler - unique_hostname - hostname, that identifies this squid-cache unique_hostname proxy.idmz.tachtler.net # Tachtler - hostname_aliases - a list of hostnames, thas presented in the DNS for this squid-cache hostname_aliases server50.idmz.tachtler.net # Tachtler - Error page language and settings - # Tachtler - error_default_language error_default_language de-de # Tachtler - Logfile settings - # Tachtler - strip_query_terms - default: on - squid-cache strips query terms from requested URLs before logging. # This protects your users's privacy and reduces log size. # But you can disable this, to see the FULL URL used by squid-cache. strip_query_terms off # Tachtler - DNS-Query order - # Tachtler - dns_v4_first - default: off - controls the order of IPv6 and IPv4 DNS-Requests. dns_v4_first on # Tachtler - Miscellaneous Settings - # Tachtler - forwarded_for - default: on - controls, how squid-cache dealing with X-Forwarded-For Header. # forwarded_for on|off|transparent|truncate|delete forwarded_for delete # Tachtler - Cache Manager configuration - cachemgr_passwd disable shutdown offline_toggle cachemgr_passwd bekannt info cachemgr_passwd geheim all
Erklärungen:
Nachfolgende Erklärungen beschreiben die einzelnen Konfigurationsdirektiven zur Portal Splash Page-Konfiguration.
# Tachtler # splash screen configuration - start - acl proxy url_regex -i http://squid.tachtler.net/* # Set up the session helper in active mode. Mind the wrap - this is one line: external_acl_type session concurrency=100 ttl=3 %SRC /usr/lib64/squid/ext_session_acl -a -T 15 -b /var/lib/squid/sessions/ # Pass the LOGIN command to the session helper with this ACL acl session_login external session LOGIN # Normal session ACL as per simple example acl session_is_active external session # ACL to match URL acl clicked_login_url url_regex -i ^http://squid.tachtler.net/html/accept.php$ # First check for the login URL. If present, login session http_access allow clicked_login_url session_login http_access allow proxy # If we get here, URL not present, so renew session or deny request. http_access deny !session_is_active # Deny page to display deny_info 511:splash.php session_is_active # splash screen configuration - stopp -
acl proxy url_regex -i http://squid.tachtler.net/*
Definition der der ACL proxy hinter der sich z.B die PHP-Seiten und ggf. Images für den Aufruf der splash.php befinden.
external_acl_type session concurrency=100 ttl=3 %SRC /usr/lib64/squid/ext_session_acl -a -T 60 -b /var/lib/squid/sessions/
Erstellen eines AKTIVEN-Session mit einer Anmeldungsdauer zum TESTEN von 60 Sekunden und unter Zuhilfenahme eines externen Programms /usr/lib64/squid/ext_session_acl ebenfalls mit einer Session-Laufzeit zum TESTEN von 60 Sekunden, welche in einer BerkelyDB unter nachfolgendem Pfad /var/lib/squid/sessions/ abgelegt wird.
acl session_login external session LOGIN
ACL welche die Anmeldeinformationen aus dem AKTIVEN-Session Hilfsprogramm ebenfalls an die Session bindet.
acl clicked_login_url url_regex -i ^http://squid.tachtler.net/html/accept.php$
ACL welche zutrifft, wenn die definierte URL, hier URL - http://squid.tachtler.net/html/accept.php aufgerufen wird, diese in der Session als aufgerufen zu kennzeichnen.
http_access allow clicked_login_url session_login
Überprüfung, wenn die URL - http://squid.tachtler.net/html/accept.php noch nicht aufgerufen wurde, den Zugriff auf die ursprüngliche vom Browser/Benutzer angeforderte URL zu verweigern!
http_access allow proxy
Zugriff auf die Ressource welche in der ACL proxy definiert wurde, auch ohne Aufrufzustimmung zulassen.
http_access deny !session_is_active
Alle weiteren Zugriffe verweigern, bis die aktive Session mit der definierten URL, hier URL - http://squid.tachtler.net/html/accept.php aufgerufen wurde, und diese in der Session als aufgerufen gekennzeichnet wurde.
deny_info 511:splash.php session_is_active
Anzeige der sogenannten deny_info - was der Portal Splash Page entspricht, solange die URL - http://squid.tachtler.net/html/accept.php nicht aufgerufen wurde!
Portal Splash Pages - Test
Anschließend kann dies nun wie folgt getestet werden:
Schritt 1: Aufruf einer URL, hier http://www.google.de im Browser und Authentifizierung gegen LDAP:
Schritt 2: Anzeige der Portal Splash Page mit anschließendem drücken der Schaltfläche [Zustimmen]
Schritt 3: Anzeige der ursprünglich durch den Benutzer eingegebenen URL durch „redirect“ über die Portal Splash „Accept“ Page:
SquidAnalyzer
SquidAnalyzer untersucht standardmäßig die Log-Datei
/var/log/squid/access.log- im Standard-Log-Format von Squid
und erstellt Statistiken und Reports über Zugriffe, Bytes, Benutzer, Netze, Listen von URL's und Listen von Domains.
Die Auswertungen orientieren sich an den Benutzern und an der Bandbreite des installierten Squid.
SquidAnalyzer nutzt dabei eine einfache Dateistruktur, um die Daten zu speichern. Der Betrieb einer Datenbank, wie MariaDB, MySQL, SQL Lite oder einer Berkelay DB ist nicht erforderlich.
Der SquidAnalyzer wertet die Daten inkrementell aus, deshalb sollte z.B. nächtlich oder sogar stündlich eine cron-Job zur Auswertung und Erstellung der Statistiken und Reports ausgeführt werden.

Andere Log-Formate wie z.B.
- squidmime
- common
- combined
werden NICHT unterstützt!
SquidAnalyzer - Voraussetzungen
Als Voraussetzung für die Installation von SquidAnalyzer sind folgende Komponenten erforderlich:
- Lauffähiger Proxy-Server Squid
- Siehe auch den internen Link: squid CentOS 7
- Lauffähiger Web-Server z.B. Apache HTTP Server
- Siehe auch den internen Link: Apache HTTP Server CentOS 7
Nachfolgende rpm-Pakete sind als Abhängigkeit erforderlich und werden ebenfalls benötigt:
SquidAnalyzer - Externes Repository
Zur Installation des SquidAnalyzer soll ein externes Repository genutzt werden.

rpm-Pakete.
Zur Einbindung des externen Repositories von
sind nachfolgende Schritte notwendig.
Mit nachfolgendem Befehlen kann ein rpm-Installationspaket heruntergeladen und installiert werden, mit dem das externe Repository von http://repo.mailserver.guru als Drittrepository im Betriebssystem, als zusätzliche Quelle, eingebunden werden kann.
Zuerst sollte mit nachfolgendem Befehl in das Verzeichnis /tmp gewechselt werden:
# cd /tmp
Nachfolgender Befehl kann das entsprechende rpm-Paket für das externe Repository von http://repo.mailserver.guru heruntergeladen werden:
# wget http://repo.mailserver.guru/7/os/x86_64/Packages/mailserver.guru-7-2.noarch.rpm --2015-04-30 17:09:52-- http://repo.mailserver.guru/7/os/x86_64/Packages/mailserver.guru-7-2.noarch.rpm Resolving repo.mailserver.guru (repo.mailserver.guru)... 217.91.103.190 Connecting to repo.mailserver.guru (repo.mailserver.guru)|217.91.103.190|:80... connected. HTTP request sent, awaiting response... 200 OK Length: 5712 (5.6K) [application/x-rpm] Saving to: \u2018mailserver.guru-7-2.noarch.rpm\u2019 100%[======================================>] 5,712 --.-K/s in 0.003s 2015-04-30 17:09:52 (1.72 MB/s) - \u2018mailserver.guru-7-2.noarch.rpm\u2019 saved [5712/5712]
Mit nachfolgendem Befehl, kann nun die Installation des rpm-Pakets für das externe Repository von http://repo.mailserver.guru durchgeführt werden:
# yum localinstall /tmp/mailserver.guru-7-2.noarch.rpm Loaded plugins: fastestmirror Examining /tmp/mailserver.guru-7-2.noarch.rpm: mailserver.guru-7-2.noarch Marking /tmp/mailserver.guru-7-2.noarch.rpm to be installed Resolving Dependencies --> Running transaction check ---> Package mailserver.guru.noarch 0:7-2 will be installed --> Finished Dependency Resolution Dependencies Resolved ================================================================================ Package Arch Version Repository Size ================================================================================ Installing: mailserver.guru noarch 7-2 /mailserver.guru-7-2.noarch 2.1 k Transaction Summary ================================================================================ Install 1 Package Total size: 2.1 k Installed size: 2.1 k Is this ok [y/d/N]: y Downloading packages: Running transaction check Running transaction test Transaction test succeeded Running transaction Installing : mailserver.guru-7-2.noarch 1/1 Verifying : mailserver.guru-7-2.noarch 1/1 Installed: mailserver.guru.noarch 0:7-2 Complete!
Mit nachfolgendem Befehl kann überprüft werden, welcher Inhalt mit dem Paket installiert wurde.
Paket mailserver.guru-7-2.noarch:
# rpm -qil mailserver.guru.noarch Name : mailserver.guru Version : 7 Release : 2 Architecture: noarch Install Date: Thu 30 Apr 2015 05:11:03 PM CEST Group : System Environment/Base Size : 2177 License : GPLv2 Signature : RSA/SHA1, Fri 20 Feb 2015 10:15:07 AM CET, Key ID 60ecfb9e8195aea0 Source RPM : mailserver.guru-7-2.src.rpm Build Date : Fri 20 Feb 2015 10:14:55 AM CET Build Host : vml000200.dmz.nausch.org Relocations : (not relocatable) Packager : Django <django@mailserver.guru> Vendor : django, http://dokuwiki.nausch.org/ URL : http://repository.nausch.org/public/mailserver.guru/ Summary : Extra (Mailserver-)Packages for CentOS 7 repository configuration Description : This package contains the Extra (Mailserver-)Packages for CentOS 7 repository GPG key as well as configuration for yum and up2date. /etc/pki/rpm-gpg/MAILSERVER.GURU-RPM-GPG-KEY-CentOS-7 /etc/yum.repos.d/mailserver.guru.repo

Zur Sicherheit sollte jedoch noch der GPG-Schlüssel des externen Repositories von http://repo.mailserver.guru importiert werden, da alle Pakete via GPG-Schlüssel signiert sind, und diese Signatur nur dann überprüft werden kann!
Nachfolgender Befehl lädt den GPG-Schlüssel des externen Repositories von http://repo.mailserver.guru von
herunter:
# wget http://repo.mailserver.guru/7/MAILSERVER.GURU-RPM-GPG-KEY-CentOS-7 --2015-04-30 17:10:41-- http://repo.mailserver.guru/7/MAILSERVER.GURU-RPM-GPG-KEY-CentOS-7 Resolving repo.mailserver.guru (repo.mailserver.guru)... 217.91.103.190 Connecting to repo.mailserver.guru (repo.mailserver.guru)|217.91.103.190|:80... connected. HTTP request sent, awaiting response... 200 OK Length: 1650 (1.6K) Saving to: \u2018MAILSERVER.GURU-RPM-GPG-KEY-CentOS-7\u2019 100%[======================================>] 1,650 --.-K/s in 0s 2015-04-30 17:10:42 (123 MB/s) - \u2018MAILSERVER.GURU-RPM-GPG-KEY-CentOS-7\u2019 saved [1650/1650]
Mit nachfolgendem Befehl, kann nun der GPG-Schlüssel des externen Repositories von http://repo.mailserver.guru importiert werden:
# rpm --import /tmp/MAILSERVER.GURU-RPM-GPG-KEY-CentOS-7

Um das Importieren des GPG-Schlüssels zu überprüfen, kann nachfolgender Befehl verwendet werden, welcher ebenfalls nachfolgende Ausgabe erzeugen sollte. (Der als erstes aufgelistete GPG-Schlüssel, sollte hinzugekommen sein!):
# rpm -qa gpg-pubkey gpg-pubkey-8195aea0-53cc3764 gpg-pubkey-f4a80eb5-53a7ff4b
Der Inhalt des importierten GPG-Schlüssels, kann mit nachfolgendem Befehl überprüft werden:
# rpm -qi gpg-pubkey-8195aea0-53cc3764 Name : gpg-pubkey Version : 8195aea0 Release : 53cc3764 Architecture: (none) Install Date: Fri 10 Oct 2014 10:25:02 AM CEST Group : Public Keys Size : 0 License : pubkey Signature : (none) Source RPM : (none) Build Date : Sun 20 Jul 2014 11:40:52 PM CEST Build Host : localhost Relocations : (not relocatable) Packager : Django <django@mailserver.guru> Summary : gpg(Django <django@mailserver.guru>) Description : -----BEGIN PGP PUBLIC KEY BLOCK----- Version: rpm-4.11.1 (NSS-3) mQINBFPMN2QBEAC2h7LGlcWQoLQMFsq5bJxI7H+/iGeAgR0IclE3wbg8oIDvCENT z3p6TnigowkJWkNSeKgMSqJtHjEmCB853glf53s1ldGN+VVEUddqpN/8ao1ua6Kl C9zDkzw0h8o3iIlhbwIilXk3qPaXyWazsnV/6PlRLgMB7T5jDMi6DC+hgx9FGe6H 1G5MzzKlfoV3PBY2AB4Tiplx8z1Wb0OtOoTsWKy6RSlWAkcznDOOl6uqtYbCj0eX g+Gs/ExVRN4ETmN7IWKwDTJIneg9ttT1D8u903CbmbESCfkTszn8i/8h8ELky3bU c5XzqPXJPeS3J+fAcZlfGlpzQp/BqBGtUFUUiKMof7YXrOwC8OEVeRifLxN+iGB6 LtpjguLWjs4xEoVs+dFGdKYI6HqsypcinguLwwovwWQsuQ5j8iVwHWkzb0lUUhHK ORl4NdP1OJkwn7IG4h+49f2+eVQyjXCAewi2KLygQZTh1w7QFIA41+ld5SDju9oD SSYM1ohOk0018R9UKFIpKayJBZzwm0X0qGLgcSmoZ+XbfXSv5qD47u52EswELqQt va24r44I0AVL5jUQ93HWyHklxnoEU9hCvYCe8KpBBi0he1Oo5gsTb+qp+SXzmkFl PTbMYBiw4oW8dGgMqkTQcVbJWh4Dhw/ILHfRMNPfPmFM7GElxJUkL3oDPwARAQAB tB9EamFuZ28gPGRqYW5nb0BtYWlsc2VydmVyLmd1cnU+iQI5BBMBAgAjBQJTzDdk AhsDBwsJCAcDAgEGFQgCCQoLBBYCAwECHgECF4AACgkQYOz7noGVrqB2sw//UbWC viCKPDRy2asxMHgiNB8hzsNrff7p9TbWRiTepZTF1RB0Txp1N8EZVaZTBSnavtFw 2RUw3XKI7ltL2KHNNJa+rY1m7QM4vYlTOylEv4CujePoeXcJWXKjiUSdJjDbybNh TePrkeOJCidS1tWisNvyh7pMzSLYeGDTIeqYZl6xoGHmMdGAGEXz3ESB/NvoYk09 1TLr6L+hRhqLrzn5VWmYEljYQL4PxI1XtPip+zbMYob/13XM4tb+r0XySeR2b3AI UdgVBM1+h1VsMOML4RgGu1QVbDlWghdGcZfF/ITumJOxVkGODHeLZmZn6HjsNJ7x 0u6jVK0qbXLmo6ANgOnNHelZY3xO44loUvCu0taXwPfB55fzgjvWwsKXvFFvunyZ EjuSCXiaHHEtqPDj21RIern1Yy+Ko+tafIQl6oHsApCZZRBW+VzNIvmBDhd52c2Z wmYUi6V+NL3BVxkfDIBzjkkhuPrj6kPGCGT3GWN0tv3KgQllxhORlc/qOFwYAFz0 Zus/Gh9AasXTz83wKUQY+1GtzOKk+V1WaWUxeUKEeDjOKQJTLHlQLviYw5uDxsxV 5OJEnbCbHuPrx8T08H+T/iu0WRk1lnd7LozAkdsRM8vYPDgUggD9VCeJmE+BV/MF EHhcxhsjHIkWCx2QnE04nRwERm7J1QfSvf8Y0mo= =YVGl -----END PGP PUBLIC KEY BLOCK-----
Jetzt kann das externe Repository von http://repo.mailserver.guru genutzt werden.
Es sollten mit nachfolgendem Befehl die von yum, dem Paket-Manager von CentOS, bereits zwischengespeicherten Informationen, welche bei der Nutzung von yum zu einem früheren Zeitpunkt ermittelt wurden, mit nachfolgenden Befehl gelöscht werden, um eine Neuermittlung aller verfügbaren Paketinformationen durchzuführen:
# yum clean all Loaded plugins: fastestmirror Cleaning repos: base extras mailserver.guru updates Cleaning up everything Cleaning up list of fastest mirrors
Eine Überprüfung, ob die Pakete verfügbar sind, kann durch eine Suche nach dem rpm-Paket
squidanalyzer
mit nachfolgendem Befehl durchgeführt werden:
# yum search squidanalyzer Loaded plugins: changelog, priorities 117 packages excluded due to repository priority protections ========================== N/S matched: squidanalyzer ========================== squidanalyzer.noarch : Squid proxy log analyzer and report generator Name and summary matches only, use "search all" for everything.
SquidAnalyzer - Installation
Zur Installation von SquidAnalyzer wird nachfolgendes Paket benötigt:
Zur Installation von SquidAnalyzer ist nachfolgender Befehl auszuführen:
# yum install squidanalyzer Loaded plugins: changelog, priorities 117 packages excluded due to repository priority protections Resolving Dependencies --> Running transaction check ---> Package squidanalyzer.noarch 0:6.6-1 will be installed --> Finished Dependency Resolution Changes in packages about to be updated: Dependencies Resolved ================================================================================ Package Arch Version Repository Size ================================================================================ Installing: squidanalyzer noarch 6.6-1 mailserver.guru-os 176 k Transaction Summary ================================================================================ Install 1 Package Total download size: 150 k Installed size: 452 k Is this ok [y/d/N]: y Downloading packages: squidanalyzer-6.6-1.noarch.rpm | 176 kB 00:00 Running transaction check Running transaction test Transaction test succeeded Running transaction Installing : squidanalyzer-6.6-1.noarch 1/1 Verifying : squidanalyzer-6.6-1.noarch 1/1 Installed: squidanalyzer.noarch 0:6.6-1 Complete!
Mit nachfolgendem Befehl, kann der Inhalt des Paketes - squidanalyzer aufgelistet werden:
# rpm -qil squidanalyzer Name : squidanalyzer Version : 6.6 Release : 1 Architecture: noarch Install Date: Tue 17 Oct 2017 08:51:45 AM CEST Group : Monitoring Size : 556888 License : GPLv3 Signature : RSA/SHA1, Mon 16 Oct 2017 04:45:42 PM CEST, Key ID 60ecfb9e8195aea0 Source RPM : squidanalyzer-6.6-1.src.rpm Build Date : Mon 16 Oct 2017 04:45:33 PM CEST Build Host : vml000137.dmz.nausch.org Relocations : (not relocatable) Packager : Django <django@mailserver.guru> URL : http://squidanalyzer.darold.net/ Summary : Squid proxy log analyzer and report generator Description : Squid proxy native log analyzer and reports generator with full statistics about times, hits, bytes, users, networks, top URLs and top domains. Statistic reports are oriented toward user and bandwidth control; this is not a pure cache statistics generator. SquidAnalyzer uses flat files to store data and doesn't need any SQL, SQL Lite or Berkeley databases. This log analyzer is incremental and should be run in a daily cron, or more often with heavy proxy usage. /etc/cron.d/squidanalyzer /etc/squidanalyzer/excluded /etc/squidanalyzer/included /etc/squidanalyzer/lang /etc/squidanalyzer/lang/ca_CA.txt /etc/squidanalyzer/lang/cs_CZ.txt /etc/squidanalyzer/lang/de_DE.txt /etc/squidanalyzer/lang/en_US.txt /etc/squidanalyzer/lang/es_ES.txt /etc/squidanalyzer/lang/fr_FR.txt /etc/squidanalyzer/lang/it_IT.txt /etc/squidanalyzer/lang/pl_PL.txt /etc/squidanalyzer/lang/pt_BR.txt /etc/squidanalyzer/lang/ru_RU.txt /etc/squidanalyzer/lang/uk_UA.txt /etc/squidanalyzer/network-aliases /etc/squidanalyzer/squidanalyzer.conf /etc/squidanalyzer/user-aliases /usr/bin/squid-analyzer /usr/share/doc/squidanalyzer-6.6 /usr/share/doc/squidanalyzer-6.6/ChangeLog /usr/share/doc/squidanalyzer-6.6/INSTALL /usr/share/doc/squidanalyzer-6.6/README /usr/share/doc/squidanalyzer-6.6/TODO /usr/share/man/man3/SquidAnalyzer.3pm.gz /usr/share/perl5/vendor_perl/SquidAnalyzer.pm /var/www/html/squidanalyzer /var/www/html/squidanalyzer/LICENSE /var/www/html/squidanalyzer/README /var/www/html/squidanalyzer/flotr2.js /var/www/html/squidanalyzer/images /var/www/html/squidanalyzer/images/back-arrow.png /var/www/html/squidanalyzer/images/cursor.png /var/www/html/squidanalyzer/images/domain.png /var/www/html/squidanalyzer/images/info.png /var/www/html/squidanalyzer/images/logo-squidanalyzer.png /var/www/html/squidanalyzer/images/network.png /var/www/html/squidanalyzer/images/up-arrow.png /var/www/html/squidanalyzer/images/user.png /var/www/html/squidanalyzer/sa-sorttable.diff /var/www/html/squidanalyzer/sorttable.js /var/www/html/squidanalyzer/squidanalyzer.css /var/www/html/squidanalyzer/squidanalyzer.js /var/www/html/squidanalyzer/update_rsc_files.sh
SquidAnalyzer - Konfiguration
Der erste Schritt zur Konfiguration beginnt mit dem anpassen der Konfigurationsdatei
/etc/squidanalyzer/squidanalyzer.conf
/etc/squidanalyzer/squidanalyzer.conf
Die Konfigurationsdatei /etc/squidanalyzer/squidanalyzer.conf könnte wie folgt aussehen:
#### # This file is the default configuration file for SquidAnalyzer # Edit it to match your needs and copy it under /etc/squidanalyzer/squidanalyzer.conf ##### # Path where SquidAnalyzer should dump all HTML and images files. # Choose a path that can be read by a Web browser Output /var/www/squidanalyzer # The URL of the SquidAnalyzer javascript, HTML and images files. # Tachtler # default: WebUrl /squidreport WebUrl / # Set the path to the Squid, squidGuard and/or ufdbGuard log files. LogFile /var/log/squid/access.log # If you want to use DNS name instead of client Ip address as username enable # this directive. When you don't have authentication, the username is set to # the client ip address, this allow you to use the DNS name instead. # Note that you must have a working DNS resolution and that it can really slow # down the generation of reports. UseClientDNSName 0 # If you have enabled UseClientDNSName and have lot of ip addresses that do # not resolve you may want to increase the DNS lookup timeout. By default # SquidAnalyzer will stop to lookup a DNS name after 0.0001 second (100 ms). DNSLookupTimeout 0.0001 # Set the file containing network alias name. Network are # show as Ip addresses so if you want to display name instead # create a file with this format : # LOCATION_NAME IP_NETWORK_ADDRESS # Separator must be a tabulation NetworkAlias /etc/squidanalyzer/network-aliases # Set the file containing user alias name. If you don't have auth_proxy # enable user are seen as Ip addresses, or if you want to replace login # name by full user name, create a file with this format : # FULL_USERNAME IP_ADDRESS || LOGIN_NAME # Separator must be a tabulation UserAlias /etc/squidanalyzer/user-aliases # How do we sort Network, User and user's Url report screen # Value can be: bytes, hits or duration. Default is bytes. OrderNetwork bytes OrderUser bytes OrderUrl bytes # How do we sort Mime types report screen # Value can be: bytes or hits. Default is bytes. OrderMime bytes # Should we display user URL details. This will show all URL read # by user. Take care to have enougth space disk for large user. UrlReport 1 # Enable this directive if you don't want the tree Top URL and Domain HTML tables. # You will just have the table of Url/Domain ordered per hits then you can still # sort the URL/Domain order by clicking on each column UrlHitsOnly 0 # Should we display user details. This will show statistics per user. UserReport 1 # Run in quiet mode or print debug information QuietMode 1 # Cost of the bandwidth per Mb. If you want to generate invoice per Mb # for bandwidth traffic this can help you. Value 0 mean no cost. # Tachtler # default: CostPrice 0.5 CostPrice 0.01 # Currency of the bandwidth cost Currency € # Top number of url to show from all url extracted from the log TopNumber 100 # Top number of url to preserve on each data file sorted by OrderUrl. # On huge access log it will improve a lot the performances but you # will have less precision in the top url. Default to 0, all url will # be stored. TopStorage 0 # Path to the file containing client ip addresses, network ip address, # and/or auth login to exclude from report Exclude /etc/squidanalyzer/excluded # Path to the file containing client ip addresses, network ip address, # and/or auth login to include into the report. Other entries will be # excluded by default. Include /etc/squidanalyzer/included # Translation Lang /etc/squidanalyzer/lang/en_US.txt, # en_US.txt, ru_RU.txt, uk_UA.txt, cs_CZ.txt, pl_PL.txt and de_DE.txt). # Default to: # Tachtler # default: #Lang /etc/squidanalyzer/lang/en_US.txt Lang /etc/squidanalyzer/lang/de_DE.txt # Date format used to display date (year = %y, month = %m and day = %d) # You can also use %M to replace month by its 3 letters abbreviation. DateFormat %y-%m-%d # Set this to 1 if you want to anonymize all user login. The username # will be replaced by an unique id that change at each squid-analyzer # run. Default disable. AnonymizeLogin 0 # Adds peer cache hit (CD_SIBLING_HIT) to be taken has local cache hit. # Enabled by default, you must disabled it if you don't want to report # peer cache hit onto your stats. SiblingHit 1 # Set the default unit for transfert size. Default is BYTES, other possible # values are KB, MB and GB TransfertUnit BYTES # Minimum percentage of data in pie's graphs to not be placed in the others item. MinPie 2 # Set this to your locale to display generated date in your language. Default # is to use strftime. If you want date in German for example, set it to de_DE. # For french, fr_FR should do the work. # Tachtler # default: #Locale en_US Locale de_DE # By default SquidAnalyzer is saving current collected statistics each time # a new hour is found in log file. Most of the time this is enough but if # you have huge log file and don't have enough memory this will slow down the # parser by forcing Perl to use temporaries files. Use lower value following # your memory and the size of your log file, on very huge log file with lot of # requests/seconde a value of 30 minutes (1800) or less should help. WriteDelay 3600 # Use this directive to show the top N users that look at an URL or a domain. # Set it to 0 to disable this feature. TopUrlUser 10 # This directive allow you to replace the SquidAnalyze logo by your custom # logo. The default value is defined as follow: # <a href="$self->{WebUrl}"> # <img src="$self->{WebUrl}images/logo-squidanalyzer.png" title="SquidAnalyzer $VERSION" border="0"> # </a> SquidAnalyzer # Feel free to define your own header but take care to not break current design. #CustomHeader <a href="http://my.isp.dom/"><img src="http://my.isp.dom/logo.png" title="My ISP link" border="0" width="100" height="110"></a> My ISP Company # This directive allow exclusion of some unwanted methods in report statistics # like HEAD, POST, CONNECT, etc. Can be a comma separated list of methods. #ExcludedMethods HEAD # This directive allow exclusion of some unwanted mimetypes in report statistics # like text/html, text/plain, or more generally text/*, etc. Can be a comma separated # list of perl regular expression. #ExcludedMimes text/.*,image/.* # This directive allow exclusion of some unwanted codes in report statistics # like TCP_DENIED/403 which are generated when a user accesses a page the first # time without authentication. Can be a comma separated list of methods. #ExcludedCodes TCP_DENIED/403 # When SquidAnalyzer find a corrupted line in his data file, it exit immedialtly. # You can force him to wait for a certain amount of errors before exiting. Of # course you might want to remove the corrupted line before the next run. This # can be useful if you have special characters in some fields like mime type. #MaxFormatError 0 # Set timezone to use when SquidAnalyzer is used in a different server than # the one running squid and there is a different timezone between these two # machine. The value must follow format: +/-HH. Default is to use local time. #TimeZone +01 # Enable this directive if you want to include port number into Url statistics. # Default is to remove the port information from the Url. #UseUrlPort 0 # Enable this directive if you want to apply immedialtly the changes made in # aliases files to avoid duplicates. You still have to use --rebuild to # recreate previous reports with new aliases. Enabling this will imply a lost # of performances with huges log files. #UpdateAlias 0 # The two following configuration directive allow you to specify a start and # stop time. Log line out of this time range will not be parsed. #TimeStart 00:00 #TimeStop 23:59
/etc/squidanalyzer/excluded
Die Konfigurationsdatei /etc/squidanalyzer/excluded könnte wie folgt aussehen:
#------------------------------------------------------------------------------ # File used to defined which client ip address, network with netmask, network # regex address, auth login and URI to exclude from the report. # # You can define one by line exclusion by specifying first the type of the # exclusion (USER, CLIENT or URI) and a space separated list of valid regex. # You can also use the NETWORK type to define network address with netmask # using the CIDR notation: xxx.xxx.xxx.xxx/n # # See example below: #------------------------------------------------------------------------------ #NETWORK 192.168.1.0/24 10.10.0.0/16 #CLIENT 192\.168\.1\.2 #CLIENT 10\.169\.1\.\d+ 192\.168\.10\..* #USER myloginstr #USER guestlogin\d+ guestdemo #URI http:\/\/myinternetdomain.dom.* #URI .*\.webmail\.com\/.*\/login\.php.* # Tachtler USER root
/etc/squidanalyzer/included
Die Konfigurationsdatei /etc/squidanalyzer/included könnte wie folgt aussehen:
#------------------------------------------------------------------------------ # File used to defined which client ip address, network with netmask, network # regex address, auth login and URI to include in the report. All other entries # will be exclude, this is the opposite of the excluded file. # # You can define one by line inclusion by specifying first the type of the # inclusion (USER or CLIENT) and a space separated list of valid regex. # You can also use the NETWORK type to define network address with netmask # using the CIDR notation: xxx.xxx.xxx.xxx/n # # See example below: #------------------------------------------------------------------------------ #NETWORK 192.168.1.0/24 10.10.0.0/16 #CLIENT 192\.168\.1\.2 #CLIENT 10\.169\.1\.\d+ 192\.168\.10\..* #USER myloginstr #USER guestlogin\d+ guestdemo
/etc/squidanalyzer/network-aliases
Die Konfigurationsdatei /etc/squidanalyzer/network-aliases könnte wir folgt aussehen:
#------------------------------------------------------------------------------- # Squid Analyzer Network Alias configuration file # FORMAT: NETWORK_NAME NETWORK_REGEX1,NETWORK_REGEX2,... # Field separator must be one or more tabulation. # You can also use the CIDR notation: # FORMAT: NETWORK_NAME xxx.xxx.xxx.xxx/n # # See examples below. # #------------------------------------------------------------------------------- #Home Network 192\.168\.1\. #Associated Networks ^10\.169\.[2-4]\.,^10\.169\.[7-9]\. #ClassB Network 10.172.0.0/16 #ClassC Network 192.168.1.0/24 # Tachtler EDMZ 88\.217\.171\.167 XDMZ 192\.168\.1\. DMZ 192\.168\.0\. INTRA 192\.168\.2\.
/etc/squidanalyzer/user-aliases
Die Konfigurationsdatei /etc/squidanalyzer/user-aliases könnte wir folgt aussehen:
#------------------------------------------------------------------------------- # Squid Analyzer User Alias configuration file # FORMAT : FULL_USER_NAME IP_ADDRESS|LOGIN_NAME,LOGIN_REGEX # Field separator must be one or more tabulation. Space in user are allowed. # See example below #------------------------------------------------------------------------------- #MyFirstName mylogin,192.168.1.12 #MyOtherNames logon\d+ # Tachtler Klaus Tachtler klaus
SquidAnalyzer - cron-job
Unter nachfolgendem Verzeichnis mit nachfolgendem Namen
/etc/cron.daily/0squidanalyzer
ist ein cron-Job installiert worden, welcher nachfolgenden Inhalt aufweist:
#!/bin/sh /usr/bin/squid-analyzer
Um den cron-Job von täglich auf stündlich zu verändern, kann dieser cron-Job mit nachfolgendem Befehl
- vom Verzeichnis -
/etc/cron.daily/ - in das Verzeichnis -
/etc/cron.hourly/
kopiert werden, um eine stündliche Ausführung zu realisieren:
# mv /etc/cron.daily/0squidanalyzer /etc/cron.hourly/
SquidAnalyzer - Test
Um das Perl-Script testweise einmalig händisch auszuführen, kann nachfolgendem Befehl zur Anwendung kommen:
# /usr/bin/squid-analyzer /var/log/squid/access.* Compute and dump year statistics for 2015 DEBUG: the log statistics gathering took: 1 wallclock secs ( 0.13 usr 0.03 sys + 0.02 cusr 0.02 csys = 0.20 CPU) DEBUG: generating HTML output took: 0 wallclock secs ( 0.20 usr + 0.04 sys = 0.24 CPU) DEBUG: total execution time: 1 wallclock secs ( 0.33 usr 0.07 sys + 0.02 cusr 0.02 csys = 0.44 CPU)
Nach der Ausführung des oben genannten Befehls, kann mit nachfolgendem Befehl, die korrekte Erstellung der benötigten Komponenten des SquidAnalyzer überprüft werden:
VORHER:
# ls -la /var/www/squidanalyzer/ total 128 drwxr-xr-x 3 root root 78 May 2 09:05 . drwxr-xr-x. 6 root root 63 May 2 08:15 .. -rw-r--r-- 1 root root 102194 Apr 30 17:17 flotr2.js drwxr-xr-x 2 root root 138 May 2 08:15 images -rw-r--r-- 1 root root 17262 Apr 30 17:17 sorttable.js -rw-r--r-- 1 root root 7604 Apr 30 17:17 squidanalyzer.css
NACHHER:
# ls -la /var/www/squidanalyzer/ total 140 drwxr-xr-x 4 root root 134 May 2 09:08 . drwxr-xr-x. 6 root root 63 May 2 08:15 .. drwxr-xr-x 11 root root 4096 May 2 09:08 2015 -rw-r--r-- 1 root root 102194 Apr 30 17:17 flotr2.js drwxr-xr-x 2 root root 138 May 2 08:15 images -rw-r--r-- 1 root root 3008 May 2 09:08 index.html -rw-r--r-- 1 root root 17262 Apr 30 17:17 sorttable.js -rw-r--r-- 1 root root 7604 Apr 30 17:17 squidanalyzer.css -rw-r--r-- 1 root root 20 May 2 09:08 SquidAnalyzer.current
Apache VHOST für SquidAnalyzer
Nachstehend soll ein möglicher virtueller Host welcher unter dem Apache HTTP Server realisiert werden kann für den Web-Anwendungsbereich des SquidAnalyzer als Beispiel dargestellt werden.

- ALT:
/var/www/squidanalyzer
auf
- NEU:
/var/www/html/squidanalyzer
geändert!
Deshalb kann
- a.) Der VHOST entsprechend angepasst werden
- b.) Der Inhalt von
/var/www/html/squidanalyzernachvar/www/squidanalyzerkopiert werden.
Nachfolgender Befehl kopiert bzw. hier verschiebt alle Dateien vom Verzeichnis /var/www/html/squidanalyzer in das Verzeichnis /var/www/squidanalyzer:
# cp -ar /var/www/html/squidanalyzer/* /var/www/squidanalyzer # rm -rf /var/www/html/squidanalyzer
Nachfolgende Konfigurationsdatei in nachfolgendem Verzeichnis und mit nachfolgendem Namen
/etc/httpd/conf.d/squidanalyzer.conf
könnte wie folgt realisiert werden:
# # squidanalyzer.tachtler.net (SquidAnalyzer) # <VirtualHost _default_:80> ServerAdmin webmaster@tachtler.net ServerName squidanalyzer.tachtler.net ServerAlias www.squidanalyzer.tachtler.net ServerPath / DocumentRoot "/var/www/squidanalyzer" <Directory "/var/www/squidanalyzer"> Options -Indexes +FollowSymLinks # Tachtler (enable for .htaccess file support) # AllowOverride AuthConfig AllowOverride None # Tachtler (enable for unlimited access) Require all granted </Directory> DirectoryIndex index.html ErrorLog logs/squidanalyzer_error.log CustomLog logs/squidanalyzer_access.log combined </VirtualHost>
Ein Aufruf kann dann über die URL http://www.squidanalyzer.tachtler.net erfolgen!
e2guardian-Konfiguration
Falls der Squid Proxy-Server hinter einem E2guardian Content-Filter betrieben wird, ist die Ermittlung der tatsächlichen IP-Adresse eines anfragenden Clients mit den Einstellungen unter nachfolgendem internen Link
ZWINGEND erforderlich, da sonst der Squid Proxy-Server NUR die IP-Adresse des E2guardian Content-Filters mitgeteilt bekommen würde und so viele der auf einer IP-Adresse oder eines Netzwerks basierende ACL nicht greifen würden!
Zur Konfiguration des E2guardian Content Filter -Servers, kann nachfolgender interner Link genutzt werden: